Remote work isn’t going anywhere. With that in mind, the legacy means of provisioning services and enforcing policies and governance for end-users often fall short of standard in terms of remote workforce. Microsoft Intune Configuration Profiles attempts to provide an alternative for ensuring compliance when it comes to a hybrid work environment.
The current landscape of the hybrid remote workforce has forced businesses to change how they have traditionally supported users. Unfortunately, many companies can no longer use the legacy approaches to provisioning end-user clients and applying configuration policies and governance settings to them.
Traditionally, organizations have relied on Active Directory Group Policies to apply configuration settings for users and computers in the environment. However, organizations have shifted to modern cloud-based approaches such as using Microsoft Endpoint Manager to apply configuration policies with the hybrid workforce. Let’s look at Group Policy vs. Microsoft Intune Profiles and how you can migrate.
Group Policy
Microsoft Group Policy as part of Microsoft Active Directory has been the defacto standard for applying user and computer policies in the enterprise. Group Policy Objects (GPOs) are used to apply a myriad of settings, controlling configurations, settings, and functionality of end-user clients.
A Group Policy Object contains a set of configuration settings that can be applied at the user or computer level. By using GPOs, organizations can apply standardized and consistent policies to users and computers without low-level registry edits and inconsistent manual processes.
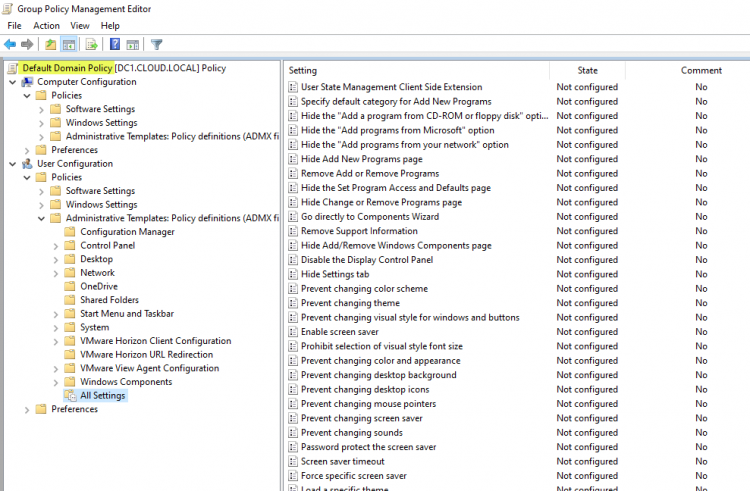
Group Policy Default Domain Policy viewed from a domain controller
However, controlling users and computers using Group Policy Objects is based in a world where all users and computers exist inside the walls of a corporate office building with all the assumed network connectivity that implies. Furthermore, all computers have “line of sight” access to domain controllers in this traditional architecture, meaning the ports and connectivity required for successfully applying GPOs in a Microsoft Active Directory network are available.
The challenge with the legacy Group Policy approach to managing end-user clients is the required network connectivity. As mentioned, if clients do not have direct line of sight connectivity to Active Directory domain controllers, Group Policy settings will fail to apply or refresh, depending on whether clients already have GPO settings applied or if they need to pull updated settings from the domain controller.
Providing connectivity for Group Policy
One option that organizations have used in the past with Group Policy and other core Windows services that need to have direct connectivity to the on-premises infrastructure. Connectivity can be achieved using virtual private network (VPN) connections. With VPN, the end-user client creates a secure tunnel back to the corporate network. It essentially allows the client to connect to the internal corporate network even when located on the Internet.
While VPN connections can allow clients to connect to the internal network and solve some of the challenges around direct connectivity to internal Windows and Active Directory infrastructure, they can create other challenges. These include management and security challenges. In addition, multiple VPN connections can become challenging to manage, and VPN connections are traditionally not known for the best network performance.
In addition to management and performance complexities, VPN connections can also lead to security concerns. While the VPN tunnel is encrypted and secure “between” the client and corporate network, it can lead to data exfiltration issues as it becomes easy for the user to copy data directly from the corporate network onto their end-user client. If an end-user client becomes infected with malware, including ransomware, VPN connections will essentially place that computer onto the corporate network, along with the malicious software.
Modern end-user client policy management
Over the past two years, with the shift to a remote workforce, organizations have quickly realized traditional end-user client management, including applying policies, no longer works as expected. In addition, the now majority remote workforce may be spread across any number of networks and geographic locations across the Internet. It means they no longer directly connect to the corporate network as they had previously worked onsite.
Now businesses are switching to a more modern approach to provisioning, managing, and applying policies to end-user clients. Modern management includes a cloud-based control and management plane approach. The end-user clients “phone home” to the cloud and receive configuration settings. The advantage of this model is the client needs Internet connectivity, and no special ports or other firewall considerations are needed since they communicate across the standard HTTPS SSL port 443.
Microsoft’s Endpoint Manager solution, specifically Microsoft Intune, provides a cloud-based solution, allowing businesses to manage end-user clients no matter where they are located. Within the Microsoft Endpoint Manager admin center, you will see a variety of configuration settings that can be applied to cloud-controlled end-user clients, including:
- Compliance policies – these are mainly used with conditional access to check a device for specific settings and determine if it meets the criteria for access, based on the “conditions” defined
- Conditional access – Conditional access works in harmony with the compliance policies to ensure the device meets certain “conditions” before it is granted access
- Configuration profiles – Configuration profiles are the most familiar to many IT admins since they have the same look and feel as traditional Group Policy Object (GPO) settings
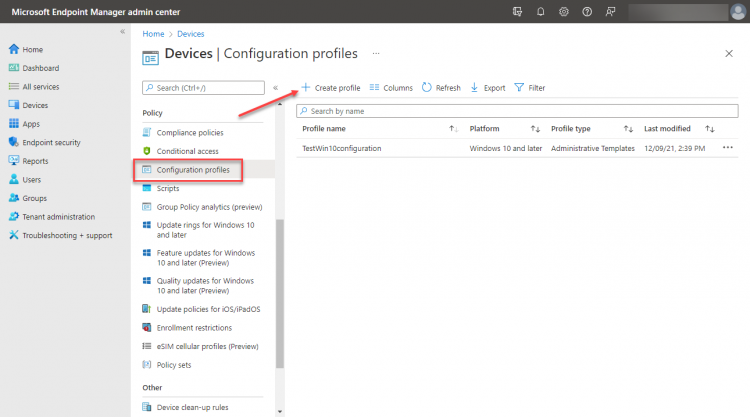
Viewing the device configuration profile blade in Microsoft Endpoint Manager admin center
Configuration profiles and the Configuration Service Provider (CSP)
If you read any of the documentation around the configuration profile, you will see a reference to the configuration service provider (CSP). So what is the configuration service provider? For those coming from a traditional on-premises Active Directory and Group Policy Object (GPO) environment, the CSP is like “client-side extensions” when working with Group Policy.
Client-side extensions are specialized DLL files that allow the end-user client to read and apply the Group Policy Object settings. With the cloud-based Intune configuration profile, the CSP allows reading, setting, modifying, or deleting configuration settings on a device. The CSP settings map to registry keys or files on the end-user client.
In addition to including client-side extensions that allow applying Group Policy settings, Windows 10 & 11 also contain the CSPs needed to use the configuration profiles defined by Microsoft Intune.
Group Policy vs. Microsoft Intune Profiles
It might seem like it would be a great idea to migrate from Group Policy to Microsoft Intune Profiles in all cases. However, that is unfortunately not true. Group Policy is still a compelling way to implement policy configurations on your end-user clients. In addition, it provides the most robust set of policies available, as many of the Group Policy settings are still not found in equivalent Microsoft Intune configuration profiles.
Additionally, Group Policy provides the fastest convergence time available for policy settings. Group Policy settings are refreshed by default on client computers every 90 minutes, with a randomized offset of plus or minus 30 minutes. Comparatively, Intune configuration profiles may take much longer and can be less predictable. Microsoft mentions, “the notification times vary, including immediately up to a few hours. These notification times also vary between platforms.”
Intune configuration profiles shine in the flexibility and control they offer to end-user clients outside the walls of the corporate environment. In addition, Intune configuration profiles eliminate the connectivity requirements and challenges that come with managing clients using traditional Group Policy settings. They allow organizations to ship end-users corporate-owned laptops or workstations, have those automatically provisioned when they come online, and apply the configuration profile settings assigned. This provisioning and governance workflow is not possible with traditional provisioning and Group Policy managed devices.
Microsoft has also come a long way in providing equivalent CSP settings for configuration profiles that match existing Group Policy settings found on-premises. However, as with any new technology, it takes time to achieve the feature parity of legacy solutions, so there is still work to do on that side of things.
Group Policy Analytics – Migrate to Microsoft Endpoint Manager and Intune
Suppose an organization wants to begin migrating from an on-premises/Group Policy management approach to the cloud-centric model of Microsoft Endpoint Manager and Intune. How can you determine if equivalent settings exist in the cloud? A great new tool is the Microsoft Group Policy Analytics tool.
The Group Policy analytics tool is a solution that analyzes your on-premises GPOs and helps determine how your GPO translates to the cloud-based settings found in Microsoft Endpoint Manager and Intune. In addition, it shows which settings are supported in Microsoft Intune’s MDM solution.
The steps to analyze GPOs are relatively straightforward. First, launch your Group Policy Management Console. Next, right-click the GPO you want to analyze and choose Save Report. Choose to save the report to an XML file instead of the default .htm file.
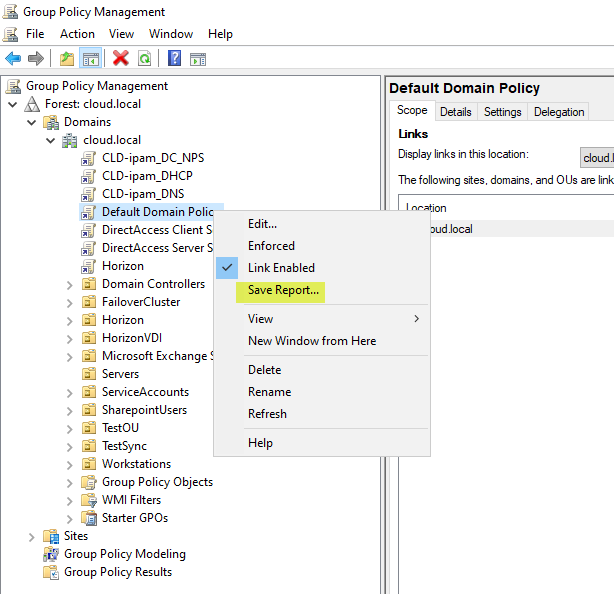
Saving a GPO report as an XML file
Log into your Microsoft Endpoint Manager admin center. Next, click the Group Policy analytics (preview) tool. Then click the Import button to import the .xml file created from your Group Policy Management Console above.
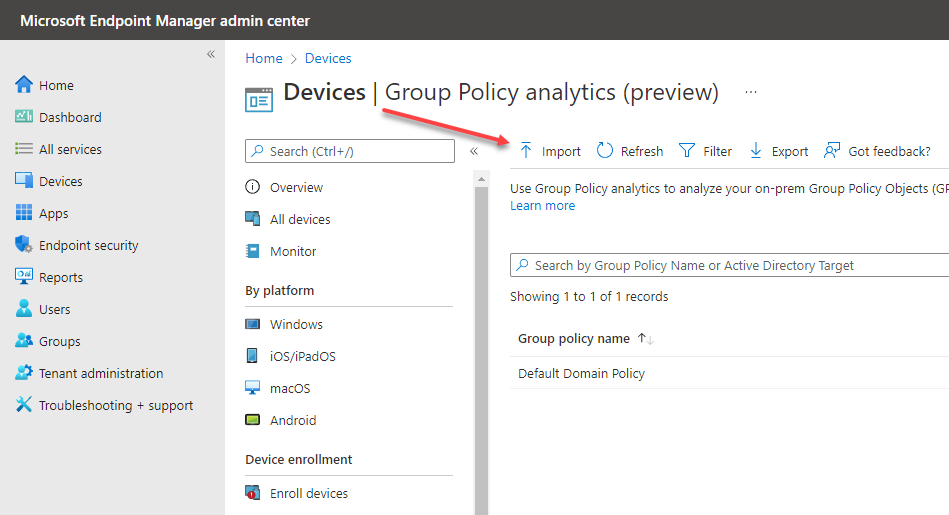
Import the file into Group Policy Analytics
After importing the XML file, the Group Policy analytics tool will examine the on-premises Group Policy settings and report which settings are supported for migration to the Intune MDM.
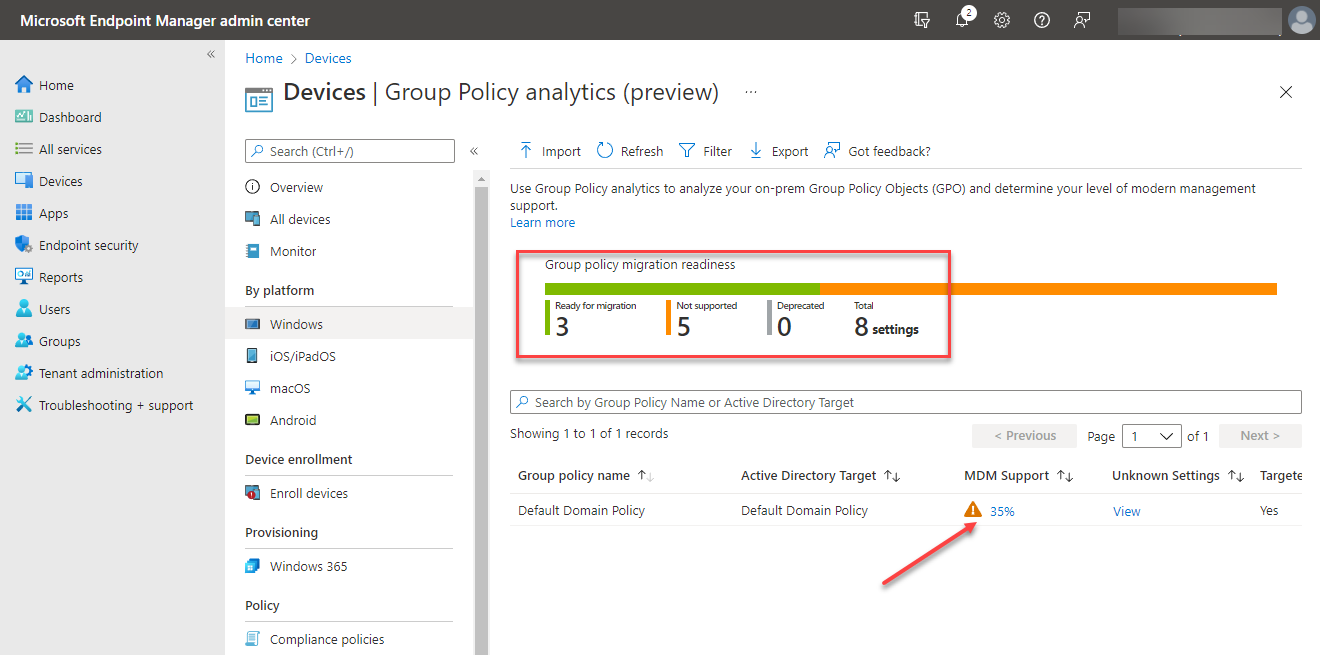
Group Policy Analytics report of compatible Group Policy settings
If you click the report’s details, you can see which specific settings are supported from Group Policy in Microsoft Intune, along with the specific CSP mapping. The Group Policy Analytics tool is a great way to have visibility to Group Policy settings that may not work with the Microsoft Intune MDM solution.
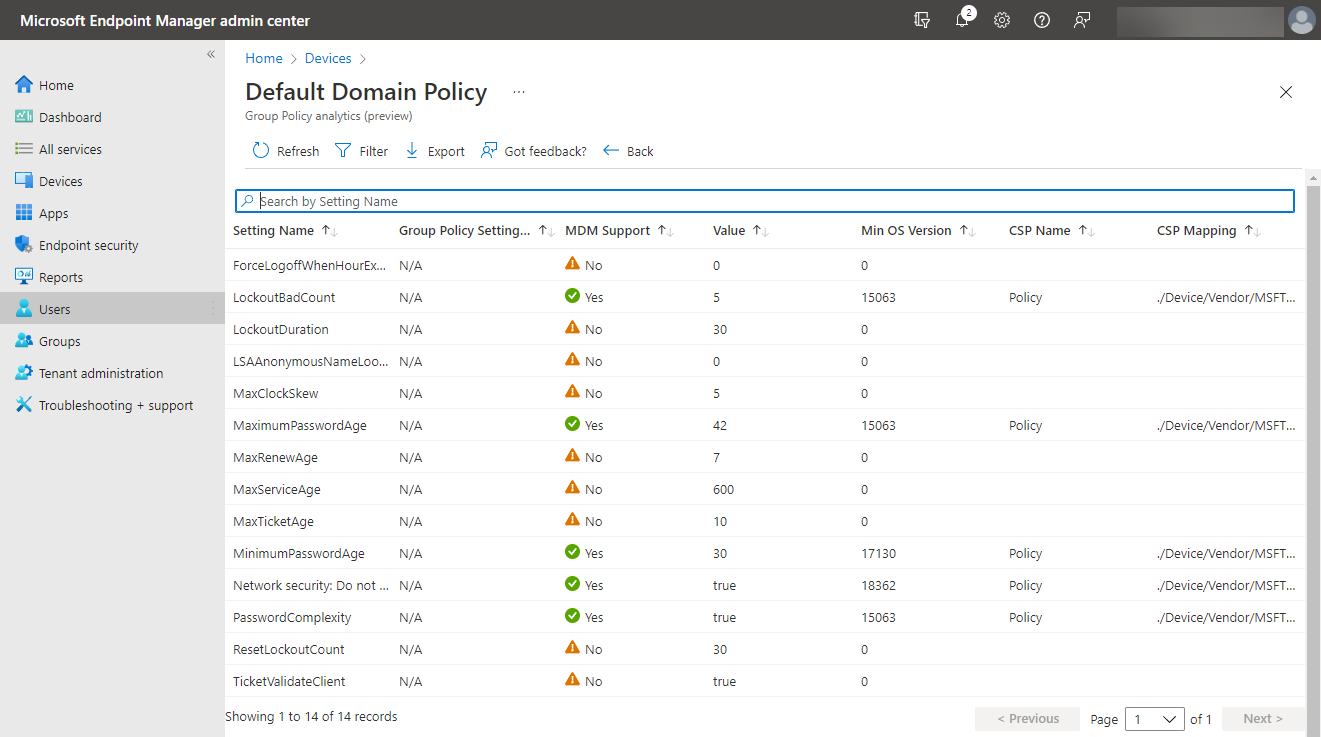
Group Policy Analytics report
Wrapping Up
Organizations are increasingly moving to a cloud-centric approach for managing end-user devices along with many other aspects of their IT infrastructure. The cloud revolution has proven beneficial with the hybrid remote workforce and easing the challenges of supporting end-user client devices and enforcing policies and governance controls.
However, there are considerations to be made as businesses look to move from legacy Group Policy configurations to modern Microsoft Intune-managed policies. There are still good use cases for maintaining Group Policy controls. Both Group Policy and Microsoft Intune configuration profiles have their strengths and weaknesses. Most likely, at this time, most businesses may choose to leverage a mix of both GPOs and cloud-based MDM management with solutions like Microsoft Intune. Microsoft is providing great tools like the Group Policy analytics tool to help ease the pain of migrating from GPOs to the CSP-based Microsoft MDM platform.




