Introduction
In October 2019, VMware acquired Carbon Black, a leading next-generation security cloud provider specializing in cloud-native endpoint protection platforms (EPP). This solution particularly detects threats on the workstation level, analyzes them on the cloud level, and eventually takes necessary steps to protect the enterprise desktop infrastructure. That is not just an antivirus or a firewall, but a complex system for monitoring network connections and applications performing suspicious activities.
Basically, it doesn’t matter to this solution whether we’re talking zero-day threats or deeply customized attacks, specifically tailored for a particular enterprise.
The thing is, this acquisition seems to be working out for everybody: before, you would have required a separate agent (lightweight agent, but still) for Carbon Black to work; now, all you need is VMware Tools, which means that you can leave all this agent deployment and support headache behind. Needless to say, VMware has had quite a good deal by paying only two and a half billion dollars.
Let’s Talk Details
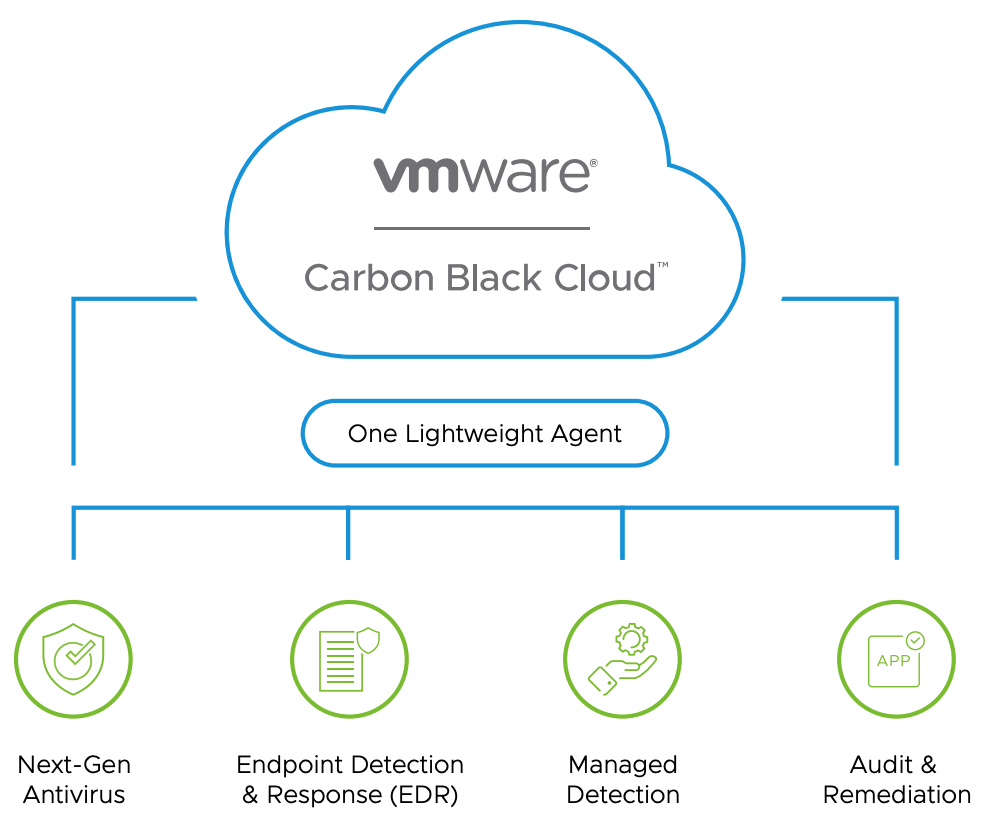
It’s time to take a look under the hood and figure out how this all works. Primarily, Carbon Black solution is meant to be used in these four directions:
- Antivirus protection;
- To detect and stop never-seen-before attacks using proactive protection methods (Endpoint Detection and Response);
- Detecting new threats 24/7 with Managed Detection: a team of skilled security professionals, analyzing the source of a threat, and validating it along with monthly reports – it’s all on the table;
- A system audit to recognize potentially dangerous configurations and be ahead of the curve.
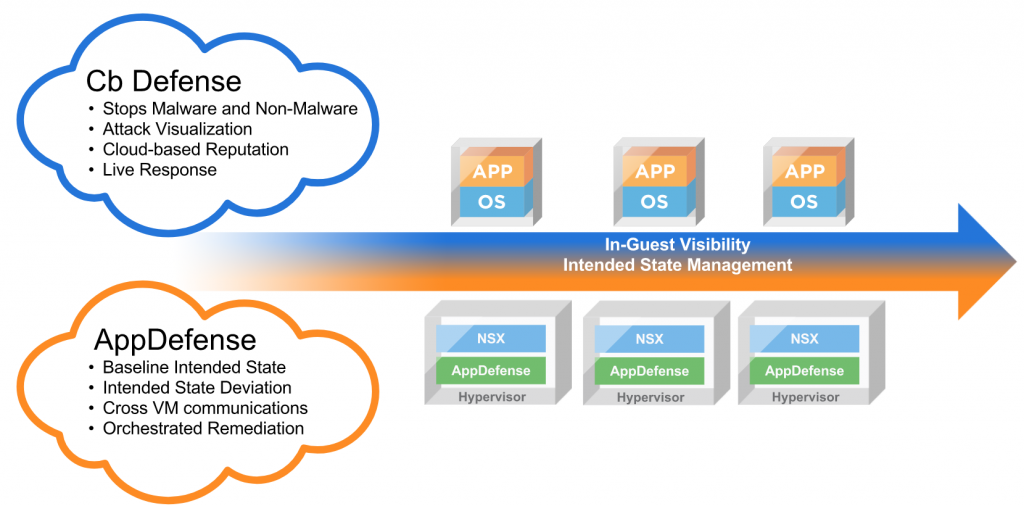
I know, I know. VMware seems to have a similar solution; after all, AppDefense has been around for some time. There’s only one tiny difference that makes all difference in the world: AppDefense is based on the positive security model, and Carbon Black is based on the negative one. What does it mean?
AppDefense is monitoring applications to detect any anomalies and deviations from «good» behavior. At the same time, Carbon Black is focused on «bad» behavior of any application to identify the threat, determine its cause, and seize it. You shouldn’t forget that AppDefense is working on the ESXi level, and Carbon Black is working on a guest OS level, too:
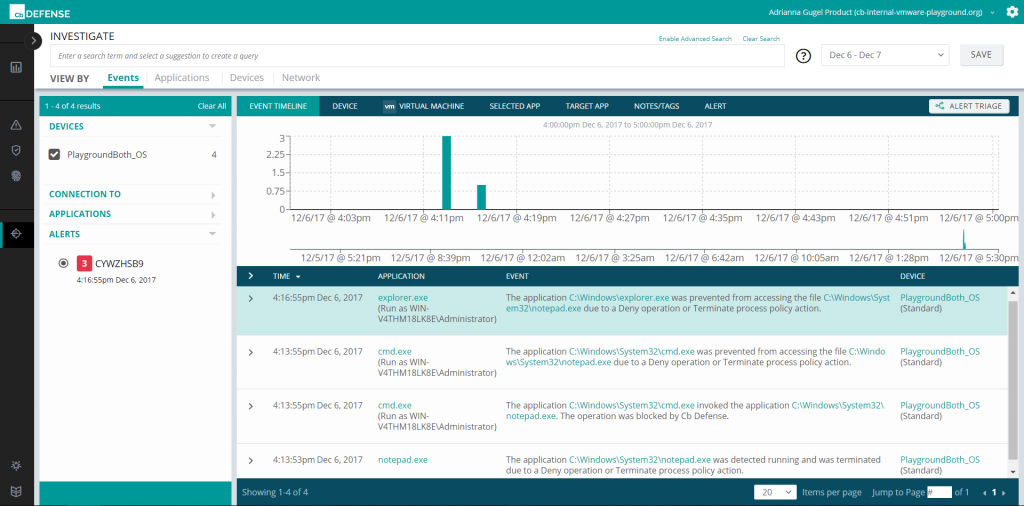
Another exciting feature of Carbon Black is real-time alerting and visualization so that a team of skilled IT security specialists could monitor the attacker’s actions, track them to the source, and block it once and for all.
And that’s how it happens:
- Carbon Black Cloud Sensor is deployed on a workstation;
- An information about a threat is sent to VMware Carbon Black Cloud;
- The cloud is continuously updating any information on possible threats;
- Analysis of the suspicious behavior based on rules;
- If anything triggers configured rules, it leads to pre-configured preventive actions via UEM API (such as quarantining the device or deleting the application);
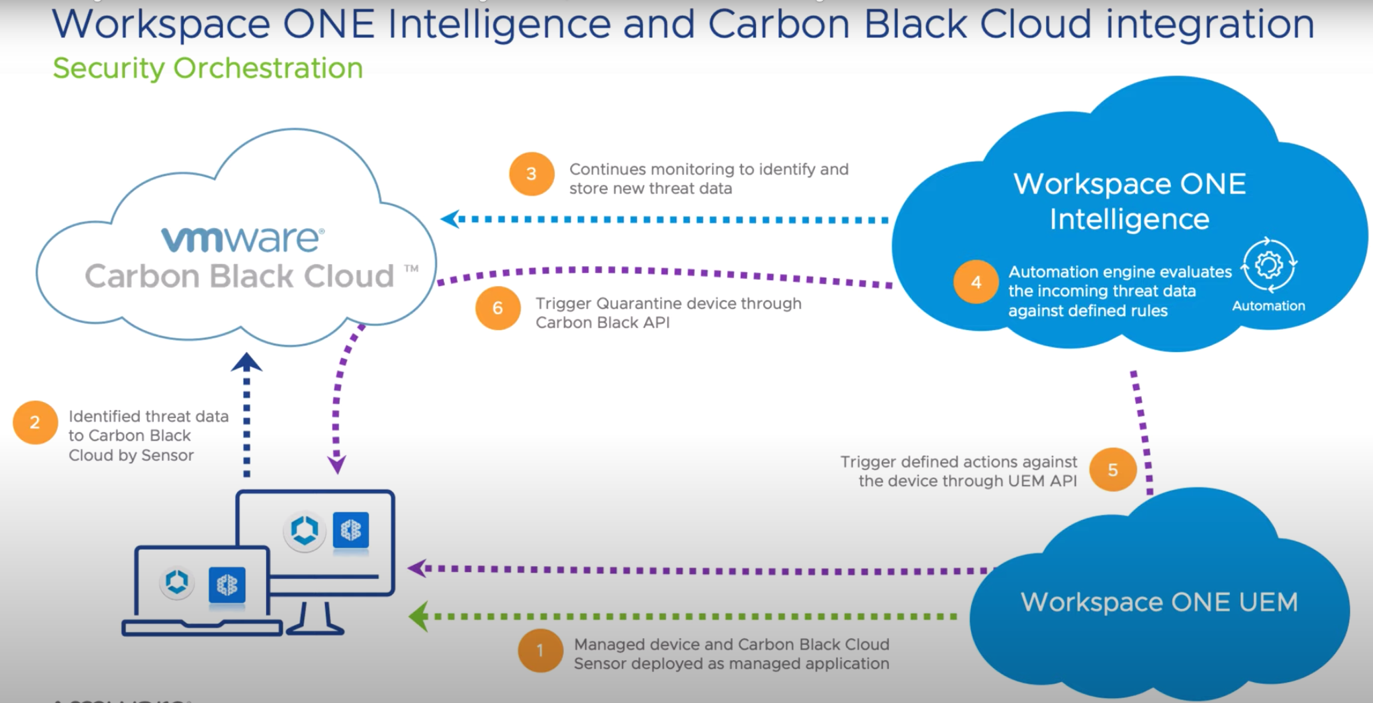
Also, as you can see while working with the Carbon Black solution, admins work with Workspace ONE UEM and ONE Intelligence at the same time.
CB just seems to be the most effective solution when it comes to ransomware, fileless malware, and a whole lot more complicated things that are explicitly designed to target a specific enterprise infrastructure.
You can check it out below, where VMware shows a ransomware-attack simulation and how Carbon Cloud deals with the problem:
Let’s take a closer look at what is going on here.
OK, so, an attack simulation has been started, and the malware is instantly and immediately blocked:
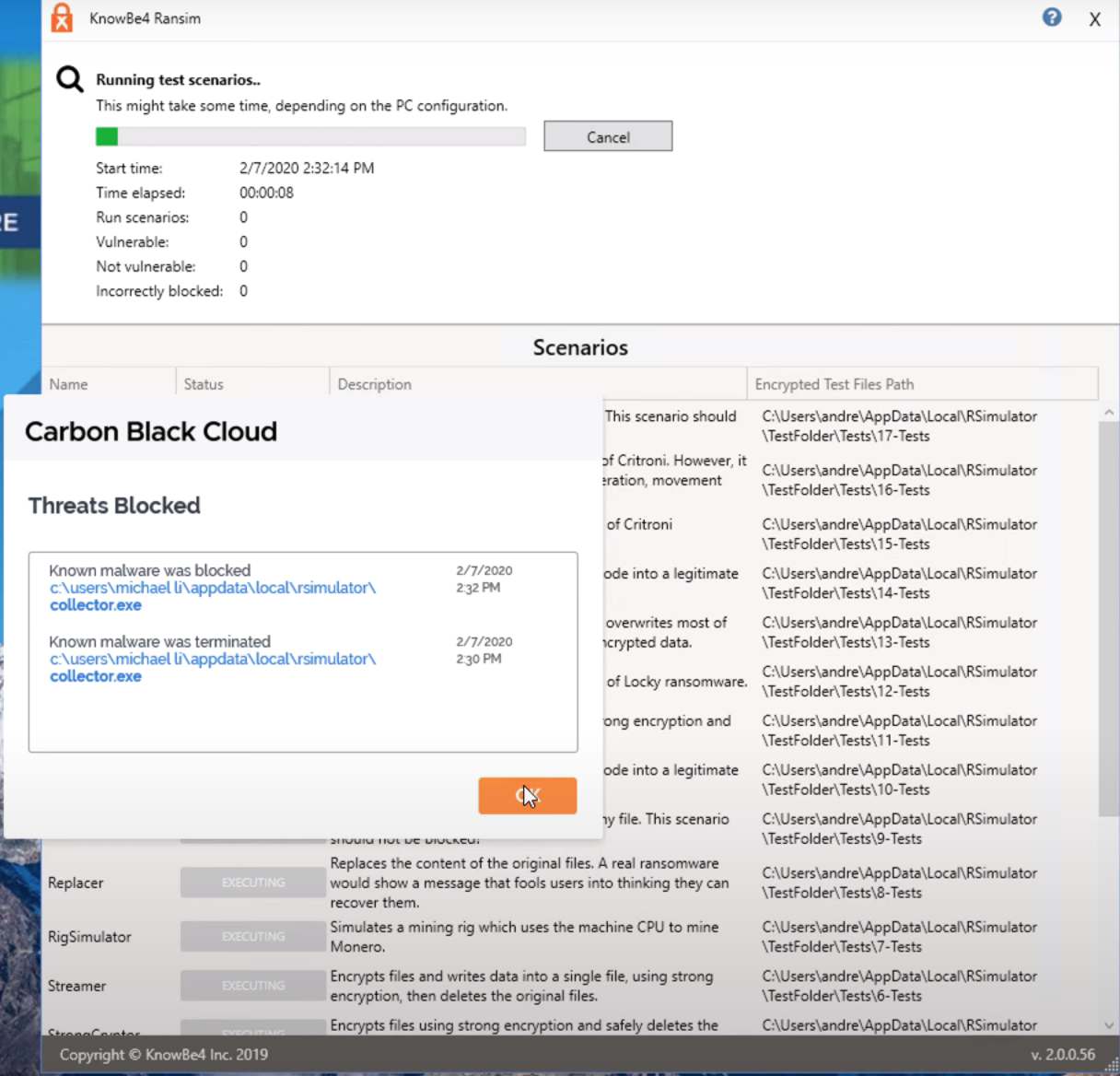
Furthermore, a suspicious DLL library is trying to get registered on the user’s laptop. However, with no luck, cause it gets caught by Carbon Black too:
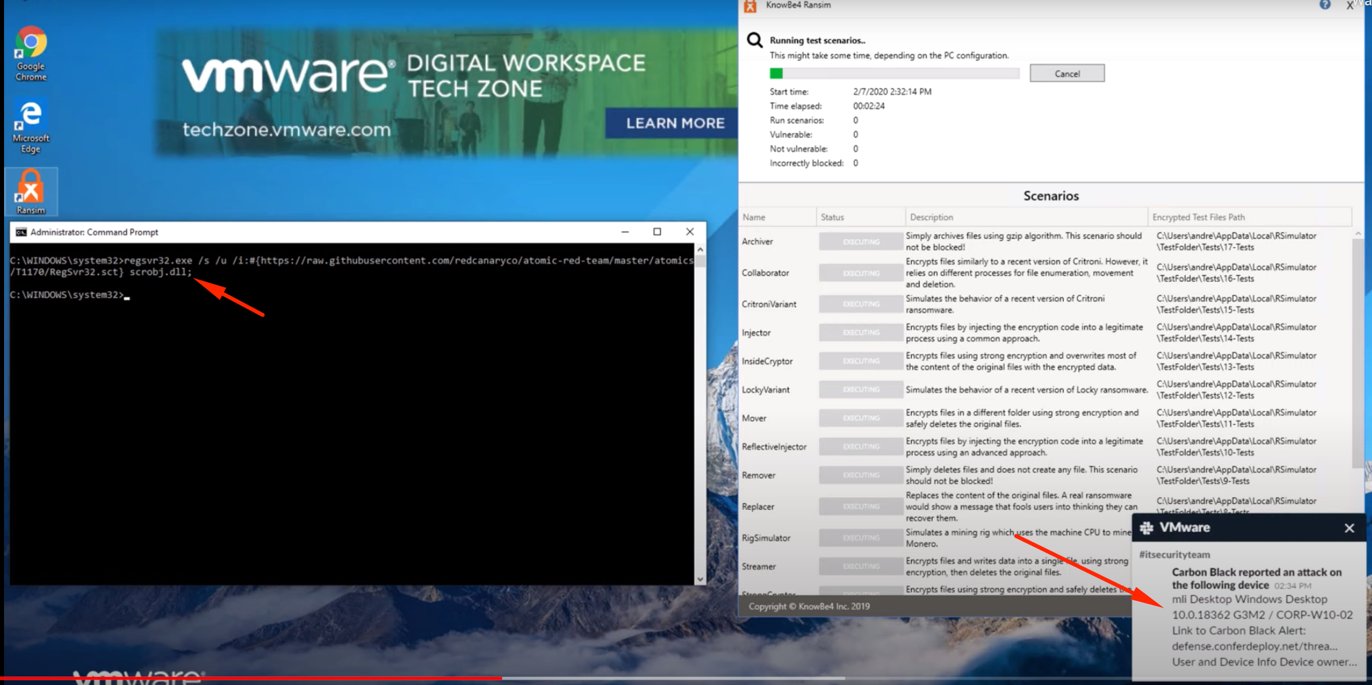
At the very same time, the IT security team receives a notification about the attack, where exactly has it occurred, and a link to its detailed description. It’s best to use integration with Slack:
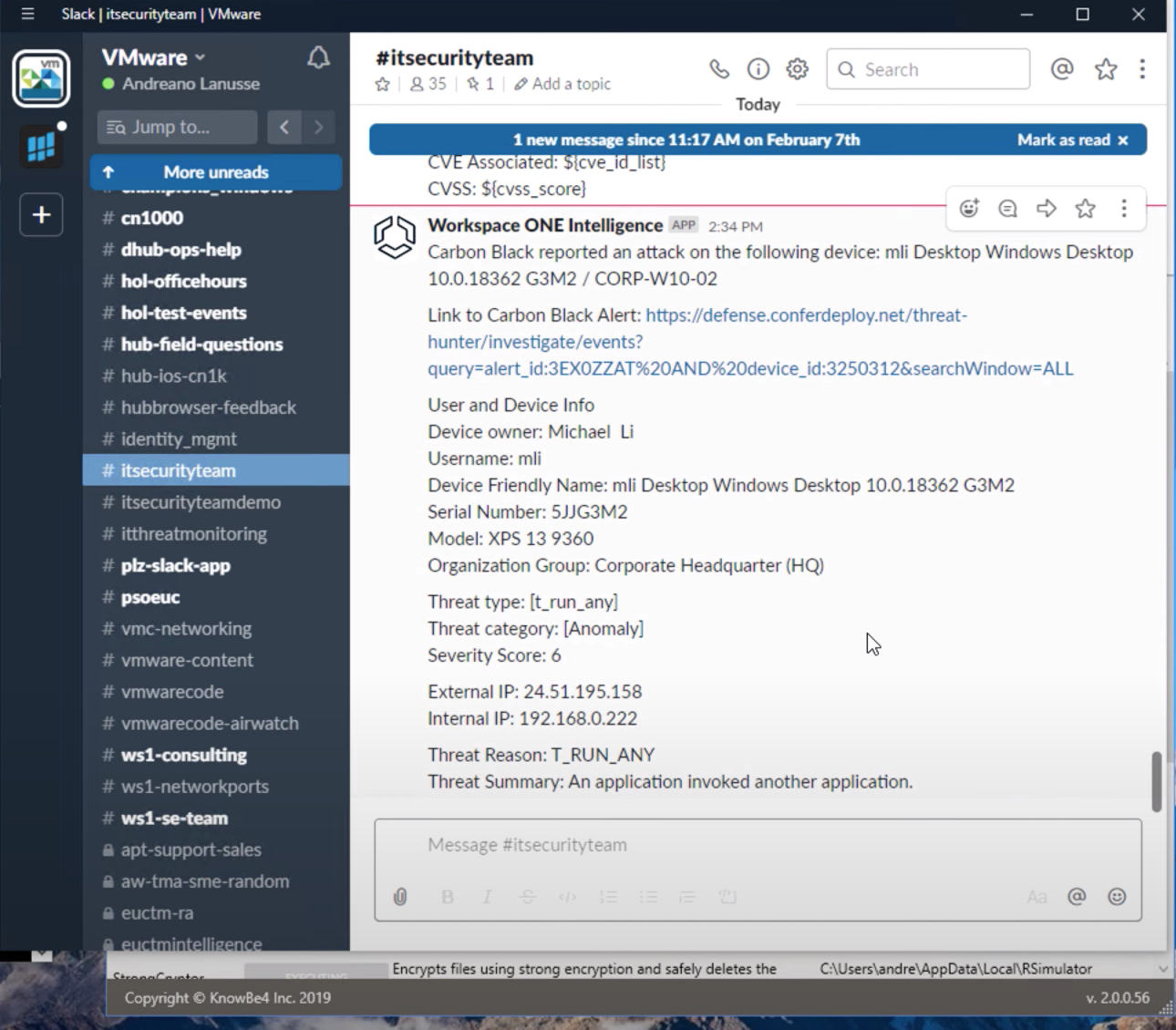
An appropriate reaction to such activity on your guest OS is quarantining the device (disabling it from the network entirely and only communicating through UEM API).
Following Slack’s link, the notification will provide an admin with a detailed log with the chronology of events and whatever details may be needed:
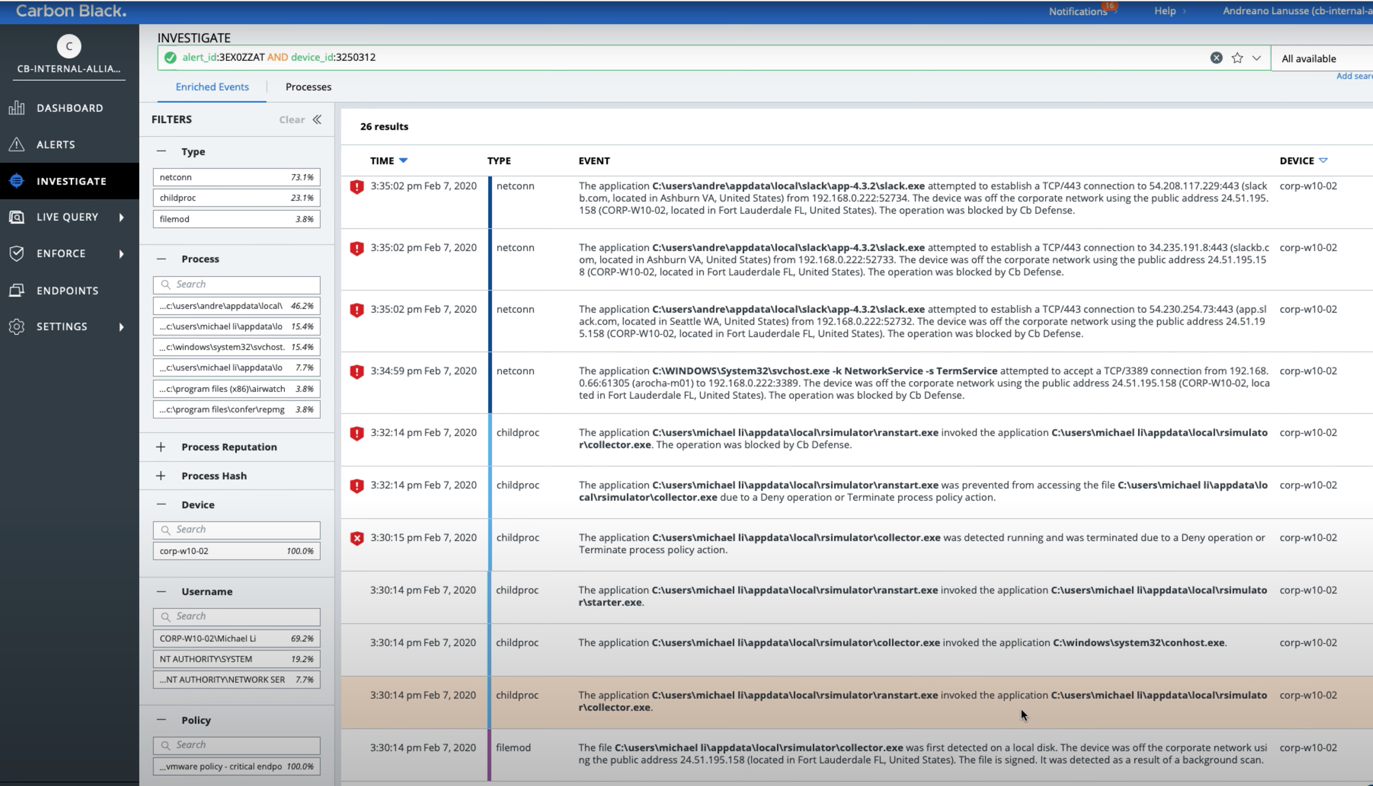
Also, in a description of each dangerous event, you can find a mentioning about it being blocked by Carbon Block (including all network communication efforts after the device was quarantined):
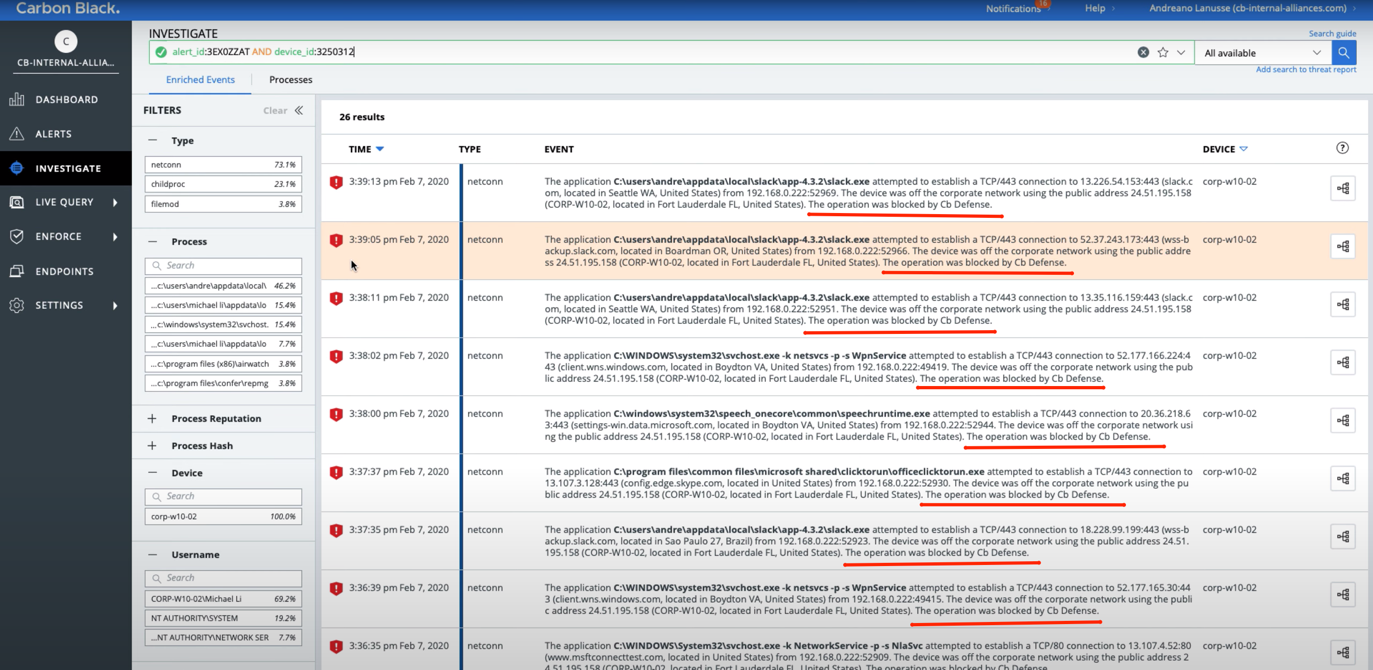
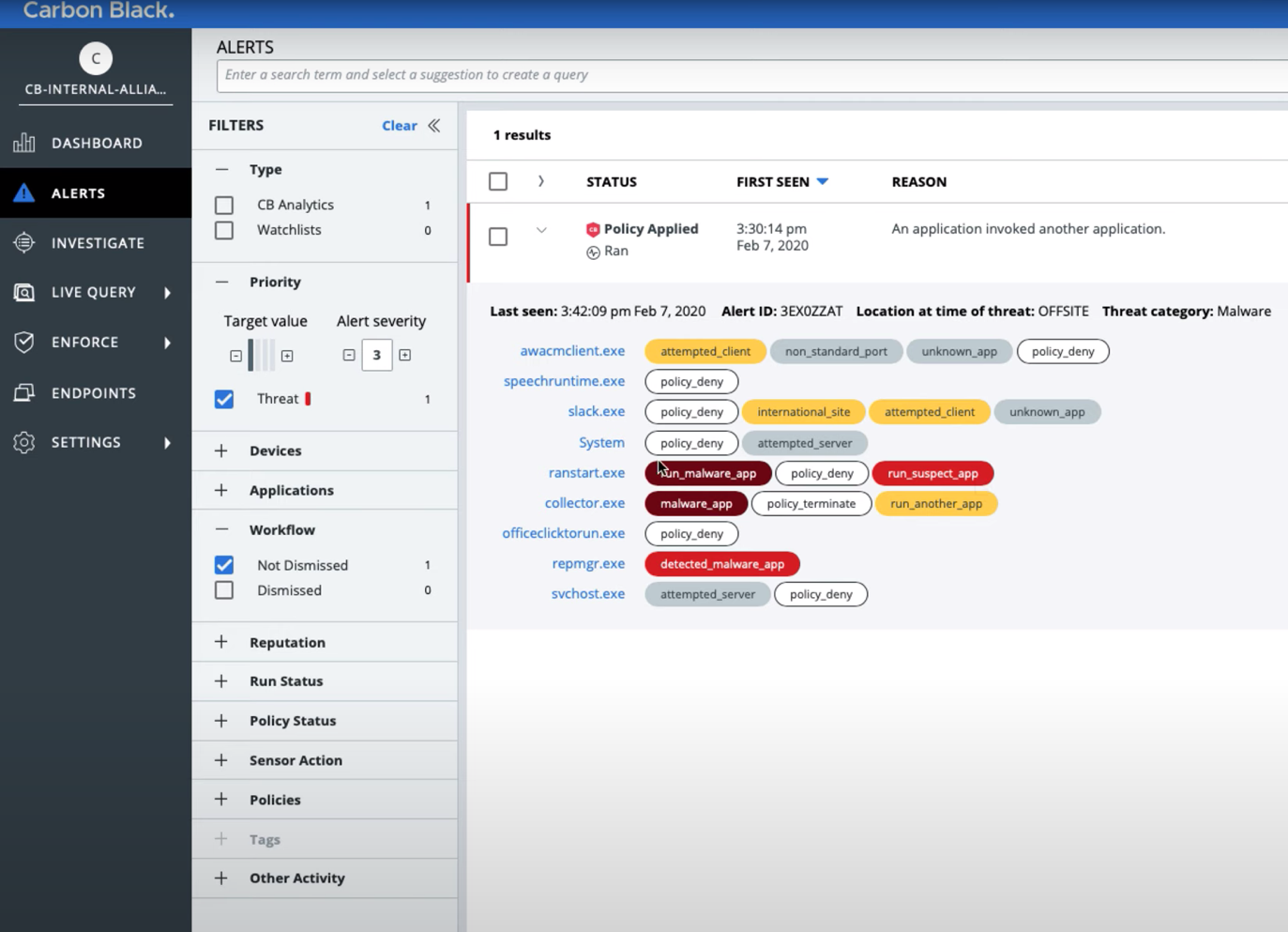
In the Alerts section, an admin can check each specific attack for all events in an aggregated order:
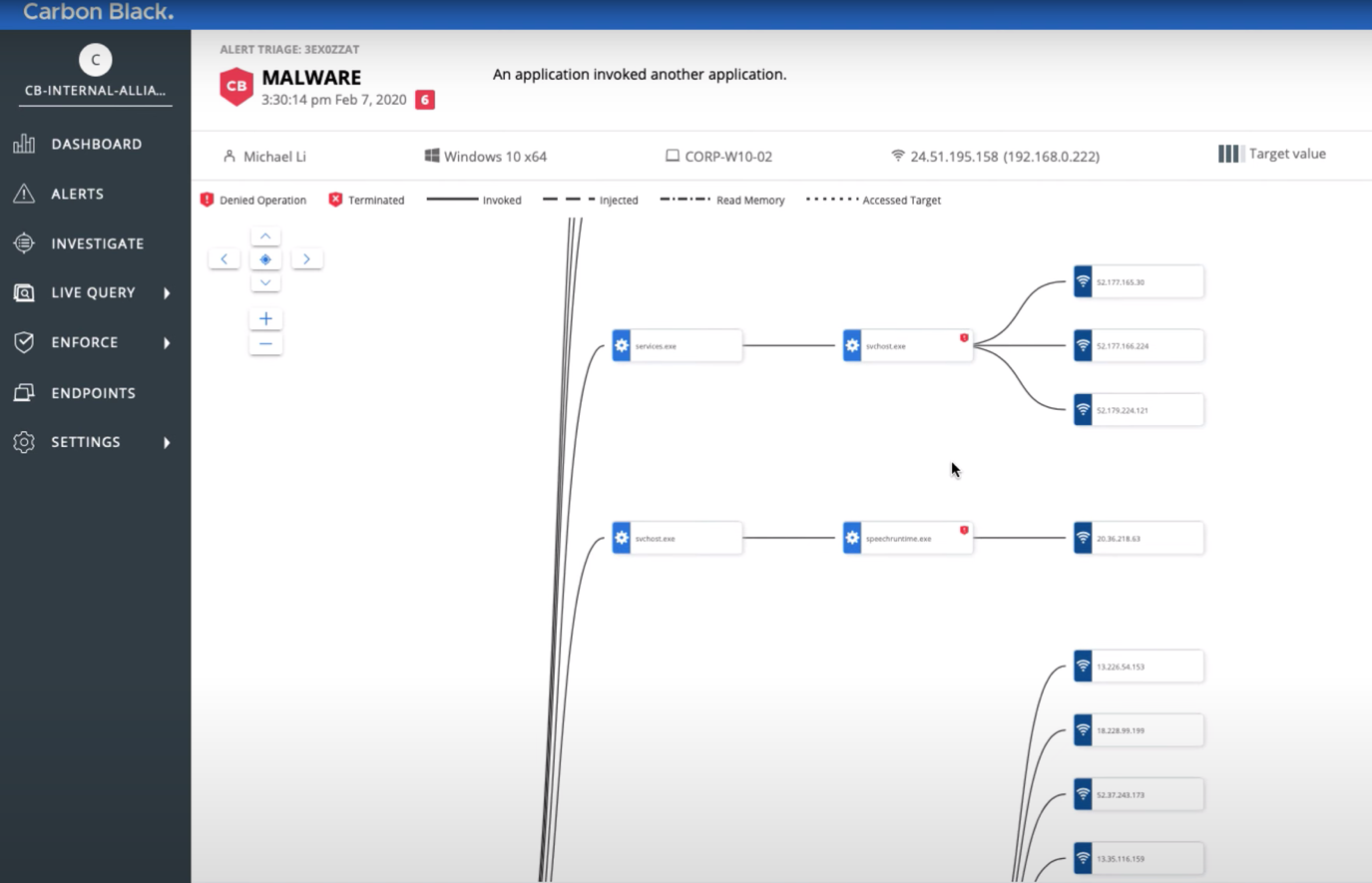
That’s when you can initiate an “investigation”, monitoring the whole chain of events so that you can visualize the entire chain of events (including destination IP addresses):
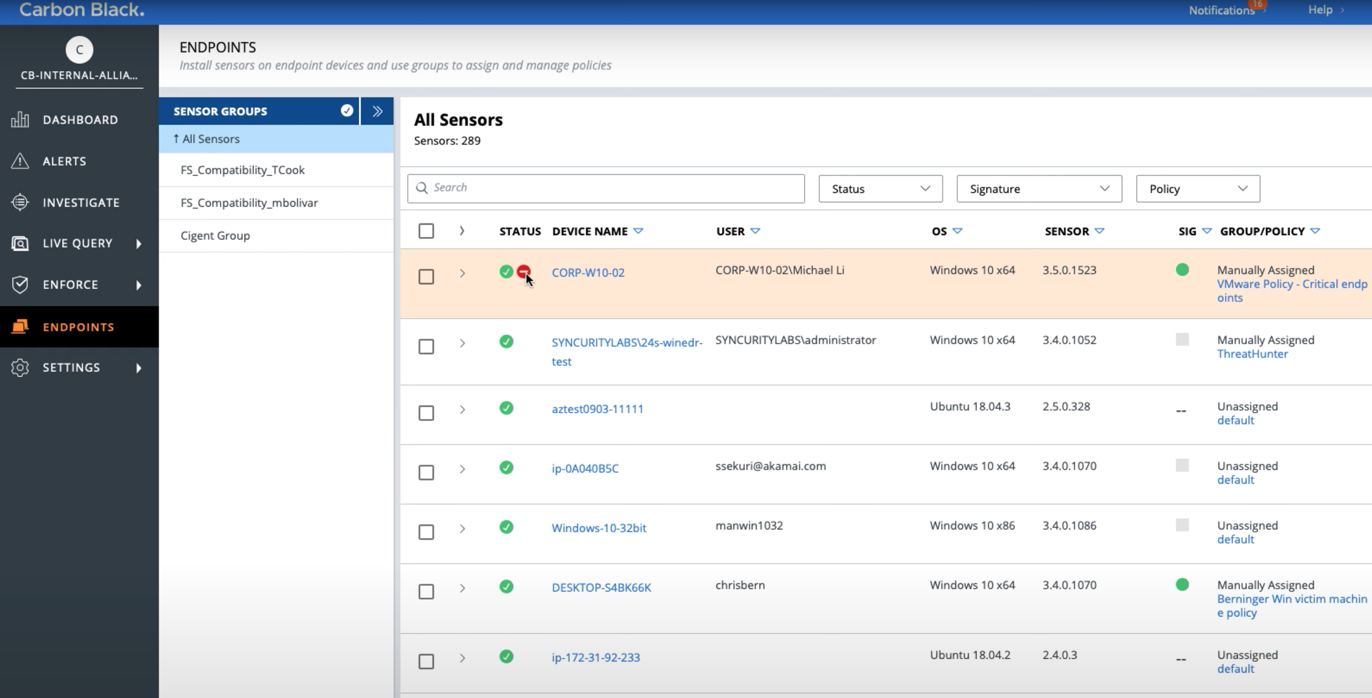
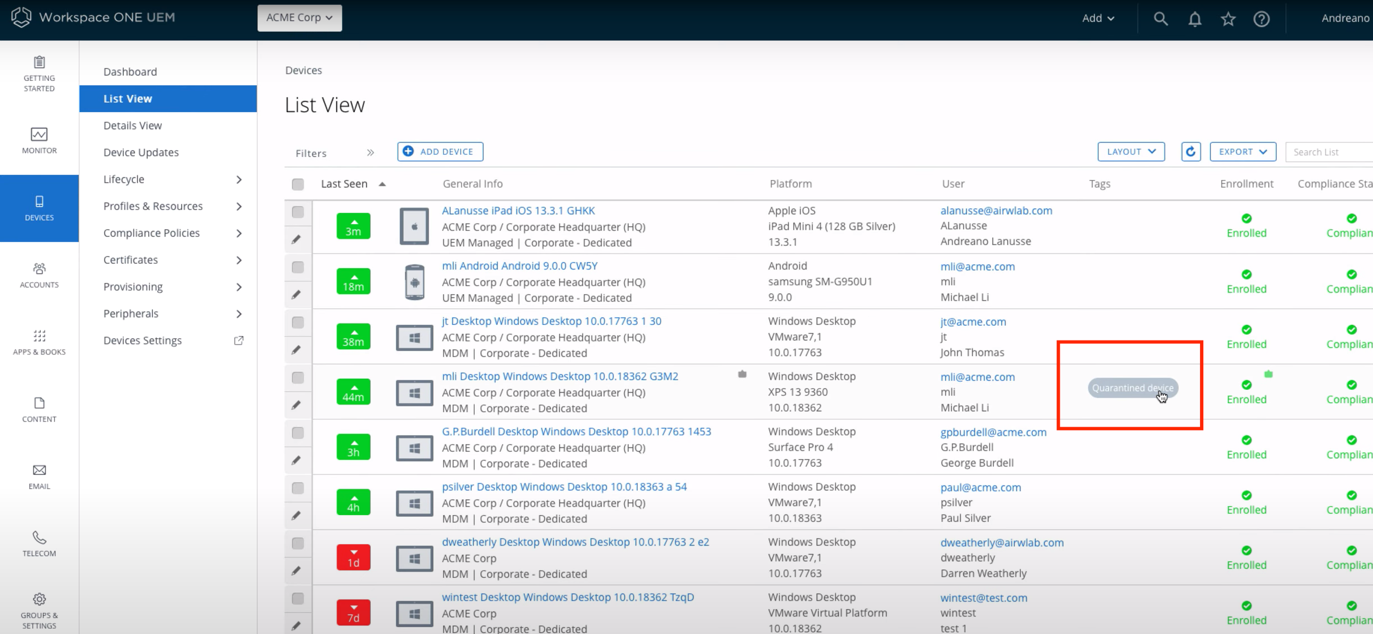
In the Endpoints section, there are all the workstations and their statuses. You can see all quarantined devices and manage them too:
For example, you can go to Live Response and perform any action you need through the console (such as editing the guest OS autorun section):
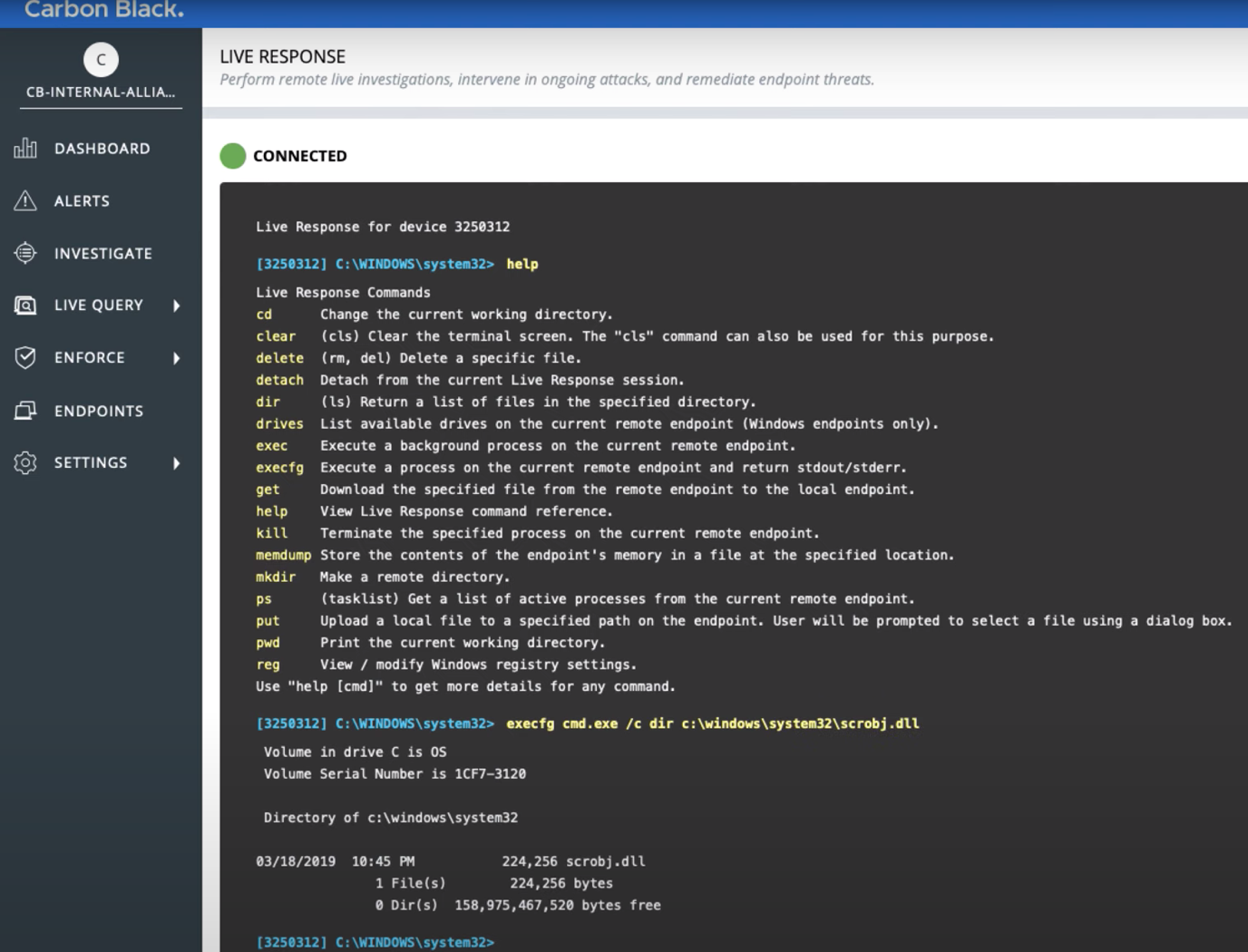
In VMware Workspace ONE UEM you can also see that the device is quarantined:
Finally, in the VMware Workspace ONE Intelligence console, you can manage to automate the response procedure in case of such events. For example, an admin can set specific rules to put a device in quarantine automatically and other actions depending on the severity of the threat, OS type, etc.
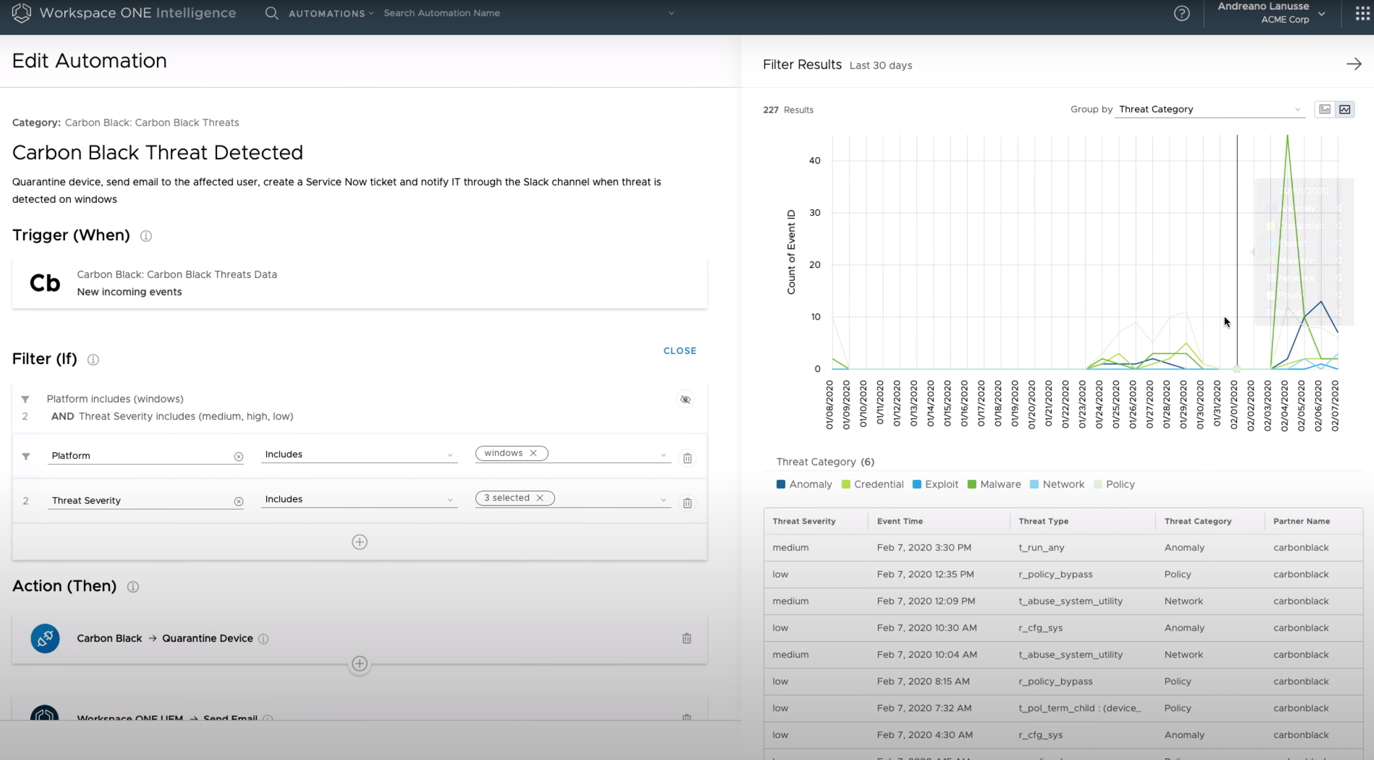
The same thing goes for the UEM API: you can send an email to an admin, create a ticket in ServiceNow, or just send a Slack notification.
Conclusions
As you can gather now, working with the VMware Workspace ONE UEM + ONE Intelligence + Carbon Black solution set enables you with the level of protection from different threats that firewalls and antivirus usually cannot match (such as, say, specifically tailored customized attacks). Besides, integration of Carbon Black with VMware NSX will provide you the protection of the whole network environment and following connections, therefore going beyond the guest OS level.
The most interesting thing is that Carbon Black and AppDefense are not mutually exclusive! VMware has recommended trying and using them together, which supposedly should expand the reach since AppDefense is working on a higher level and on the side of the data center can work with the solutions from the vRealize family. However, it does seem like these solutions sooner or later will spawn some third option which consolidates features from both products.




