There is no question that Microsoft has been taking a serious stance on security for the Windows platform with new security functionality and capabilities introduced across the board. We can see this by looking at modern requirements for Windows devices, such as Windows 11. For example, Microsoft now requires PCs to have Trusted Platform Modules (TPM) devices before users can install Windows 11.
In addition, Microsoft has introduced something starting in Windows 10 called Secured-core PCs that helps to secure the operating environment. Recently, Microsoft has added a new Secured-core PC configuration lock that provides additional protection. Let’s see how.
What is a Secured-core PC (SCPC)?
Before we look at the new functionality provided by the Secured-core PC configuration lock, what is a Secured-core PC (SCPC) in general? With Secured-core PCs, Microsoft is providing the tools for businesses to combat the growing trend of attackers going after kernel privileges by compromising vulnerable kernel drivers. Multiple malware variants go after these vulnerabilities, including RobbinHood, Uroburos, Derusbi, GrayFish, and Sauron. In addition, malware campaigns by the threat group STRONTIUM have leveraged driver vulnerabilities such as those in CVE-2008-3431, CVE-2013-3956, CVE-2009-0824, CVE-2010-1592.
When attackers can gain a foothold with kernel driver vulnerabilities, they can even disable security agents that may be present on an end-user PC. One thing is sure: traditional security tools and protections are ineffective against these attacks.
Modern cybersecurity requires a multi-layered approach that involves not only software but also involves security protection at the hardware level. Also, cloud-based security solutions such as those brought about by Azure Sphere provide what Microsoft refers to as a “chip-to-cloud” approach.
Secured-core PCs combine multiple layers of security using multiple technologies, including virtualization, operating system protections, hardware, and firmware protection. These work in conjunction with Microsoft Defender Advanced Threat Protection to provide end-to-end protection against advanced kernel privilege attacks. When all of these protective security layers are turned on, the PC is considered to be in a secured-core state.
Technologies enabled by Secured-Core PC
What technologies make up a Secured-core PC? Secured-core is not a single technology as such but rather is a combination of best practices and recommended security protections in place on Windows PCs, including:
- TPM 2.0 or higher – Trusted Platform Module (TPM) 2.0 is a technology that allows hardware-based security functions. It is a specially designed cryptoprocessor that stores crypto keys. TPMs are now the defacto standard in modern clients and servers and are required for installing Windows 11.
- Virtualization-based security (VBS) – VBS uses hardware virtualization technology to provide memory isolation for security-related constructs, so these aren’t directly accessible from the operating system. In this way, if the operating system becomes compromised, the protected memory area can remain isolated from malicious code. In addition, security solutions like Hypervisor-enforced Code Integrity (HVCI) rely on VBS.
- Windows Defender System guard – System Guard protects and ensures system integrity as the system boots up. The system is validated through both local and remote attestation. In addition, hardware-based trust guarantees firmware and other software are secure and is the authorized code intended to run on the system.
- Hypervisor-protected code integrity (HVCI) – HVCI is hypervisor-protected code integrity protecting systems against modification of the Control Flow Guard (CFG) settings and ensures valid certificates on other security services for services like Credential Guard.
- Credential Guard – Windows Credential Guard uses virtualization-based security (VBS) to help isolate secrets stored in memory so that only privileged system software can access them.
- Boot DMA Protection – Boot DMA protection includes Kernel DMA protection that protects against drive-by direct memory access (DMA) attacks using hot-plug devices plugged into Thunderbolt and CFexpress ports.
- Secure Boot – Secure Boot is a new boot standard helping to ensure the system is booting with only the trusted software from the OEM. Secure Boot checks software boot components, including UEFI firmware drivers, to ensure these are the expected signatures, helping to verify the integrity of the boot process.
Secured-core PC configuration lock
One of the challenges with security is maintaining a strong security posture. Also, if a device is configured as a Secured-core PC, you want to ensure that the endpoint remains secure with the settings and configuration. In addition, when a PC or laptop is given to an end-user with Secured-core, you want to ensure the Secured-core settings remain intact.
Microsoft has introduced a Secured-core PC configuration lock as a new capability for Secured-core PC. So what is a Secured-core PC configuration lock? In short, Secured-core PC configuration lock (config lock) is a new secured-core PC (SCPC) feature preventing configuration drift of secured-core PC features caused by intentional or unintentional misconfiguration. If the business intends for client PCs to be configured with secured-core features, it ensures these remain secured-core PCs.
The Secured-core configuration lock provides a way for admins to enforce policies on their corporate devices to keep them compliant and protect the operating system. It does this by quickly remediating insecure changes affecting the configuration of Secured-core PCs.
Even with MDM policies that can reconfigure security policy settings, the configuration drift may place the endpoint in a vulnerable state until the next configuration sync, which can take some time. Secured-core PC configuration lock prevents configuration drift for managed PCs with much quicker remediation. How?
Secured-core PC configuration lock provides almost instant remediation of configuration drift affecting endpoints’ security. How does this work? The client operating system monitors specific registry keys related to the secured-core PC configuration. When drift is detected in any of the keys, the secured-core PC configuration lock reverts the changes to the configuration in seconds.
Does configuration lock work on all PCs or only secured-core PCs?
The secured-core PC configuration lock only works with secured-core PC and does not work with PCs that are not enabled as a secured-core PC. Configuration lock only works with secured-core PCs.
What policies are locked?
Which secured-core PC configuration policies are locked exactly?
CSPs
- BitLocker
- PassportForWork
- WindowsDefenderApplicationGuard
- Application Control
MDM policies
- DataProtection/AllowDirectMemoryAccess
- DataProtection/LegacySelectiveWipeID
- DeviceGuard/ConfigureSystemGuardLaunch
- DeviceGuard/EnableVirtualizationBasedSecurity
- DeviceGuard/LsaCfgFlags
- DeviceGuard/RequirePlatformSecurityFeatures
- DeviceInstallation/AllowInstallatiofMatchingDeviceIDs
- DeviceInstallation/AllowInstallatiofMatchingDeviceInstanceIDs
- DeviceInstallation/AllowInstallatiofMatchingDeviceSetupClasses
- DeviceInstallation/PreventDeviceMetadataFromNetwork
- DeviceInstallation/PreventInstallatiofDevicestDescribedByOtherPolicySettings
- DeviceInstallation/PreventInstallatiofMatchingDeviceIDs
- DeviceInstallation/PreventInstallatiofMatchingDeviceInstanceIDs
- DeviceInstallation/PreventInstallatiofMatchingDeviceSetupClasses
- DmaGuard/DeviceEnumerationPolicy
- WindowsDefenderSecurityCenter/CompanyName
- WindowsDefenderSecurityCenter/DisableAccountProtectionUI
- WindowsDefenderSecurityCenter/DisableAppBrowserUI
- WindowsDefenderSecurityCenter/DisableClearTpmButton
- WindowsDefenderSecurityCenter/DisableDeviceSecurityUI
- WindowsDefenderSecurityCenter/DisableEnhancedtifications
- WindowsDefenderSecurityCenter/DisableFamilyUI
- WindowsDefenderSecurityCenter/DisableHealthUI
- WindowsDefenderSecurityCenter/DisableNetworkUI
- WindowsDefenderSecurityCenter/Disabletifications
- WindowsDefenderSecurityCenter/DisableTpmFirmwareUpdateWarning
- WindowsDefenderSecurityCenter/DisableVirusUI
- WindowsDefenderSecurityCenter/DisallowExploitProtectioverride
- WindowsDefenderSecurityCenter/Email
- WindowsDefenderSecurityCenter/EnableCustomizedToasts
- WindowsDefenderSecurityCenter/EnableInAppCustomization
- WindowsDefenderSecurityCenter/HideRansomwareDataRecovery
- WindowsDefenderSecurityCenter/HideSecureBoot
- WindowsDefenderSecurityCenter/HideTPMTroubleshooting
- WindowsDefenderSecurityCenter/HideWindowsSecuritytificationAreaControl
- WindowsDefenderSecurityCenter/Phone
- WindowsDefenderSecurityCenter/URL
- SmartScreen/EnableAppInstallControl
- SmartScreen/EnableSmartScreenInShell
- SmartScreen/PreventOverrideForFilesInShell
Enable secured-core configuration lock
To enable the secured-core PC configuration lock, you need to do this from Microsoft Intune in the Endpoint Manager. First, log into Endpoint Manager and navigate to Devices > Configuration profiles > Create profile. Choose the following:
- Platform – Windows 10 and later
- Profile type – Templates
- Template name – Custom
Once these are selected, click the Create button.
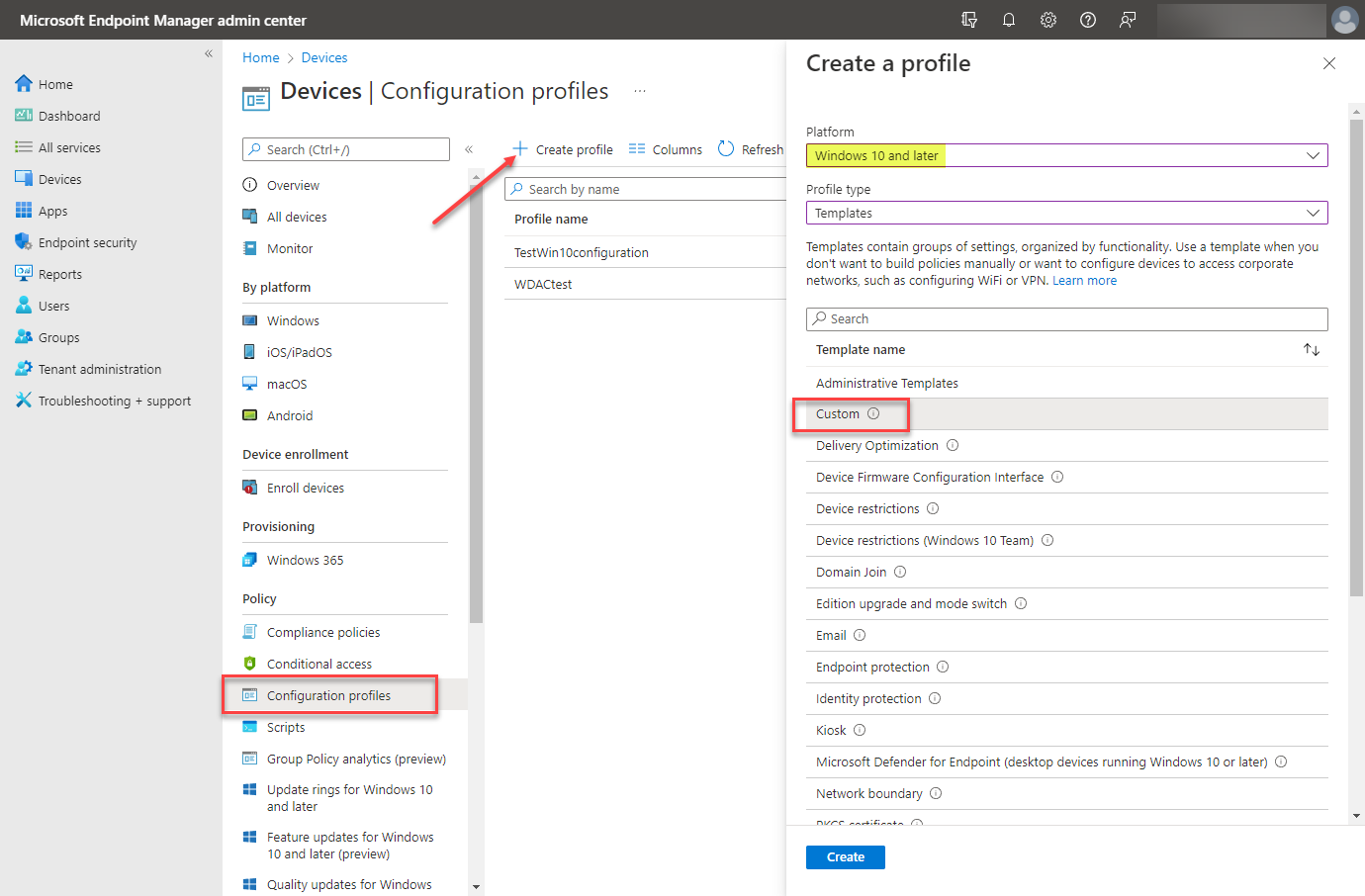 Beginning the process of creating a new configuration profile for secured-core PC configuration lock
Beginning the process of creating a new configuration profile for secured-core PC configuration lock
The wizard begins. On the Basics screen, name the new secured-core PC configuration profile. Click Next.
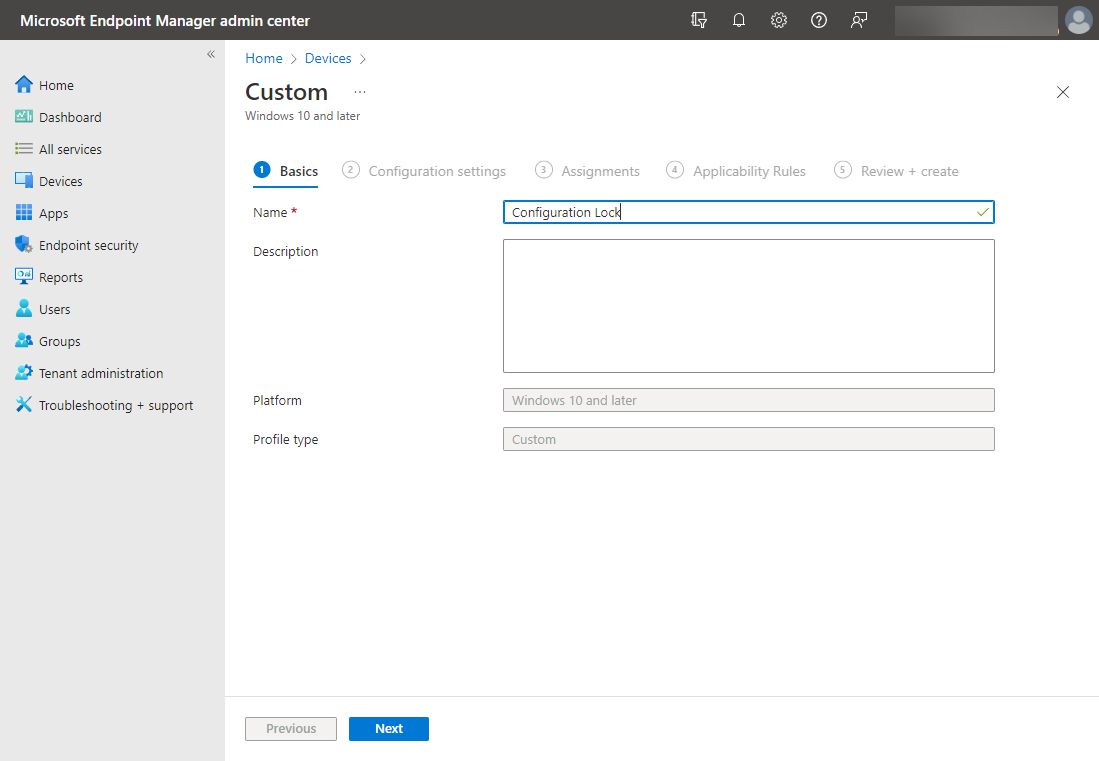 Name the new secured-core PC configuration lock configuration profile
Name the new secured-core PC configuration lock configuration profile
On the Configuration settings screen, click the Add button.
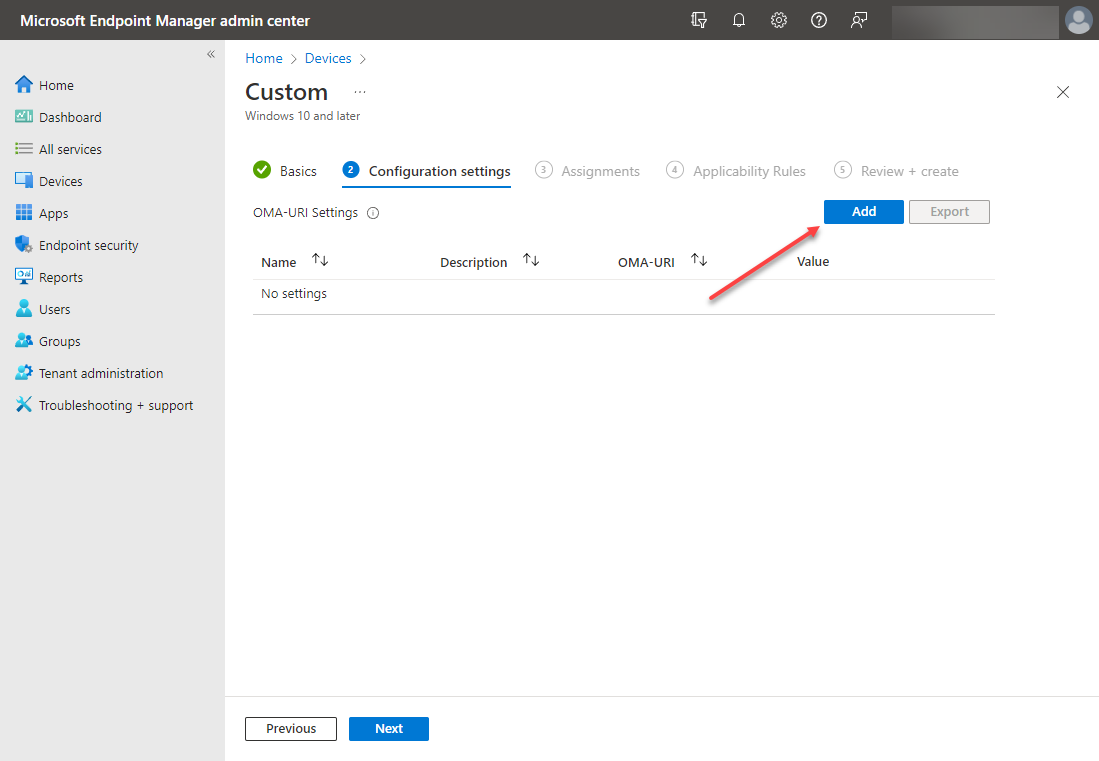 Beginning the process to add a new configuration settings policy
Beginning the process to add a new configuration settings policy
In the Add Row blade, enter the following:
- Name – The name for your configuration lock OMA-URI settings
- Description – The optional description for the settings
- OMA-URI – For secured-core PC configuration lock, you need to enter the following:
./Vendor/MSFT/DMClient/Provider/MS%20DM%20Server/ConfigLock/Lock
- Data type – Integer
- Value – To enable, enter 1. To disable, enter 0
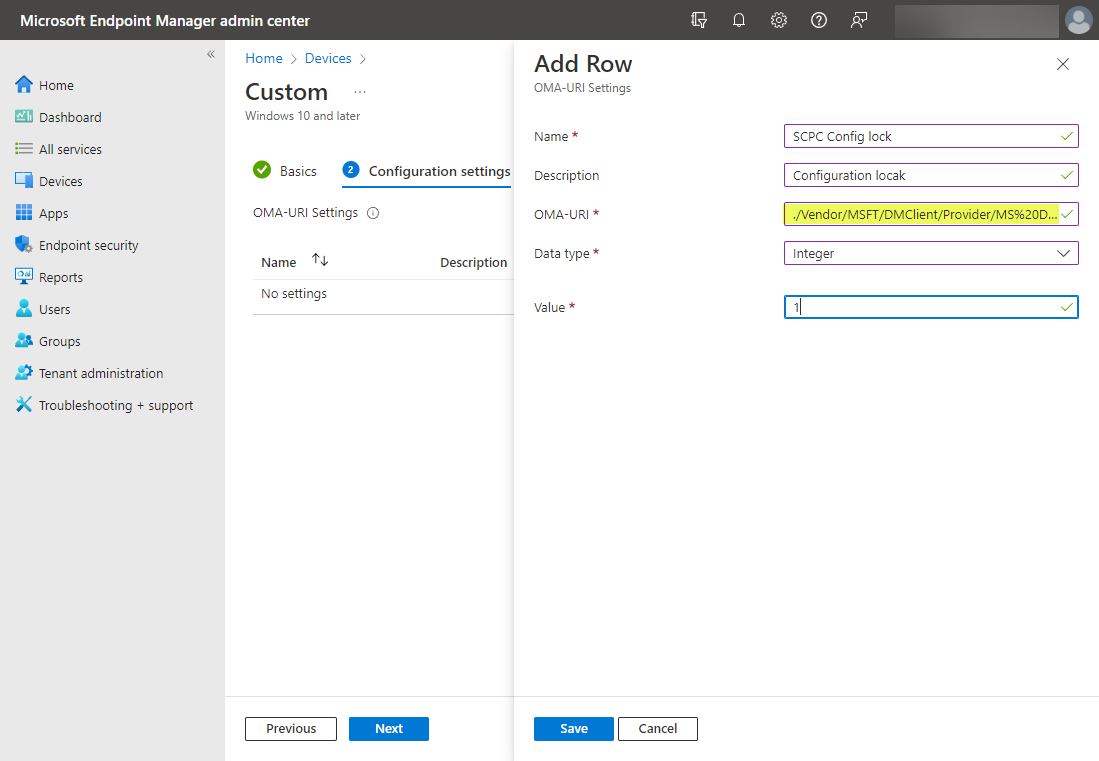 Creating the new OMA-URI settings for secured-core PC configuration lock
Creating the new OMA-URI settings for secured-core PC configuration lock
The new OMA-URI settings are added successfully.
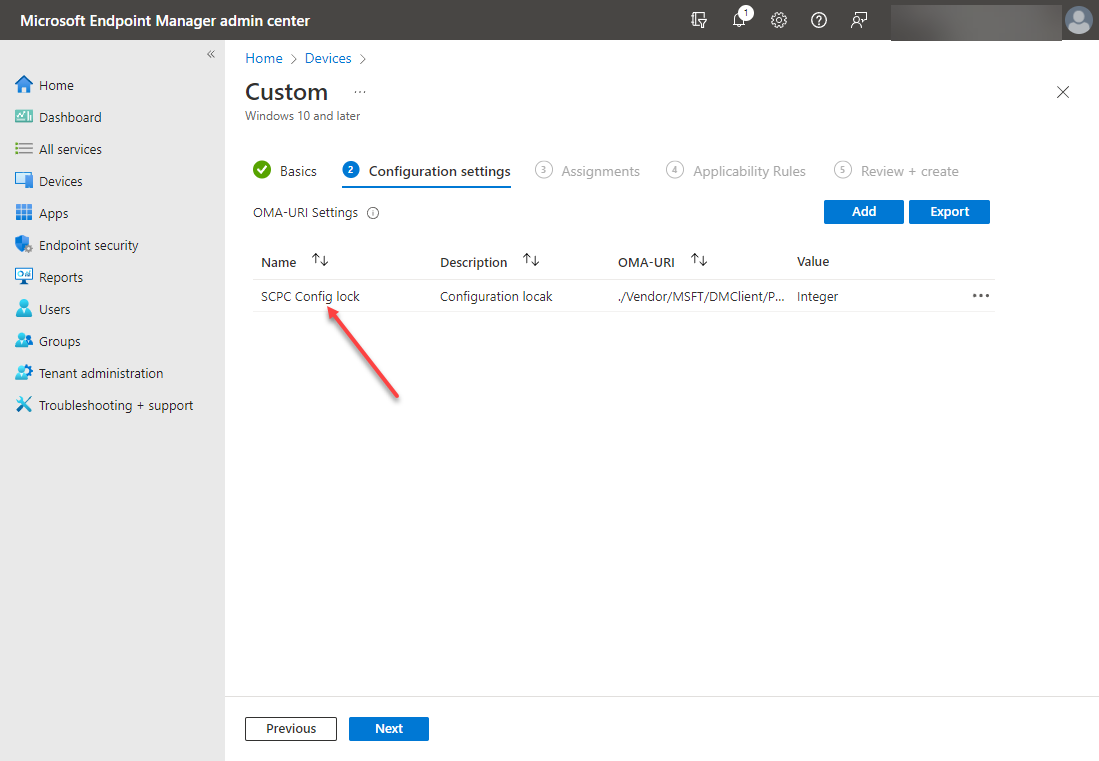 OMA-URI settings are successfully added
OMA-URI settings are successfully added
Choose the assignments for the configuration policy. Here you will select the group(s) you want to apply the new configuration profile for enforcing secured-core PC configuration lock.
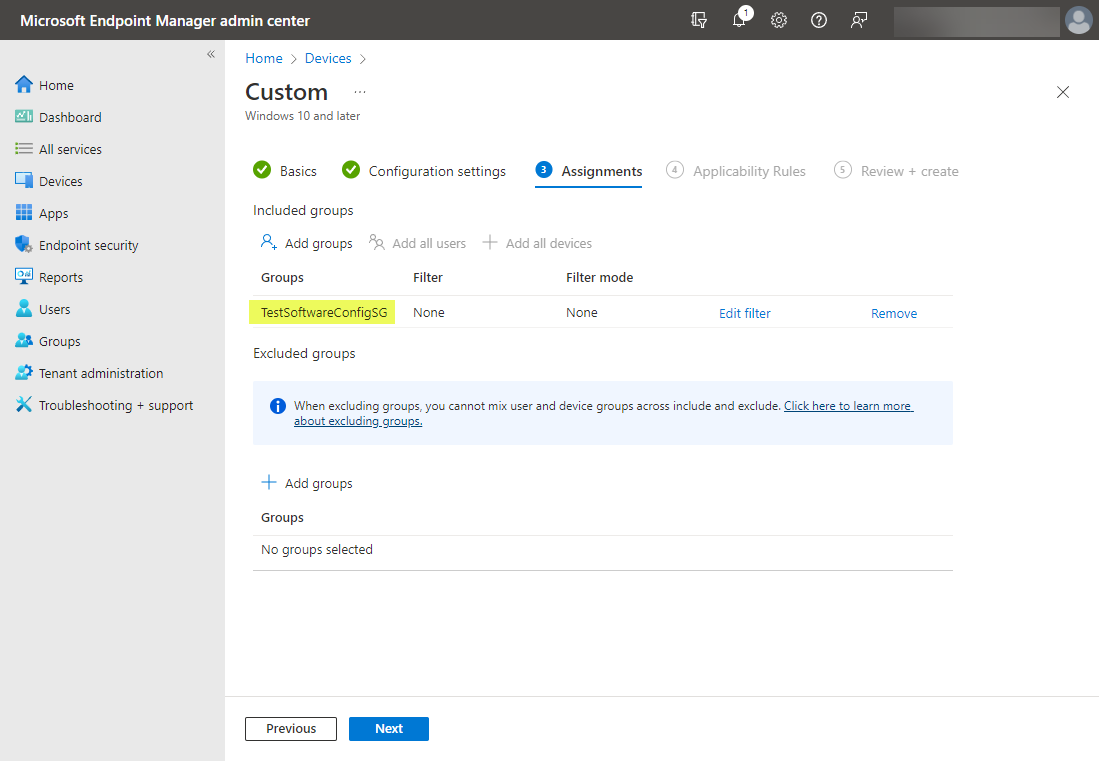 Adding the group to apply the new secured-core PC configuration lock to in your organization
Adding the group to apply the new secured-core PC configuration lock to in your organization
Click Next on the Applicability Rules.
 Applicability rules in the new configuration profile
Applicability rules in the new configuration profile
On the Review and Create page, click the Create button.
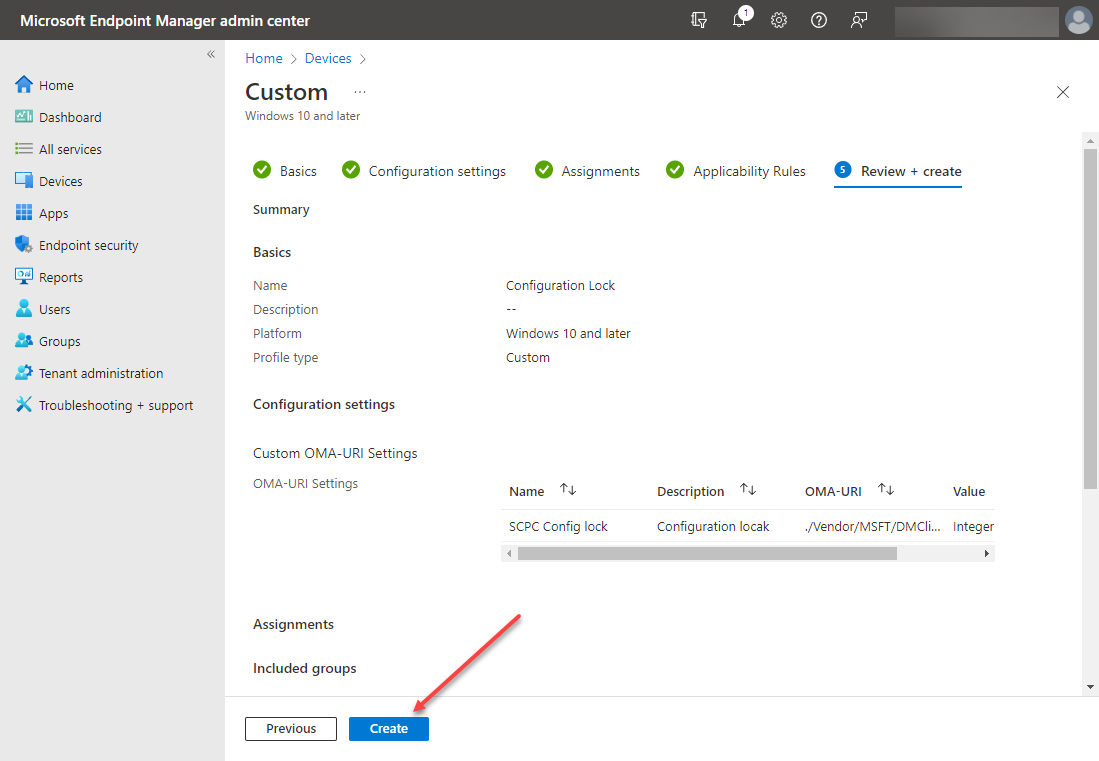 Review and create the new secured-core PC configuration lock configuration profile
Review and create the new secured-core PC configuration lock configuration profile
You should now see the newly added configuration profile for the secured-core PC configuration lock listed in your configuration profiles.
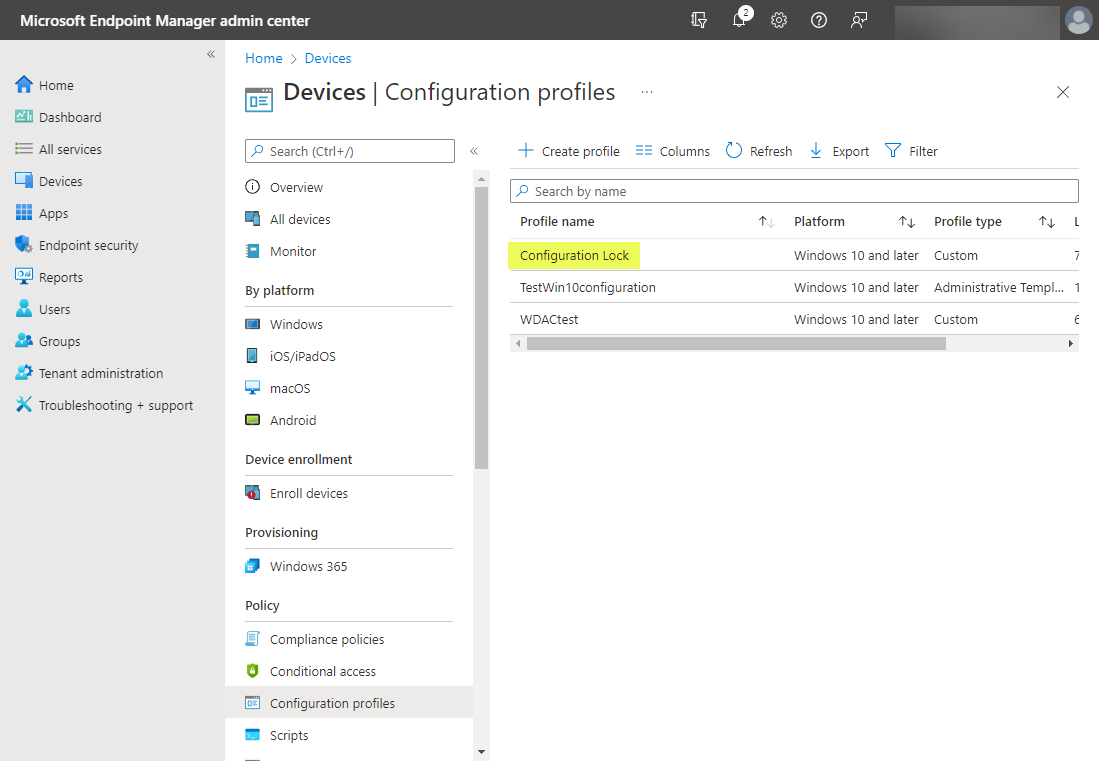 Newly created secured-core PC configuration profile in devices configuration profiles
Newly created secured-core PC configuration profile in devices configuration profiles
Wrapping Up
Modern security requires a multi-layered approach involving hardware, software, and cloud technologies to help defend against today’s very sophisticated and complex threats against endpoints. The secured-core PC group of technologies combines to form a robust security mechanism helping to protect against these modern attacks.
The new secured-core PC configuration lock is an excellent addition to secured-core PC (SCPC) technologies, allowing admins to effectively “lock” security protections in place. According to Microsoft, when configuration drift is detected away from the secure posture provided by the secured-core PC, the new configuration lock remediates the configuration in seconds. As shown, the new secured-core PC configuration lock is easily configured using Microsoft Endpoint Manager device configuration profiles.
Learn more about secured-core PC configuration lock in the official documentation from Microsoft here:
Secured-core configuration lock – Windows Client Management | Microsoft Docs




