Last week, Microsoft released Azure Bastion in GA. This feature enables us to connect to VMs (Linux or Windows) through Azure Portal.
We all know that connecting production VMs directly to the Internet via a public IP is a huge concern from a cybersecurity standpoint. Therefore, usually, all critical VMs don’t have public IPs, and they are managed either from a site-to-site VPN or a console VM that holds a public IP. In both cases, managing your Azure VMs is not easy since cybersecurity is a concern.
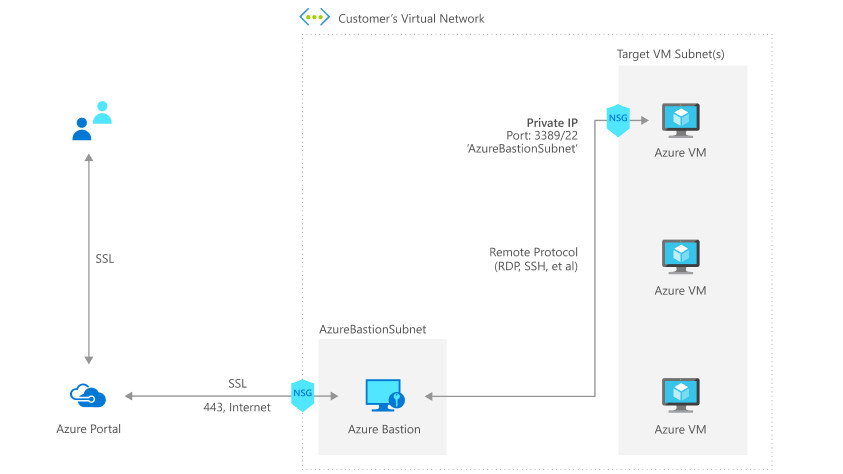
Thanks to Azure Bastion, you don’t need a site-to-site VPN or a console VM to manage all your Azure VMs anymore. Azure Bastion is a PaaS connected between the Internet (through a public IP) and a virtual network. When this service is enabled, you can connect to your VMs through Azure Bastion. By doing this, you will be able to open a console RDS or SSH directly inside the Azure Portal. In this topic, we will see how to deploy and use Azure Bastion.
Requirements
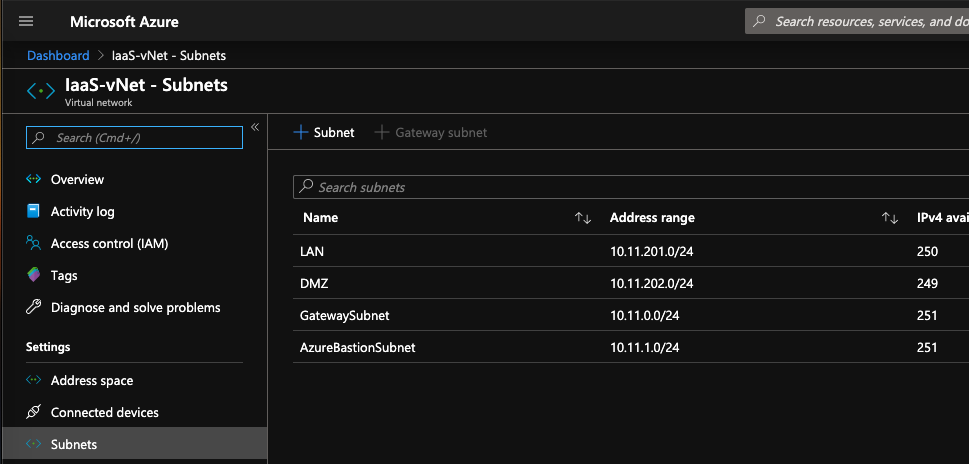
Before deploying Azure Bastion, you need a virtual network with a subnet called exactly AzureBastionSubnet.
Deployment
To deploy Azure Bastion, open the Azure Marketplace and search for Azure Bastion.
Then click on Create to start the process of Azure Bastion deployment.
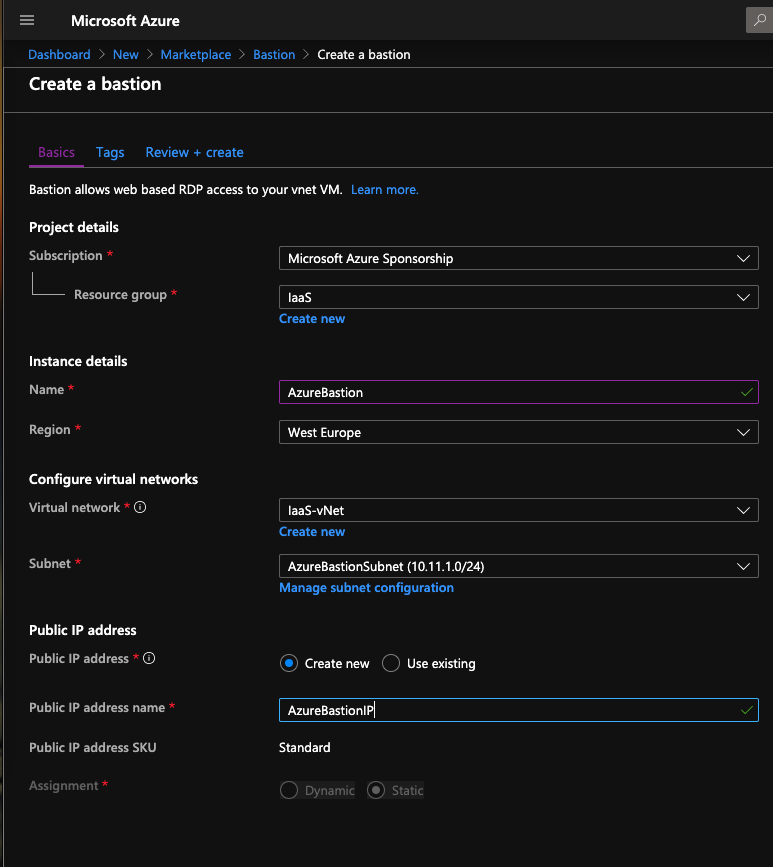
Next, specify the following information:
- Name: provide a name for the resource
- Resource Group: choose a resource group where Azure bastion will belong
- Region: a few regions are currently available, select a region that fit your needs
- Virtual Network: select the virtual network where you created AzureBastionSubnet
- Subnet: Select AzureBastionSubnet
- Public IP Address: you can use an existing static public IP or you can create a new one.
At the end of the process, you can review the settings you specified. If all is good, just click on Create.
Connect to VM through Azure Bastion
Now, when you click on Connect in an Azure VM, you have an additional option called Bastion. In order to get this option, the Azure VM must belong to the same virtual network as the Azure Bastion.
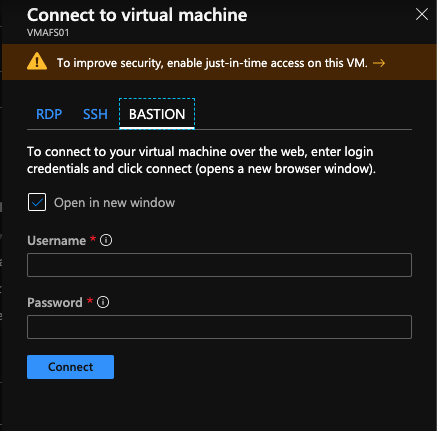
For a Windows VM, specify the credentials to connect. You can open the console in a new tab or directly inside the Azure Portal:
For a Linux VM, you will be asked to specify SSH credentials instead of Windows credentials.
Session logs
Azure Bastion is now able to log an active RDS / SSH session. You can check who is connected and where. You also have the option to disconnect them.
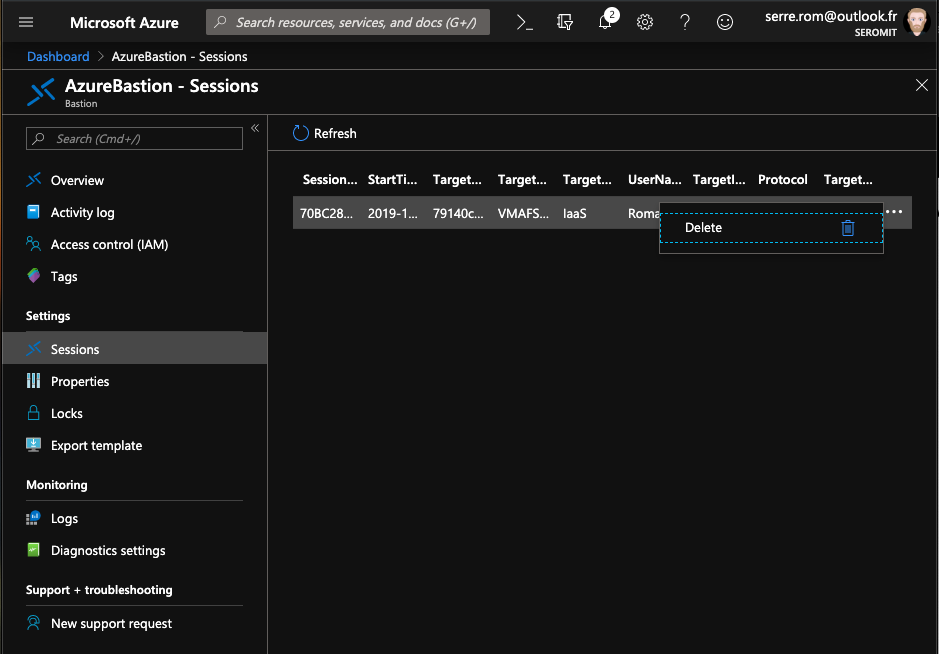
Moreover, Azure Bastion can be connected to a Log Analytics workspace to centralize event logs.




