Fairly often, unexperienced end users get caught on some website which uses malware or newly some crypto miners which uses up to 70% of your PCs power to mine a cryptocurrency for some hackers. So how to protect at best those end users?
One of the new ways is to use Microsoft’s built-in utility called Windows Defender Application Guard (WDAG).
The tool is designed for W10 Enterprise version only and the system has to support to run Hyper-V role.
Microsoft introduced a new layer of defense-in-depth protection which uses Hyper-V for isolation purposes.
Quote:
What is Windows Defender Application Guard and how does it work?
Designed for Windows 10 and Microsoft Edge, Application Guard helps to isolate enterprise-defined untrusted sites, protecting your company while your employees browse the Internet. As an enterprise administrator, you define what is among trusted websites, cloud resources, and internal networks. Everything not on your list is considered untrusted.
If an employee goes to an untrusted site through either Microsoft Edge or Internet Explorer, Microsoft Edge opens the site in an isolated Hyper-V-enabled container, which is separate from the host operating system. This container isolation means that if the untrusted site turns out to be malicious, the host PC is protected, and the attacker can’t get to your enterprise data. For example, this approach makes the isolated container anonymous, so an attacker can’t get to your employee’s enterprise credentials.
System Requirements
- Windows 10 Enterprise 1709 (Fall Creators Update) or higher
- A computer which supports Hyper-V
- A 64-bit computer with minimum 4 cores is required for the hypervisor and virtualization-based security (VBS)
- Extended page tables, also called Second Level Address Translation (SLAT)
- One of the following virtualization extensions for VBS:
- Intel VT-x
- AMD-V
- Microsoft recommends 8GB RAM for optimal performance
- 5 GB free space, solid state disk (SSD) recommended
- Input/Output Memory Management Unit (IOMMU) support is strongly recommended
- Microsoft Edge and Internet Explorer
How to Install/Uninstall
Depending on the mode (if you’re in the domain environment or on the isolated computer). You can basically install this tool two different ways:
- Configure and activate via is configured using an Enterprise devices management tool like System Center Configuration Manager, Microsoft Intune, or others.
- Standalone activation via PowerShell or via Add/Remove Windows Features User interface.
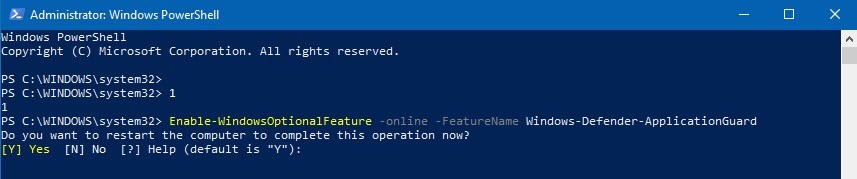
Installation via PowerShell:
Open an elevated PowerShell Window and type:
Enable-WindowsOptionalFeature -Online -FeatureName Windows-Defender-ApplicationGuard
Installation via UI:
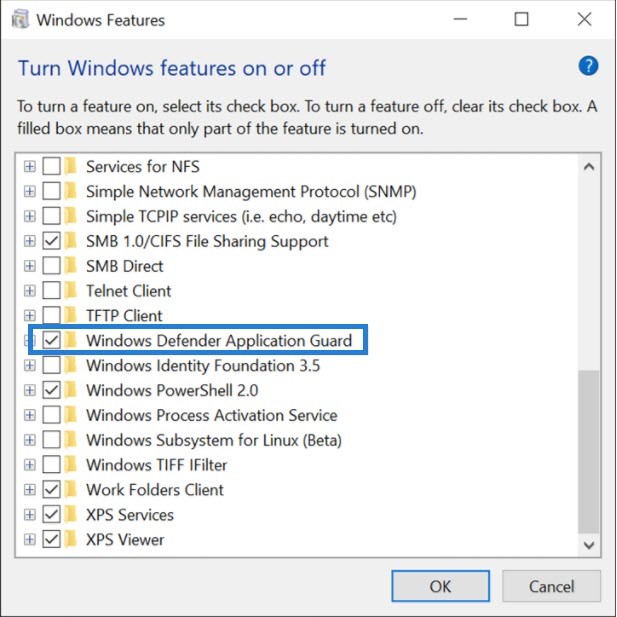
I know that Microsoft has changed the way we Install/Uninstall programs on W10, but the old way of doing it is still present.
On W10 computer, open a classic control panel by typing “control panel” in the search window. Then click Programs and Features (as in W7) > Turns Windows Features On and Off.
Optionally:
Use this command which you can type into an elevated command prompt window:
rundll32.exe shell32.dll,Control_RunDLL appwiz.cpl
Then follow the steps as above.
You’ll need to restart the computer to complete the installation.
Note: I’m assuming that the Hyper-V role is already installed on the computer you’re testing the feature with. If not, please activate the Hyper-V role as well.
Once you’ve restarted the device, you’ll need to open Edge browser and there will be an option in the menu to open a New Application Guard window.
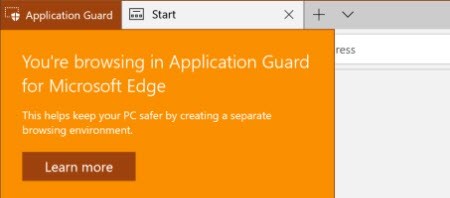
When you open a new Application Guard window for the first time, you’ll see a splash screen saying that WDAG will take a few minutes to prepare.

Once done, you’ll see a message saying that “You’re browsing in Application Guard for Microsoft Edge” message.
The underlying Hyper-V role is “sandboxing” the environment making sure that the underlying physical computer won’t get infected with a malware or exploited with a crypto miner malware.
Any websites you visit, files you download, or settings you change while in this isolated environment are deleted when you sign out of Windows, wiping out any potential malware.
You might think that within this new environment, you’ll have to re-create your favourites, or cookies or saved passwords. But no.
All the data such as your favourites, cookies, and saved passwords will be persisted across Application Guard sessions. The persisted data will not be shared or surfaced on the host, but it will be available for future Microsoft Edge in Application Guard sessions.
WDAG needs a device with a 64-bit CPU, Second Level Address Translation (SLAT), and VT-x (Intel) or AMD-V.
Additionally, WDAG has quite a performance impact. And because of the performance impact, Microsoft recommends 8GB of RAM, which is pretty common those days anyway.
You should also activate VT-D within your BIOS, which is a manual step.
Also, another (good) security feature is that you cannot download files from the isolated Application Guard container to the host PC. But, as a workaround, you do have the option of using “Print as PDF” or “Print as XPS”.
Another thing that might turn you down to use WDAG on your computer is the fact that it is not possible to Install and use VMware Workstation or Player, as WDAG uses Hyper-V role, and you cannot have both on the same computer.
Other solutions than WDAG?
Yes, there are, but not isolating the rest of the operating system from malware. Google Chrome has an experimental feature. This feature makes to run websites in their own process to block cross-site scripting attacks. But as being said, it doesn’t protect the operating system.




