In our first article we have covered VMware ESXi host security and gave you some ideas on how to make them more secure and more resilient against ransomware. In that post we have talked about TPM, secure boot or lockdown mode and those tips are more than welcomed when seeking for securing your virtual environments.
Today we’ll cover a bit more and give you more tips to fight against ransomware. The fact that when your ESXi host is hit by ransomware, it seeks the datastores to which your host is connected and encrypts all the files residing on those datastores (including shared datastores of course).
You might have several ESXi versions running connected to shared datastores, and not all with the latest security patches. If any of those hosts get infected with ransomware, the VM’s files running on that shared datastores get encrypted.
It is much easier for the ransomware guys to target ESXi than each guest OS credentials to get into each Virtual machine (VM) individually.
ExecInstalledOnly Enforcement
You can enforce the security of the ESXi host by enabling to run only VMkernel binaries that have been packaged and signed as a part of a VIB.
A VIB is an ESXi software package. As you know, VMware and its partners package solutions, drivers, CIM providers, and applications that extend the ESXi platform as VIBs. VIBs are available in software depots. You can use VIBs to create and customize ISO images or to upgrade ESXi hosts by installing VIBs asynchronously onto the hosts.
If we check further details about a VIB, we can find that VIB has 3 parts:
- File Archive – the main file. The file which gets deployed to the ESXi host.
- XML descriptor file – has important info about requirements for installing the VIB. (dependencies, compatibility, reboot necessary, etc. )
- Signature File – a signature that verifies the level of trust (Integrity, Information about the creator, and verifications that have been done).
So basically, this security enforcement will disallow running any other code on the ESXi other than which comes from signed VIBs.
The ESXi security option needs to be configured as follows. You’ll have to set “execInstalledOnly” option to True.
This advanced option on the ESXi hosts allows you to disable the execution of custom code inside ESXi so the host will not execute anything that wasn’t installed through signed VIB from a certified vendor or partner.
The setting is when you log in to your ESXi > Manage >Advanced Settings
VMkernel.Boot.execInstalledOnly
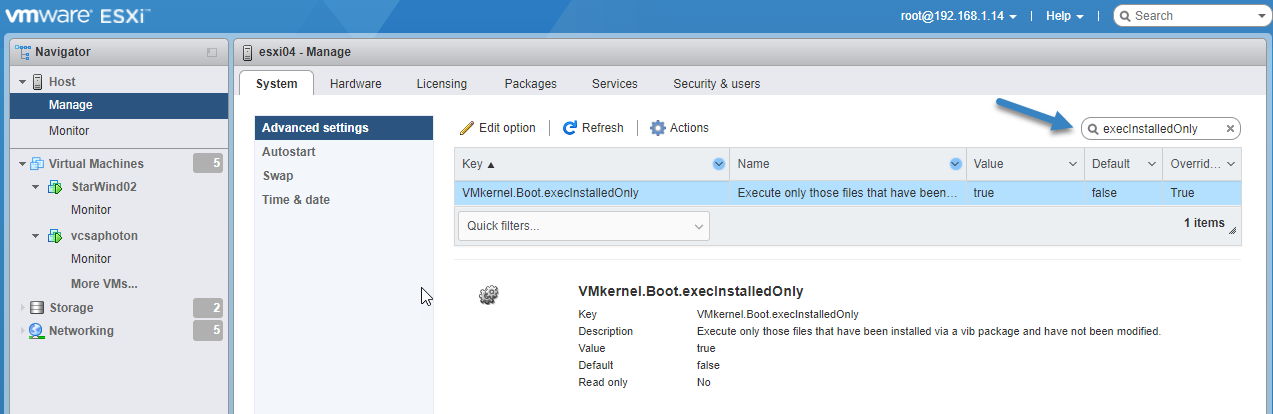
VMkernel Boot ExecInstalled Only
And then click the Edit Settings icon to change its value.
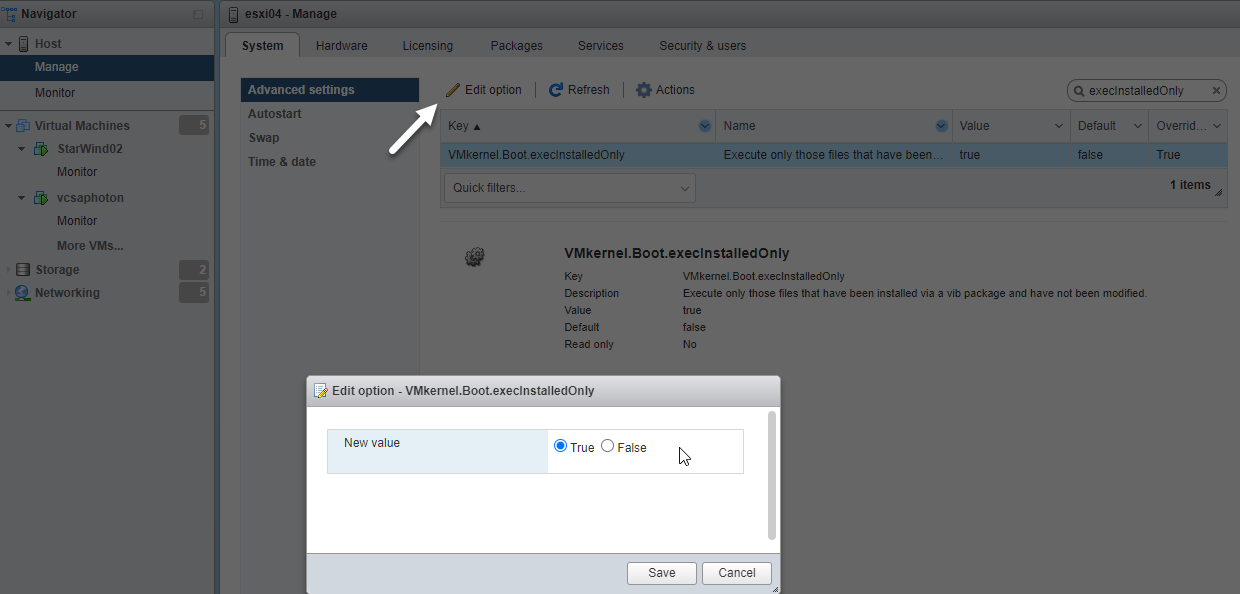
Change value of VMkernel Boot ExecInstalled Only
If you want to do the same for multiple ESXi hosts at a time, using PowerCLI might be a better option. The default setting of an ESXi host is that execInstalledOnly is set to FALSE. We can verify this by simply listing the setting:
|
1 |
<em>esxcli system settings kernel list -o execinstalledonly</em> |
And then with the option “set” and value TRUE to activate this option via this command:
|
1 |
<em>esxcli system settings kernel set -s execinstalledonly -v TRUE</em> |
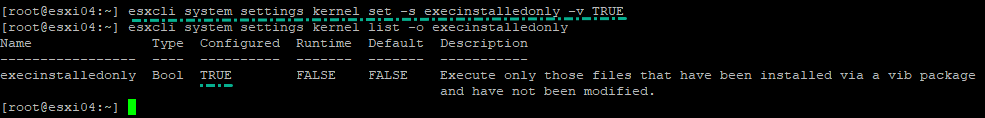
VMkernel.Boot.execInstalledOnly settings on your ESXi via CLI
You’ll need to reboot your host.
Change ESXi acceptance Level
If you ever changed the acceptance level of your ESXi (for example to install some community NIC drivers) you might be willing to revisit those settings. If you want to add a VIB with a low acceptance level to an image profile, you can change the image profile acceptance level. You can, but be aware of the security drawbacks.
The security settings to prevent the installation of unsigned VIBs can be found In Mange > Security and users > Acceptance Level > Edit Settings.
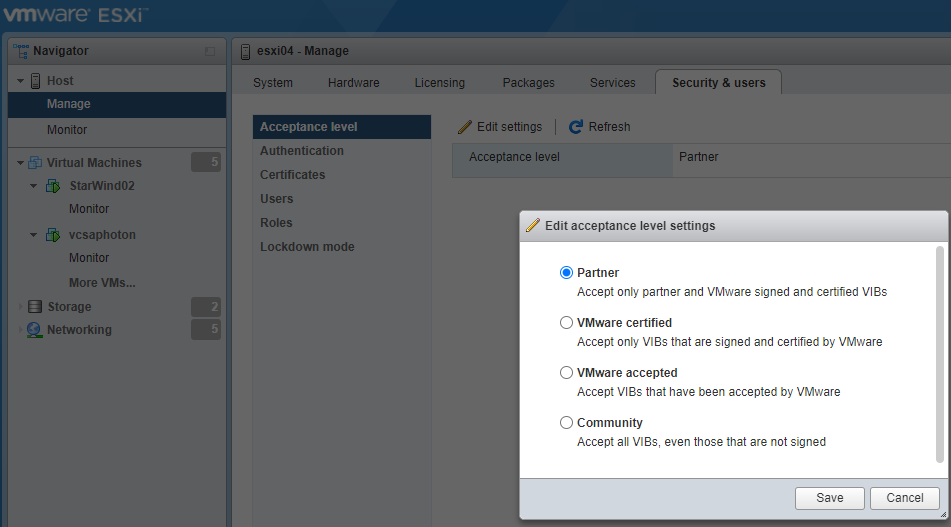
Edit Acceptance Level settings
This is to make sure that only certified VIBs run on that particular host. The acceptance level of the host depends on the level of the lowest VIB. If you want to allow lower-level VIBs, you can change the acceptance level of the host. You can remove CommunitySupported VIBs to be able to change the host acceptance level.
VMwareCertified – The most stringent requirements. VIBs go through thorough testing fully equivalent to VMware in-house Quality Assurance testing for the same technology.
VMwareAccepted – VIBs also go through verification testing, but the tests do not fully test every function of the software. CIM providers and PSA plug-ins are among the VIBs published at this level. VMware support however will direct you to the partner’s support organization, in case of any problems.
PartnerSupported – VIBs published by a partner that VMware trusts. The partner performs all testing, however, VMware does not verify the results. Usually, non-mainstream technology that partners want to enable for VMware systems. Technologies such as Infiniband, ATAoE, and SSD are at this level with nonstandard hardware drivers.
CommunitySupported – VIBs created by individuals or companies outside of VMware partner programs. VIBs at this level have not gone through any VMware-approved testing. Support only via the community at this level.
Set a central logging
If your ESXi host’s datastores get encrypted, even the logs get encrypted. If you want to keep track, you should set central logging. You can use the vSphere Client or the esxcli system syslog command to configure the syslog service.
Global syslog host
Other security tips
Microsoft AD and ESXi/VCSA separation – I’d separate ESXi and Microsoft Active Directory (AD). Even if we have the option to join ESXi to AD, keeping separation allows more security enforcement. Same idea for VMware vCenter server appliance. Imagine that your AD get’s compromised and you have your ESXi and VCSA joined to a domain. The attacker can possibly compromise the whole virtual environment if a proper separation is not at place.
Backups, backups, backups – Again and again, back up what you can, how many times you can. At least 2 copies of your backup on two different media. In total, you should have 3 backup files in 3 different locations. No matter which backup software from whichever vendor. Nowadays most of them are able to handle incremental backups and backup copies or VM replications. Even with the lowest cost VMware licensing packages you can get a hand or a product called VMware vSphere replication allowing you to set up replication of your business-critical VMs to another ESXi host located at another building/room with a local datastore. A pretty simple DR scenario.
Thoughts
As you can see, the choice is clear. If you want your security to become top-notch, you might want to get rid of some Non-standard ESXi boxes within your environment or at least disconnect them from shared datastores. If something happens to non-critical VMs on a local datastore of ESXi running a free version of ESXi it might not be important. But if the same (possibly non-patched) host will be connected to a shared datastore with production VMs and the host is hit by ransomware, then you might have a problem.
If you want to get more information, you can find it on this VMware Documentation page.




