StarWind enables users to set access restrictions to initiators.
Note: A Default Access Policy will be applied to all newly created targets. Individual access rights can also be set.
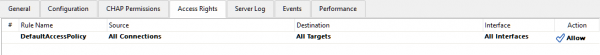
By default, if no HA devices are configured on the server, a StarWind VSAN server has only one access rule added: DefaultAccessPolicy. This rule allows for all connections from all servers to all targets via all network interfaces and does not restrict access to any target or interface in any way. The Access Rights view for a standalone StarWind device is demonstrated in the screenshot below.
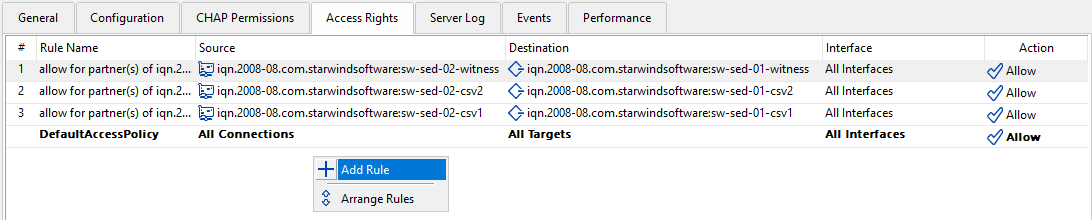
When HA devices are created on the StarWind VSAN node, the ACL rules for partner connections are added automatically as shown below.
To set the access rights:
1. Select a connected StarWind server in the StarWind Management Console.
2. Navigate to the Access Rights tab.
3. Right-click the target and perform the required action:
- Add a new access rule
- Modify existing rules
- Remove access rules
- Arrange the rules
To add a new access rule:
1. Right-click the target and select Add Rule.
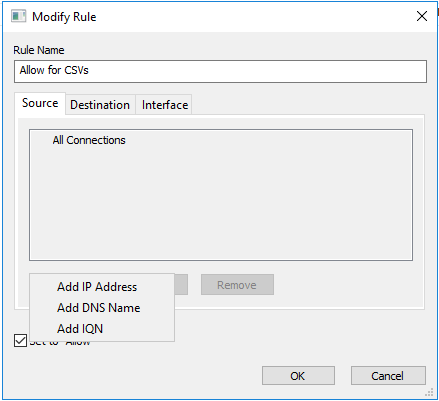
2. Enter a rule name and click Add to fill out the Source field.
3. Add the information for each of the servers that are expected to connect to the StarWind target and specify either an IP address, DNS name or unique IQN for the servers.
Select the appropriate option, specify the required data and click OK.
Note: Use Modify to change the source settings and Remove to delete specified connections, targets and interfaces.
NOTE: To obtain the server IQN, open Microsoft iSCSI Initiator and navigate to the Configuration tab (Windows Server):
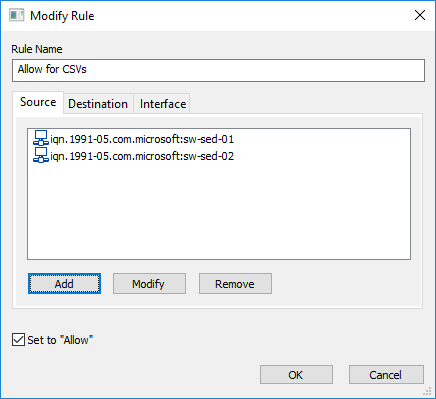
The Source tab will look similar to the screenshot below:
4. If needed, select the Set to Allow check box.
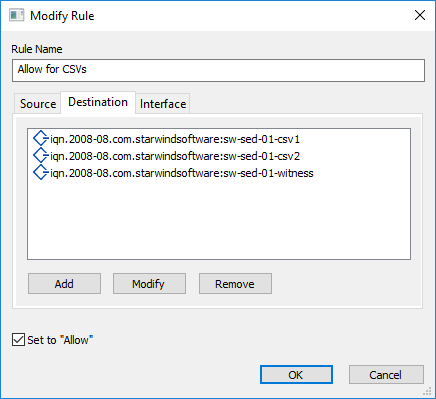
5. Go to the Destination tab, click Add and select a target name from the drop-down target list. Click OK.
Note: Multiple targets can be configured within the same ACL rule. Also, all targets are allowed to be connected to if no target is set explicitly.
6. Select the Interface tab and click Add.
In the Interface tab, specify the IP address(es) allowed to accept connections to the StarWind VSAN target.
By default, all interfaces are allowed to be used in the newly created rule. If only dedicated interfaces are intended to be used for connecting to the targets, select the required interfaces from the dropdown list in the popup window. Click OK.
NOTE: The loopback address 127.0.0.1 should be added for the Hyper-V hyperconverged scenario. For any other configuration scenario, this IP address is not required.
7. Click OK to add a new access rule.
8. Once all required rules are configured with the Allow checkbox selected, all other connections can be restricted. To perform this, double-click the DefaultAccessPolicy rule and uncheck the Set to “Allow” checkbox. This will block all connections that are not explicitly configured in the rules preceding DefaultAccessPolicy. Press OK to confirm.
9. To apply the newly configured rules to all iSCSI sessions and make sure that only necessary sessions are connected, restart the StarWind VSAN service on the node where changes have been introduced. If an HA setup is used, make sure that similar rules are configured on the partner server(s).
To modify an existing rule:
1. Right-click the access rule you want to change and select Modify Rule.
2. Click OK to confirm the changes.
To remove an access rule:
1. Right-click the access rule you want to delete and select Remove Rule.
2. Click Yes to confirm the deletion.
To change a rules order:
1. Right-click the main area of the Access Rights tab and select Arrange Rules.
2. Select a rule and click the Up or Down buttons to change its order.
3. Click OK.