As many admins of virtual infrastructures know, for the first time ever, VMware vSphere 6.5 received the long awaited encryption feature of both virtual disks content and vMotion hot migrations.
The VMs encryption works based on AES-NI algorithm, and the key management is carried out based on KMIP 1.1 standard. When I/O operation comes to the disk of the virtual machine, it is immediately encrypted on-the-fly, which provides complete security against data security attack.
Not only virtual disks, but also VMX configuration files, snapshot files and all other file objects related to the virtual machine are encrypted.
VM objects encryption is fulfilled externally. This way the guest OS doesn’t have access to the encryption keys. Encrypted virtual machines are always transferred between the ESXi hosts with vMotion, which is also encrypted.
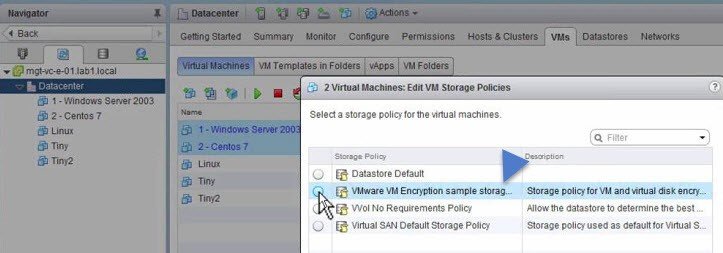
To start virtual machine encryption, an appropriate storage policy should be assigned to it:
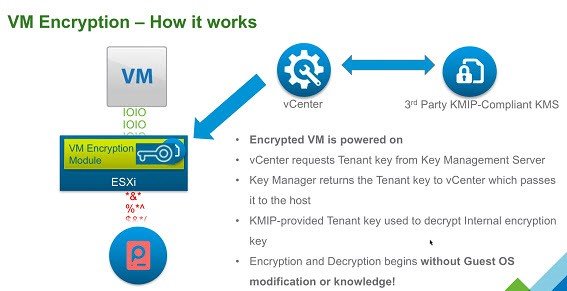
How VM Encryption in VMware vSphere 6.5 works:
- User assigns VM Encryption policy at the virtual machine level.
- For the VM, a random key is generated and encrypted with a key from the key manager (KMS key).
- When VM is switched on, vCenter server receives the key from the Key Manager and sends it to VM encryption Module on ESXi server, which unlocks the key in the hypervisor.
- Next, all I/O operations are carried out through encryption module, encrypting all input and output SCSI-commands transparently for guest OS.
All those things are compatible with third-party key management systems (and requires one of them) built on standard KMIP of version 1.1 or higher:
To decrypt virtual machine and then store it in regular format, just set default storage policy (Datastore default).
Also, there is special PowerCLI cmdlets, which can encrypt or decrypt VM and detect which of them are encrypted at the moment. For example, this way you can encrypt VM with default encryption policy in the last PowerCLI update:
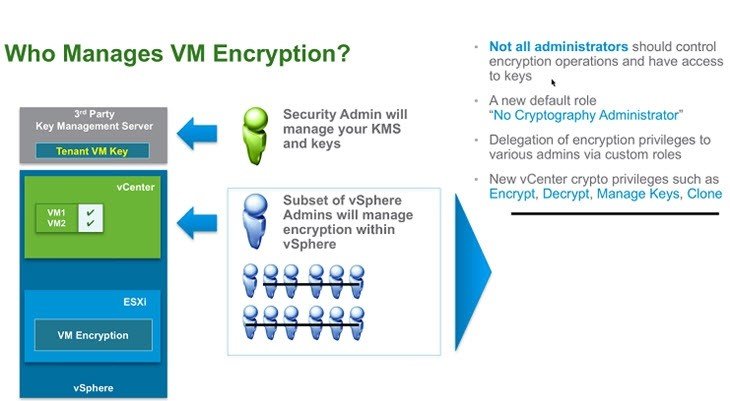
Get-VM -Name <VM name> | Enable-VMEncryptionvCenter works just as a client in the encryption system. For key handling, Key Management Server (KMS) is used.
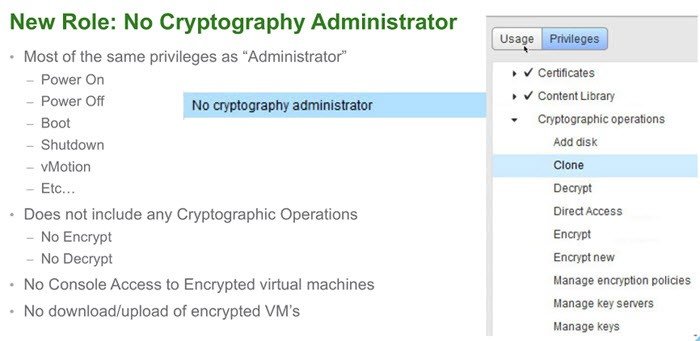
In privileges control mechanism, there is now new No Cryptography Administrator role. If it is assigned, the following privileges will be denied to standard administrator:
- Manage key servers
- Manage keys
- Manage encryption policies
- Console access to encrypted VMs
- Upload/download encrypted VMs
Any external systems working after KMIP standard can be used as KMS:
When using VM encryption, the following things should be considered:
- Yes, you will definitely need key management system (external Key Management Server).
- Backup options are supported through Ethernet only (no SAN-to-SAN backup).
- If you make backup copy for regular backup method, it will be unencrypted, if you recover it – everything will comply with target storage policy (that is, VM can appear to be unencrypted after the recovery).
- The vCenter server can’t be encrypted itself – otherwise, it couldn’t be switched on at all.
- Also, the following options are not supported:
- Suspend/resume
- VM encryption with snapshots and creation of snapshots for encrypted VMs
- Serial/Parallel port
- Content library
- vSphere Replication
For vMotion, encryption works on the VM-level, and for synchronization data transfer 256-bit encryption keys are used. Encryption of the vMotion traffic works on VMkernel level with widely used algorithm AES-GCM (Advanced Encryption Standard / Galois Counter Mode).
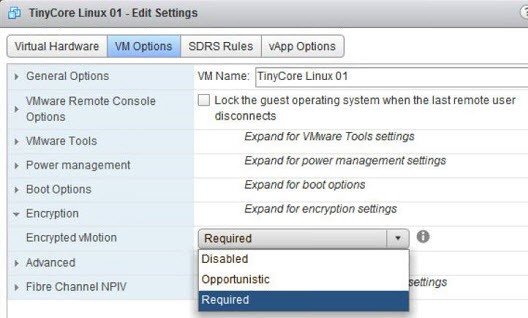
There are 3 policies for encrypted vMotion:
- Disabled – switched off.
- Opportunistic – encryption only in case it is supported by source and target host ESXi, otherwise vMotion will be unencrypted.
- Required – will certainly be used.
Moving machines between the hosts is fulfilled by the exchange of one-time keys, which are generated and served by vCenter server, rather than KMS.
In general, encryption of virtual machines and vMotion migrations is great stuff, but keep in mind you will need external KMS server for that.
Also, recently VMware published another interesting technical paper VMware vSphere encrypted vMotion architecture, performance, and best practices” on different aspects of mechanism of virtual machines encrypted migration between the hosts.
Experiments described in the open document have proven the following:
- vSphere 6.5 Encrypted vMotion migration works almost with the same speed vMotion does
- CPU encryption load is low due to the optimizations made in the vMotion code
- vSphere 6.5 Encrypted vMotion is the same reliable as regular vMotion
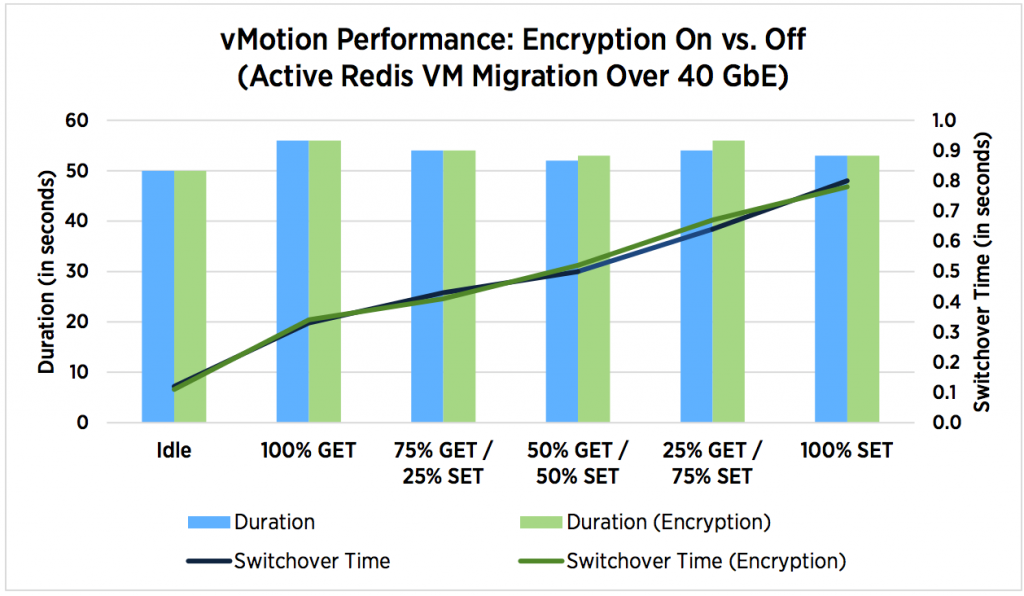
For example, let’s see the testing results of vMotion hot migration performance in enterprise infrastructure for virtual machine with Redis database manager.
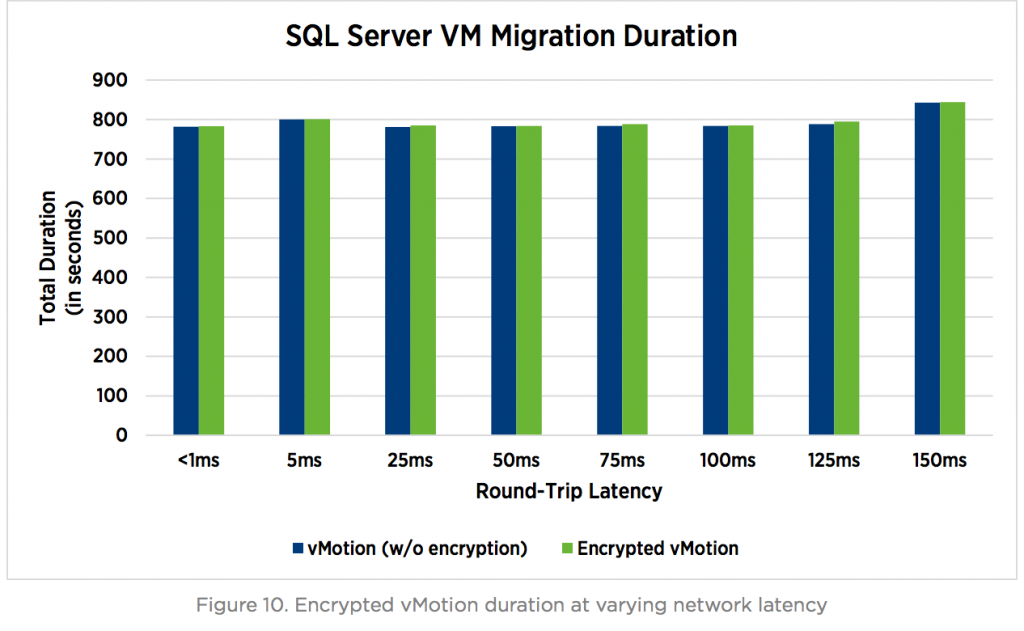
Here is Microsoft SQL Server virtual machine migration for a long distance at varying network latency, which depends on datacenters location:
There are several more interesting pictures in the document, but there is only one conclusion – encrypted vMotion almost doesn’t affect virtual infrastructure performance.
- VMware vSphere 6.5 – What to be aware of before upgrade?
- Recent news for VMware Tools packages for VMware vSphere 6.5