When time comes to deciding whether to go with vSphere Distributed Switch or Cisco Nexus 1000v it is hard to tell which product is superior and you find many different and quite contradictory opinions.
While quite often it is the political decision based on the answer to the question “Who is going to manage the virtual networking?” there are many other aspects you, as an infrastructure designer, should be aware of.
Recently VMware announced End of Sale of Nexus 1000v which caused some confusion amongst clients. I know customers who were pretty sure Cisco discontinued Nexus 1000v, but rest assured, Cisco is still fully committed to continue development of virtual networking and to support Nexus 1000v in the latest and future versions of vSphere.
When time comes to deciding whether to go with vSphere Distributed Switch or Cisco Nexus 1000v it is hard to tell which product is superior and you find many different and quite contradictory opinions.
While quite often it is the political decision based on the answer to the question “Who is going to manage the virtual networking?” there are many other aspects you, as an infrastructure designer, should be aware of.
Recently VMware announced End of Sale of Nexus 1000v which caused some confusion amongst clients. I know customers who were pretty sure Cisco discontinued Nexus 1000v, but rest assured, Cisco is still fully committed to continue development of virtual networking and to support Nexus 1000v in the latest and future versions of vSphere.
In this article I will try to focus on main differences between solutions. It won’t cover every single feature, but will give you enough food for thought to make an educated choice.
Feature comparison, Configuration Maximums
Back in 2009, when Distributed vSwitch was first introduced in vSphere 4 it lacked a lot of important features compared to Nexus 1000v.
There was no support of Link Aggregation Protocols, there was scarce choice of load balancing hashing algorithms and no presence of monitoring and troubleshooting tools like Netflow or Port Mirroring, but it was still good enough to automate networking provisioning for ESXi hosts and virtual machines.
The Cisco Nexus 1000V was introduced almost at the same time and provided significantly richer set of capabilities while delivering similar network configuration, security policies and tools to physical and virtual servers, which I guess tipped the scale in favor of Cisco product.
At the current moment the vSphere Distributed Switch in vSphere 6 is pretty mature and is on par with most of the functionality provided by Nexus 1000V Essential edition. I think that’s one of the main reasons why VMware ceased selling Nexus 1K and officially recommends to move to vDS.
But let’s have a closer look at the feature differences.
With Cisco Nexus 1000V you get the following benefits that vSphere Distributed Switch does not deliver:
- DHCP Snooping – improves the security of a DHCP infrastructure by determining traffic sources are trusted or not and by maintaining dynamic table of hosts’ mac addresses, leased IP addresses, vlans and associated interfaces.
- IP Source Guard – provides source IP address filtering using information in DHCP snooping database.
- Dynamic ARP Inspection – monitors ARP packets on untrusted ports to validate IP to MAC bindings.
- VxLAN support – Layer 2 network isolation technology for network virtualization
- Cisco TrustSec SGA support – allows organizations to enforce identity-based network access
- Cisco VSG support – multitenant, stateful, distributed firewall enabling microsegmenation and zone based policy enforcement.
- Supported Integration with other virtual Services:
- ASA 1000v
- vWAAs
- CSRv 1000v
The first three features are used quite often in physical environments where the risk of getting malicious computer connected to the network is somewhat higher. In virtual world they seem to be beneficial in multitenant environments where vSphere Administrator does not fully control tenants’ virtual servers.
Cisco Virtual Security Gateway (VSG) is available in Advanced Edition of Nexus 1000v only. In a way it is functionality comparable to vSphere NSX.
The remaining features have to be complemented by virtual appliances that are bought separately.
The good thing is that all these features are consistent across virtual and physical Nexus switches.
On top of that I would add more advanced troubleshooting with CLI in Cisco Nexus switches.
Finally, Nexus 1000v works on different types of hypervisors which makes it easier for Networking team to support multi-hypervisor environments or simplifies migration from one hypervisor to another.
vDS can brag about the following capabilities Nexus 1K does not have:
- Load Based Teaming also known as “Route based on physical NIC Pro-actively monitors and redistributes network bandwidth across different physical links. It does not require any Link Aggregation Protocols, which makes physical switch configuration pretty simple.
- Multiple TCP/IP stacks – simplifies routing and IP address management with a dedicated default gateway for different types of traffic.
- Cross vCenter vMotion – allows live migration VMs between different datacentres.
- Network Health Check – provides proactive monitoring of common configuration issues and automatic roll-back in case of misconfiguration of the management network.
Unfortunately, there is no vDS command line interface comparable to Nexus CLI. Apart from GUI configuration you can either take advantage of PowerCLI vDS commandlets. Alternatively, there are ESXi host level commands esxcli or esxcfg, but none of them is as easy and powerful as Nexus CLI.
Comparing configuration maximums of two virtual switches you can notice that historically Cisco Nexus 1000v dragged some limitations from the physical platform, but these numbers have been constantly improved. The latest versions of vDS and Nexus 1K have configuration maximums that are more than sufficient for most of the companies.
Deployment
vDS is a part of vSphere so all you need to enable it is an Enterprise Plus license.
Nexus 1000V installation requires deployment of two VSM virtual appliances and installation VEM on each of the host afterwards. The VEM installation can be automated using vSphere Update Manager or PowerCLI and does not require restarting hosts.
Upgrade
The vDS upgrade process is as simple as possible. You basically have to press the upgrade button and choose to which level you want to upgrade. The upgrade of a distributed switch is a non-disruptive operation which means the hosts and virtual machines attached to the switch do not experience any downtime.
If you still have outdated ESXi hosts in the vSphere farms vSphere Distributed Switch covers this risk with great backwards compatibility.
Cisco Nexus 1K upgrade requires significantly more time and efforts. There are quite a few steps in the manual upgrade process. You will also need to check compatibility matrix to ensure new Nexus 1K firmware is supported on with your vSphere.
Also, sometimes there is no direct upgrade path to the latest Nexus 1K release so you will have to upgrade to intermediate release first. Mixed versions of ESXi hosts make upgrade process more complicated.
In 2015 Cisco delivered Virtual Switch Update Manager appliance which aims to simplify and streamline the Nexus 1000V installation, migration and upgrade workflows.
High Availability
With vDS the Control Plane is built in vCenter. The standard vSphere HA protects from hardware failure. However, the OS level HA is available for Windows vCenter Server only and with quite complex implementation of Microsoft Failover Clustering.
Control Plane redundancy in Nexus is implemented through placing two Virtual Supervisor Modules on different physical hosts which protects Nexus 1000v from physical host failure as well. The OS level redundancy is achieved by Active/Passive configuration of VSM HA pair. The state and configuration remain constantly synchronized between the two VSMs to provide a stateful switchover if the active VSM fails.
However, both solutions depend on vCenter in equally so I would say it is a parity here.
The Data Plane of vDS and Cisco VEM are both parts of ESXi kernel which makes it possible to pass traffic even when VSM or vCenter is down, however, you can’t make any changes to the virtual switch configuration nor can you bring up new virtual machines.
Licensing
vSphere Distributed Switch requires Enterprise Plus License and delivers full feature set.
As long as all CPUs on the host are licensed there is not much to manage with regards to licensing.
Cisco Nexus 1000V switch takes advantage of Distributed vSwitch API which was developed jointly by Cisco and VMware, to provide advanced networking capability to virtual machines. It means that in order to run Nexus 1KV you need to possess vSphere Enterprise Plus license.
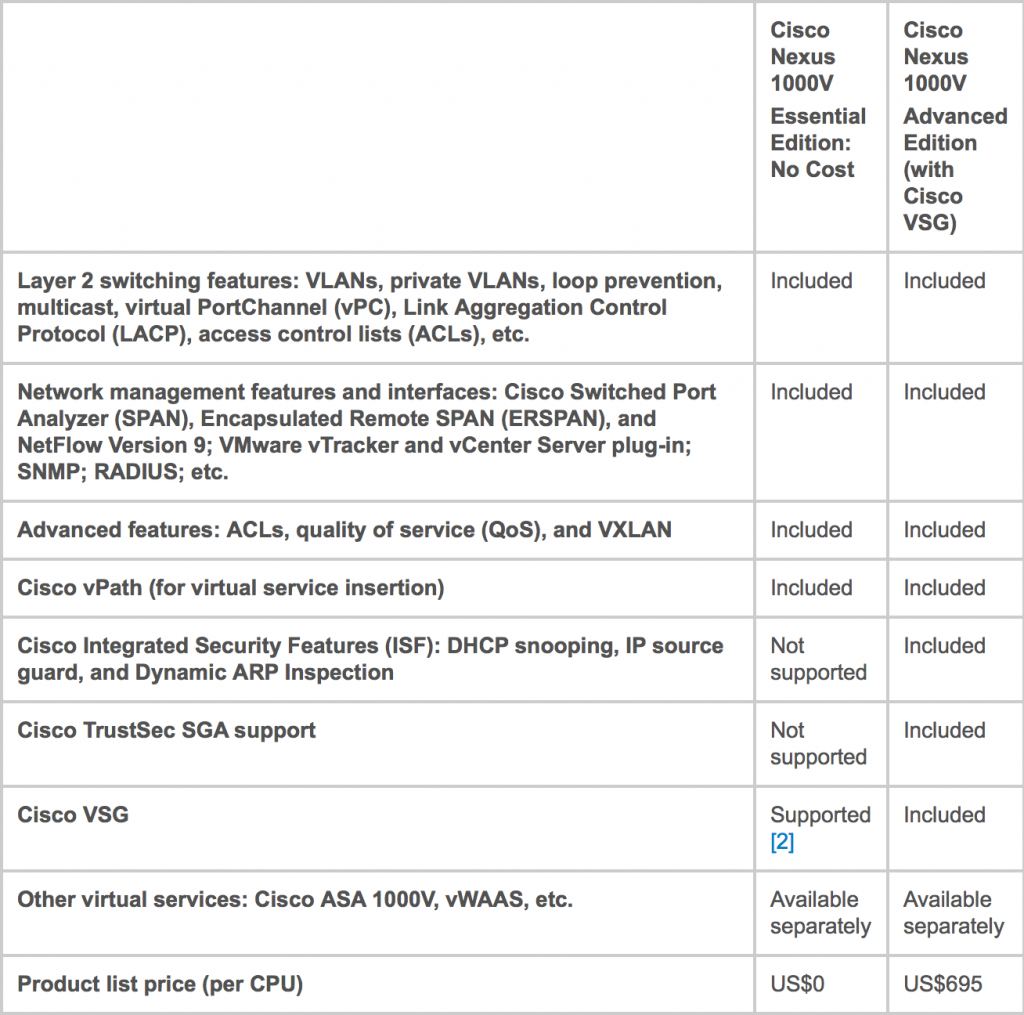
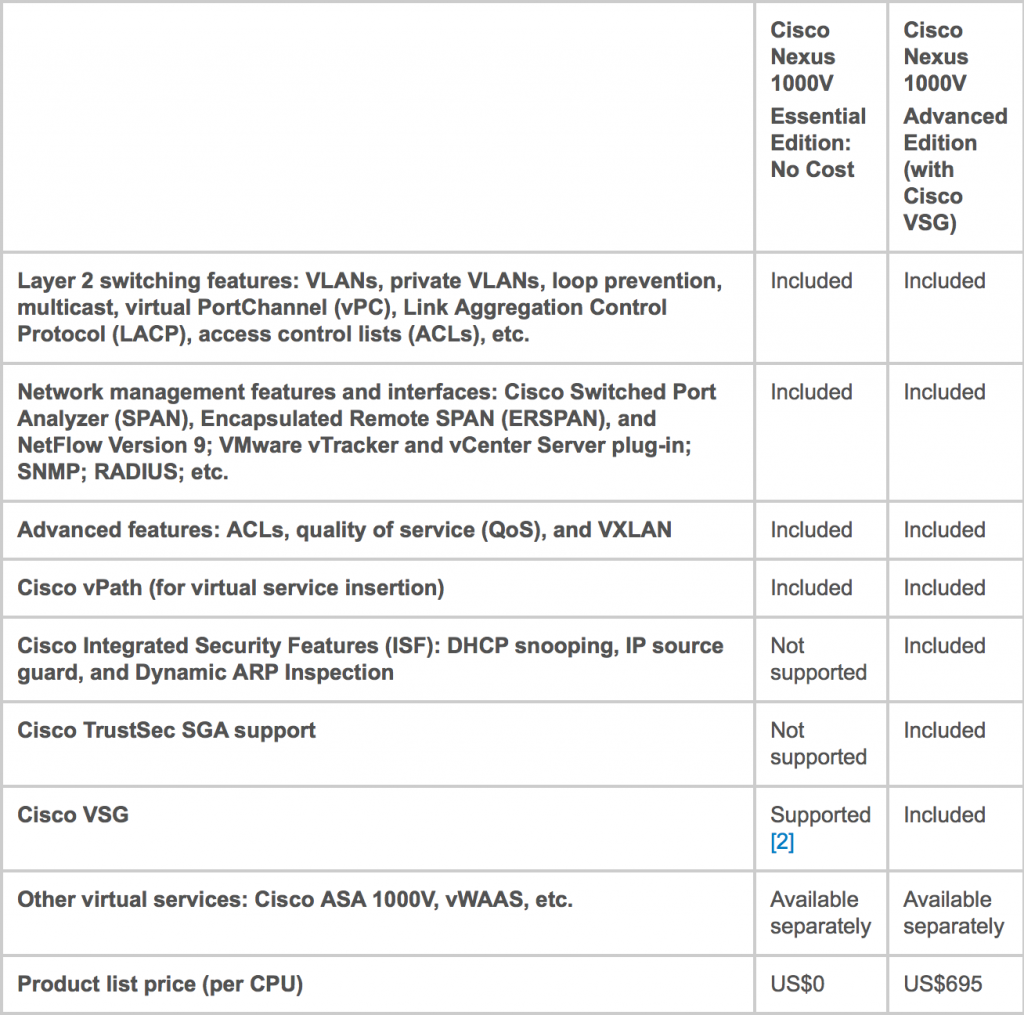
The Nexus 1KV comes in two flavors – Essential and Advanced Editions. Essential comes with a limited set of features, but it is completely free. Advanced edition delivers extra security features and integration with other Cisco virtual services.
The following table depicts difference between Essential and Advanced Editions
Suggested Retail price per 1 vSphere Enterprise Plus license is 3,495.00 USD. That price covers all features of vSphere, not only networking part of it.
Advanced Nexus 1000V license will add another 700 USD on top of that, however, not many infrastructures require extra features of Advanced editions and you can still enjoy separation of duties with Essential Edition.
Conclusion
Apart from everything we have already discussed there are other factors to be taken into consideration when making choice. You will have to think what kind of skills your team has and how big your teams are. You may also consider using credits from vendors to organize trainings to obtain required skill set.
Solutions interoperability is another thing to keep in mind when making the decision.
All in all, both products enable scalable and flexible network architecture while doing this in different ways.