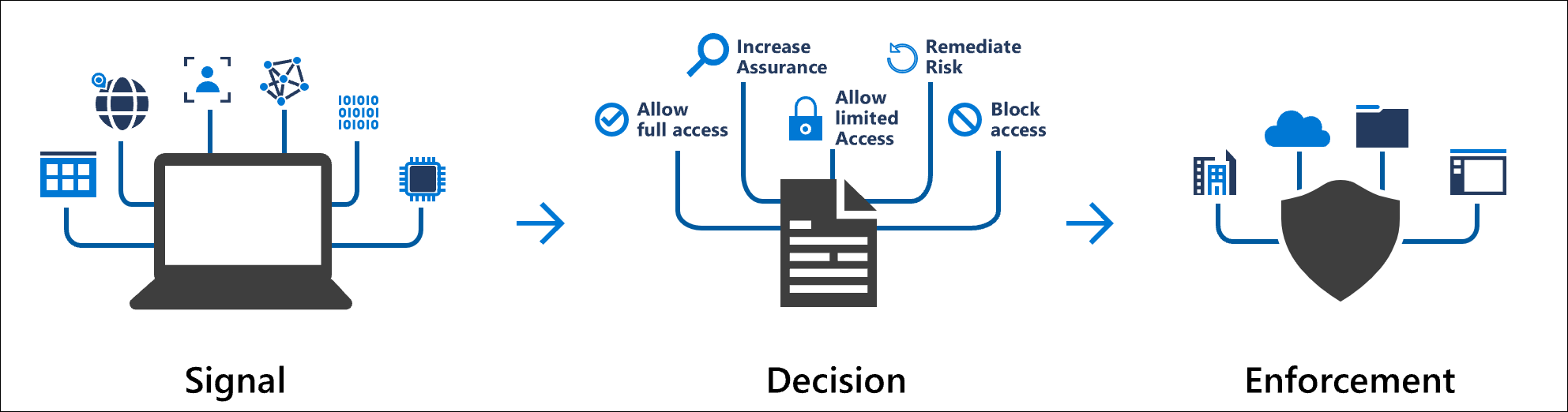
Conditional Access is an Azure Active Directory Premium P1 feature that collects signals and make a decision on the access level to the applications registered in Azure AD. The decision can be to block / allow access or even to provide a limited access to the applications.
Conditional Access leverage several signals to make decisions. These signals can be:
- The user IP location
- The state of the devices based on device compliancy
- The risky user or risky sign-in state based on Azure AD Identity Protection
- The group membership or the user Azure AD role
- Etc.
Conditional Access can be used with Microsoft Cloud App Security in order to gain real time visibility over activities in the cloud environment. For example, you can deny to save or print document if the user is connected to Office 365 with his personal device. This week Microsoft has announced also that Conditional Access can be used with M365 compliant features: you can request MFA if you open sensitive information.
To provide an overview of Conditional Access, I’ll show how to enforce MFA to users who belong to Global Administrator role when they connect to Azure Portal.
Create the Conditional Access
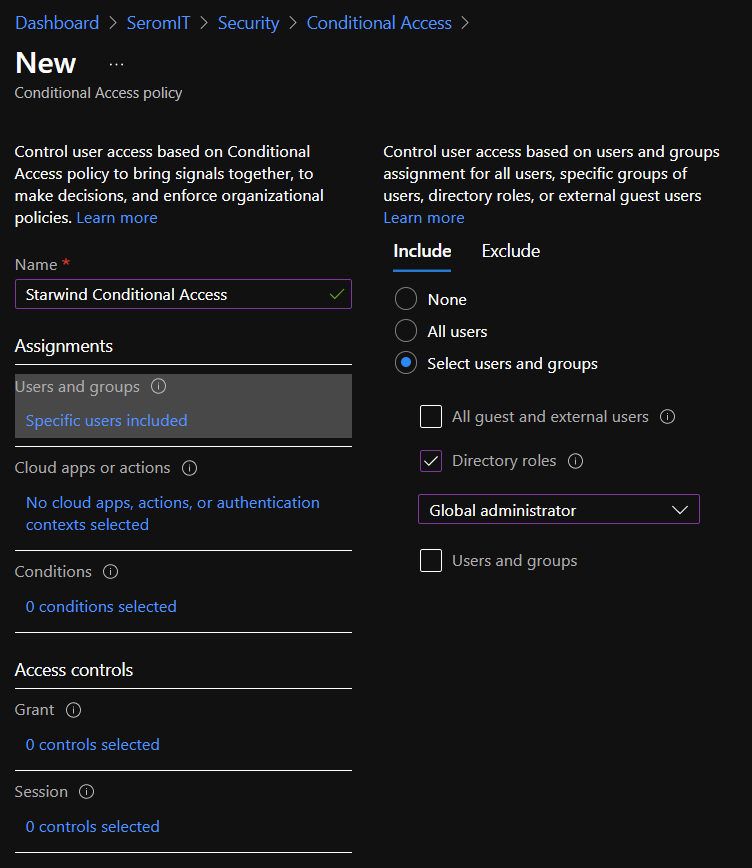
To manage Conditional Access, you need an Azure AD Premium P1 at least. Then navigate to your Azure AD | Security | Conditional Access. From there you can click on New Policy. First provide a name to your conditional access then select Users and Groups. In this tab, you can select who will be included or excluded from this conditional access. You can include or exclude all users, a specific user or group, a specific azure AD role or guests and external users. For this example, I include Global Administrator.
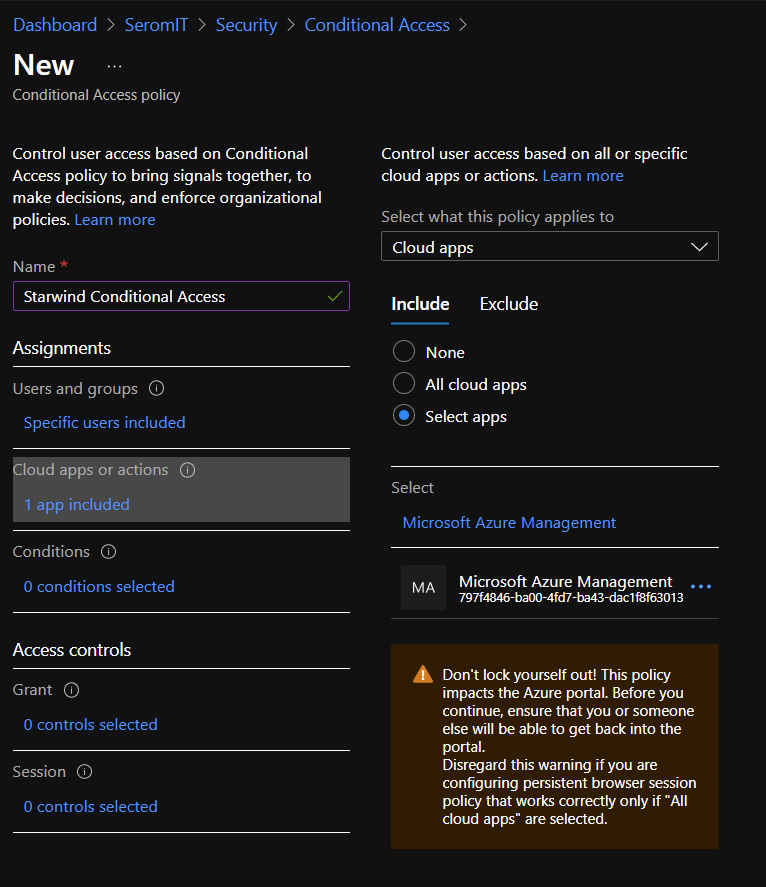
Next select Cloud Apps or Actions section. From there you can include or exclude cloud apps which will be enforced by conditional access. Cloud apps are applications registered in Azure AD. Because I just want to enable MFA for Azure Portal I chose Select Apps and I selected Microsoft Azure Management
Next select the conditions section. From there you can select signals that will be part of the decision. You can select the location, the user and sign-in risky level etc. Here I configure nothing because I want MFA applied to all Global Administrator.
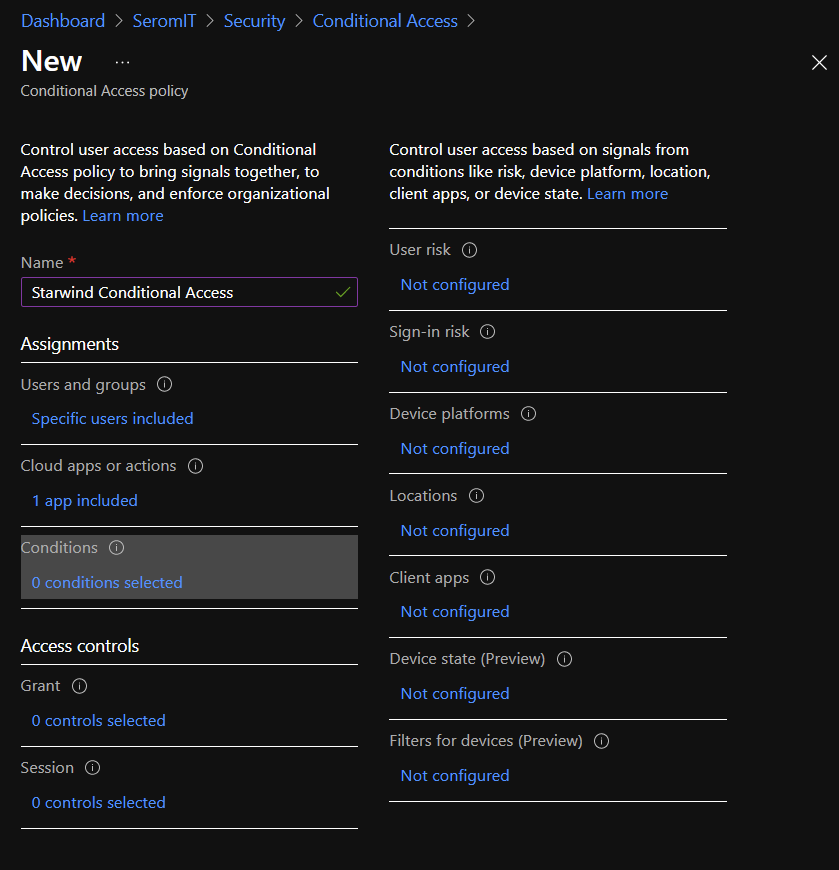
Next in Grant section, I enable Require Multi-Factor Authentication. As you can see you can also require that device is compliant or hybrid Azure AD joined
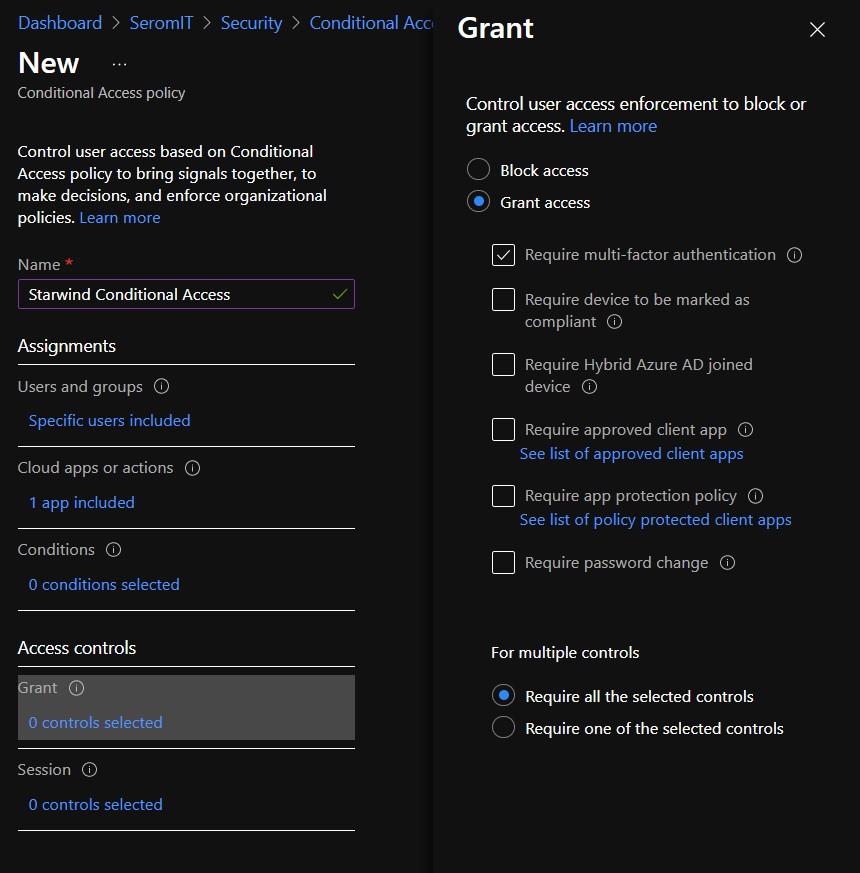
In Session section you have some control on the session. You can:
- require to user to sign-in again depending on the frequency you set,
- allow a user to remain signed-in even if he closes his browser and open it again,
- Enforce App Control by using custom policy in Cloud App Security
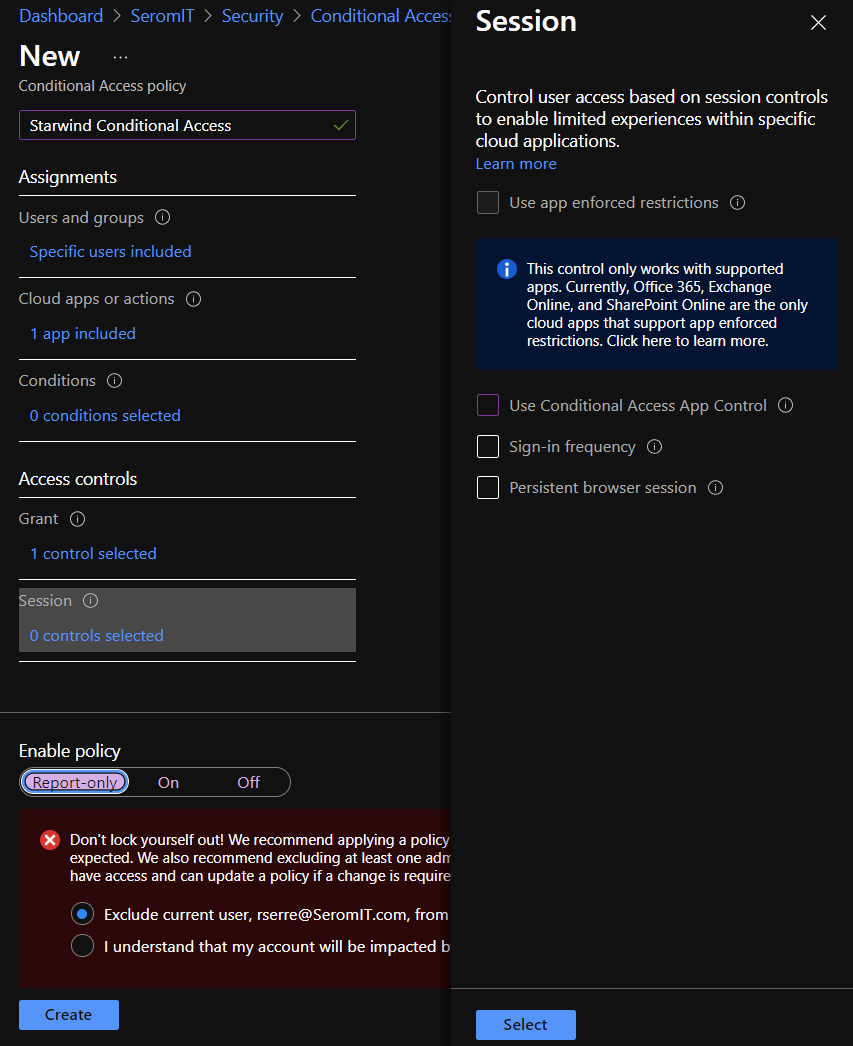
Finally, to enable the conditional access, select Enable Policy On and click on Create. As you can see you have a warning that asks you to check if you don’t lock yourself. The first time you do this configuration, be sure you have a global administrator account that is not impacted by this conditional access. When you have tried your conditional access, you can remove this account.
Try the conditional access
To try it, I open a browser in private and I navigate to the azure portal. When you specified credentials, you should get a request to approve sign in by SMS or Microsoft Authenticator depending on what you chose when you configure MFA.