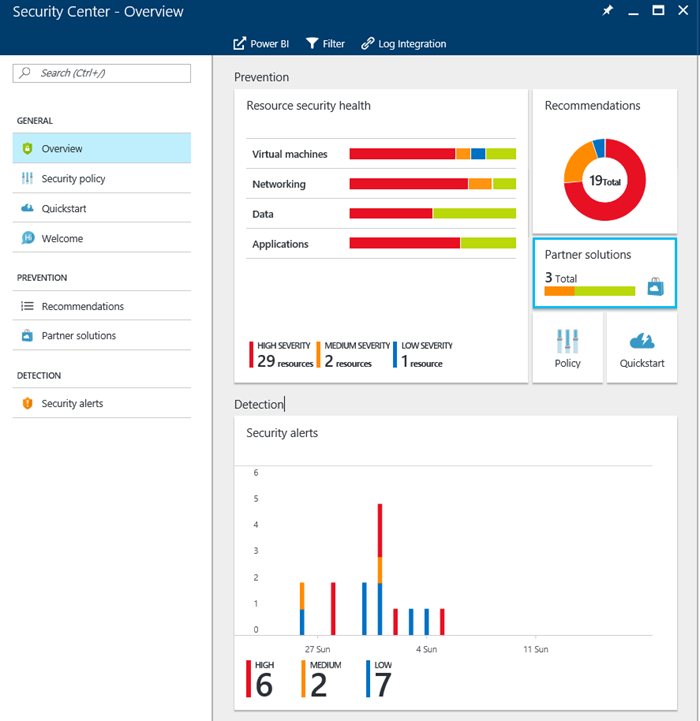
We’ve discussed in previous posts about Azure and the security topic as being one of the most critical ones for customers and therefore to Microsoft as well. Because of that, the Redmond based company has been including several new enhancements and features into Azure Security Center. One of the latest is the integrated vulnerability assessment.
The vulnerability assessment is nothing more than a recommendation within Azure Security Center, and currently this assessment is provided by Qualys on a subscription base (free trial available). You can enable the vulnerability assessment on VM basis by using an agent.
Some of the key features available in this vulnerability assessment are:
- Identify, classify and monitor assets and vulnerabilities
- Prioritize their remediation
- Comply with internal and external policies
- Automatically find and eradicate malware infections on your websites
Once deployed, Qualys agent will start reporting vulnerability data to the partner’s management platform which in turn, provides vulnerability and health monitoring data back to Azure Security Center.
Here’s a simple step-by-step to enable Azure’s vulnerability assessment within Security Center:
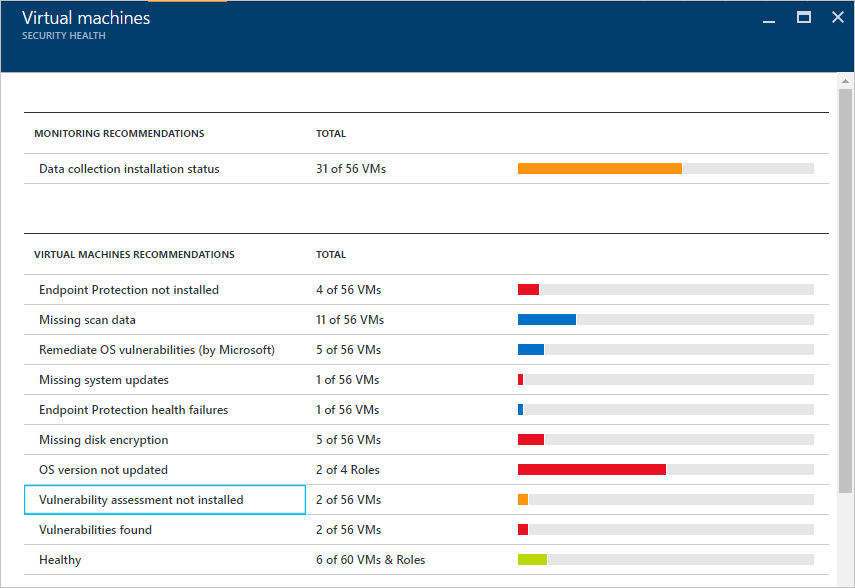
- In the Resource security health tile, click Virtual Machines.
- In the Virtual machines blade, select “Vulnerability assessment not installed”
- In the Add a vulnerability assessment solution – PREVIEW blade, select the VMs that you want to install the vulnerability assessment solution.
- In the Add a vulnerability assessment solution – PREVIEW blade, click Install on the VMs option and the Add Vulnerability Assessment blade appears:

- In this blade you can choose to create a new vulnerability assessment, which allows you to select a partner solution from Azure Marketplace or you can select an existing partner solution under use existing solution, in this case Qualys.
- The partner’s blade will open. The fields shown in this blade may change according to the partner, for this example using Qualys should show something like this:
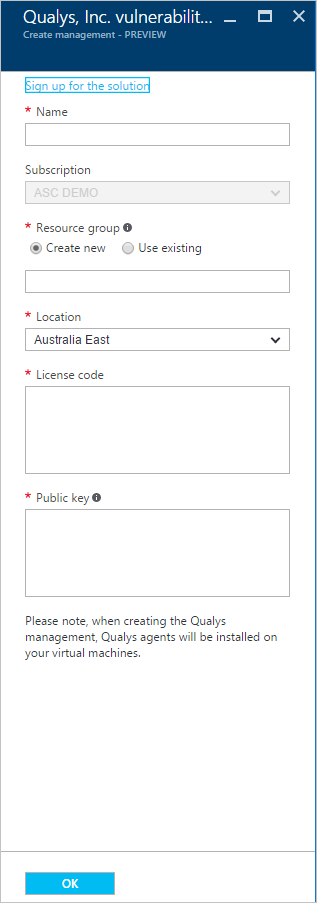
- Complete the information related to the subscription (you can use the free trial option here to add the license and public key).
- Once enabled, it is recommended to wait 12 hours until the agents have completed the analysis and are being able to inform back to Azure Security Center.
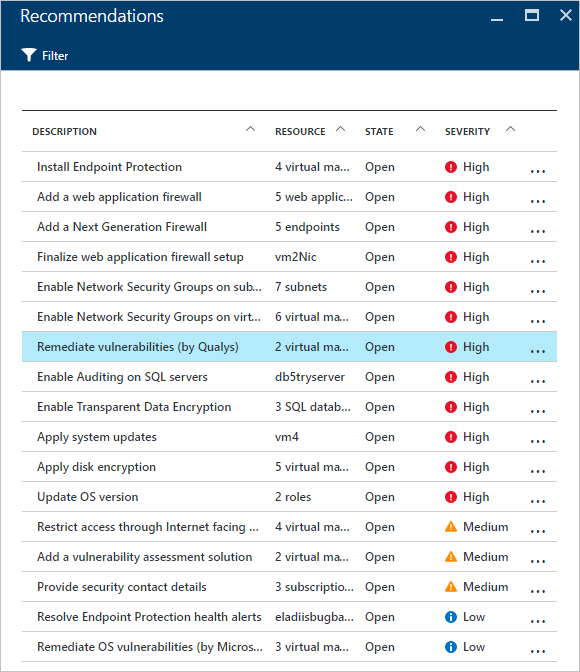
- These issues will be surfaced under the Virtual Machines Recommendations options.
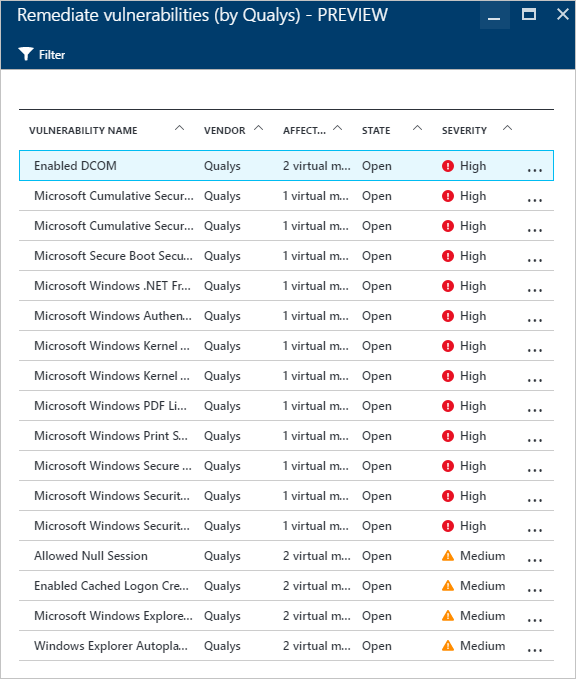
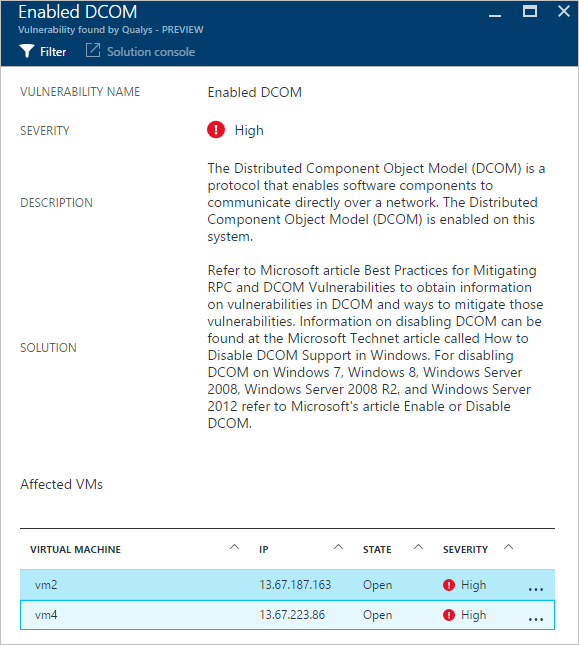
- Accessing to that selected recommendation shows that the detection was performed by Qualys. If you click on this recommendation, a new blade with a list of vulnerabilities will appear:
For this example, the vulnerability Enable DCOM was selected and a new blade appears with the recommended steps to address this vulnerability.
Related materials: