Some years back, I came across a piece of software called sandboxie which is an application that, when running, ring-fences a part of the hard drive as a sort of scratch area to do its work in.
When any application is launched via the sandoboxie tool, sandboxie uses that scratch area to allow whatever is launched to do its work and then, when the application is closed the sandboxie service would terminate everything running from that ringfenced area.
The whole idea was that it would be a way of running things you might not be certain about to confirm that they were safe (or not!) and then the contents could be deleted just by closing the app. Sandboxie first hit the internet around 2004. When Sandboxie first hit the internet, IT security was really still in its infancy but there were already scandals involving several companies where they had been hit by a mass virus infection or had sent out disks or CD’s that had a virus on them.
These days, security is a much more serious affair with some heavy penalties for companies who end up disclosing personal data through a breach. With this in mind, I have been surprised that no one has taken the sandbox idea and developed it further. Well, Microsoft have now released “Sandbox mode” in Windows 10 build 18898 and above.
The Windows 10 Sandbox mode is a small virtual machine that runs on windows 10 and, when you close the VM, Windows 10 resets it back to a default image. That means that anything that has been installed is gone, any data that might have been created is gone. It is a full reset back to a “last known good state”.
Sandbox mode is easily installed via the windows features menu:
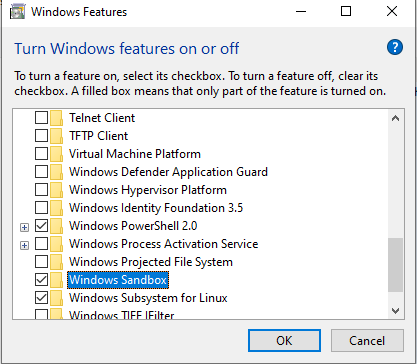
Once installed a reboot will be required.
In summary, sandbox mode is a very nice additional feature to winodws but it doesn’t remove the need for anti-virus software as not everything can or will run in the sandbox system, each time the VM is restarted it reverts to default.
Sandbox mode is another nice feature alongside existing features such as Bash in Windows and it shows that Microsoft are taking the Hyper-V technology and trying out some interesting options with it. I hope they continue but I cannot see the windows sanbox mode catching on for day to day activies as it just takes time to set up. It would be nice to see if MS offer any tools for basic sandbox customisation such as freezing a sandbox with say, google chrome pre-installed or even a deployment tool like chocolately and a post-launch deployment script. Those would add a bit more value and use to the mode.
Launching sandbox mode for the first time was very slow as Windows had to spin up the environment, subsequent launches were much faster, taking about 40 seconds to bring the VM up to a point that it could be used.
It should be noted that the hardware I am running it on is not the latest and greatest, I am sure that newer hardware will perform much better.
It is important to realise that sandbox mode is not a panacea; it is not something where you can install cryptolocker to see what it does and for it to have and no effect on the network.
The key thing to understand is that by default, this sandbox machine is not really a sandbox, not in the sense of being either restricted or air gapped. It still has connectivity.
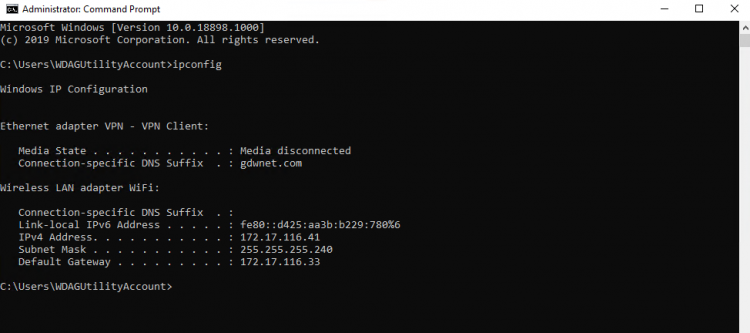
An ipconfig on the VM shows that it has logged me in with an administrator level account and has given the VM an IP in the class B private managed range. This IP has not come from my DHCP server but from the NAT pool used by Hyper-V. The VM still has connectivity through this NAT connection out to the wider world, that means that anything ‘bad’ on the sandbox VM can still get out onto the internal network and potentially wreak havoc.
 As an example, if you decided to run a cryptolocker style piece of ransomware in the sandbox, it would infect the sandbox and if the software was designed spread as much crypto type infections are, it would be able to use the NAT interface to be able to find hosts that have missing patches and potentially spread that way.
As an example, if you decided to run a cryptolocker style piece of ransomware in the sandbox, it would infect the sandbox and if the software was designed spread as much crypto type infections are, it would be able to use the NAT interface to be able to find hosts that have missing patches and potentially spread that way.
The only two reduces in risk here would that the sandbox is not on the domain and that it likely has a different IP range to your internal network. Both of these mitigations would merely slow down the spread of something
If you have a need to run something that you are not sure about and if you want to analyse exactly what that software will do, nothing can beat a purpose built VLAN that has just internet access with just a single clean machine and enhanced firewall logging. This sort of setup can take some time to configure and there is always the risk of a misconfiguration allowing something malicious to escape onto the main network.
Sandbox mode certainly has its advantages; it can be a handy way to install a piece of software for testing out the install process or to test out a new automated task, it can be used to help test software for anything malicious but caution must be taken due to the aforementioned default NAT access to the wider network.




