As we often hear, “Security is not an option”. It’s why, today, I propose you to monitor weak password, On-Premises and in the cloud.
Weak password On-Premises
The documentation is available here: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad-on-premises
To start, download the 2 software, available here: https://www.microsoft.com/download/details.aspx?id=57071
Install the Azure AD Password Protection proxy on a server, On-Premises, who is member of the Active Directory. This proxy will communicate directly to Azure AD:
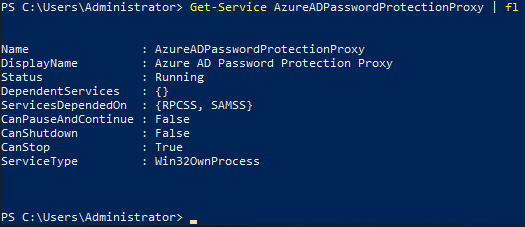
Verify that the service is running fine:
|
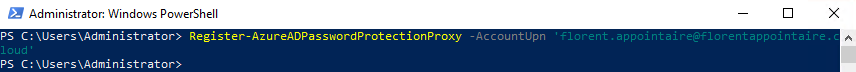
Now, we need to register our proxy, with our Azure AD, with the following command. It will ask you for the password and MFA. This account must be Global Admin of the Azure AD:
|
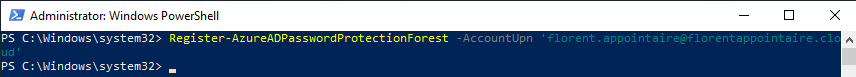
It’s time to register our AD forest with the following command. The account that executes the command on PowerShell must be at least, Enterprise Administrator:
|
Now it’s time to install the agent on Domain Controllers. Copy the binary on each DC, and execute the following command. It’s important to restart the Domain Controller to load correct DLLs:
|
The next step is to activate the On-Premises Password protection on the Azure console. Navigate to the Azure Portal, go to Azure Active Directory > Security > Authentication methods > Password protection:
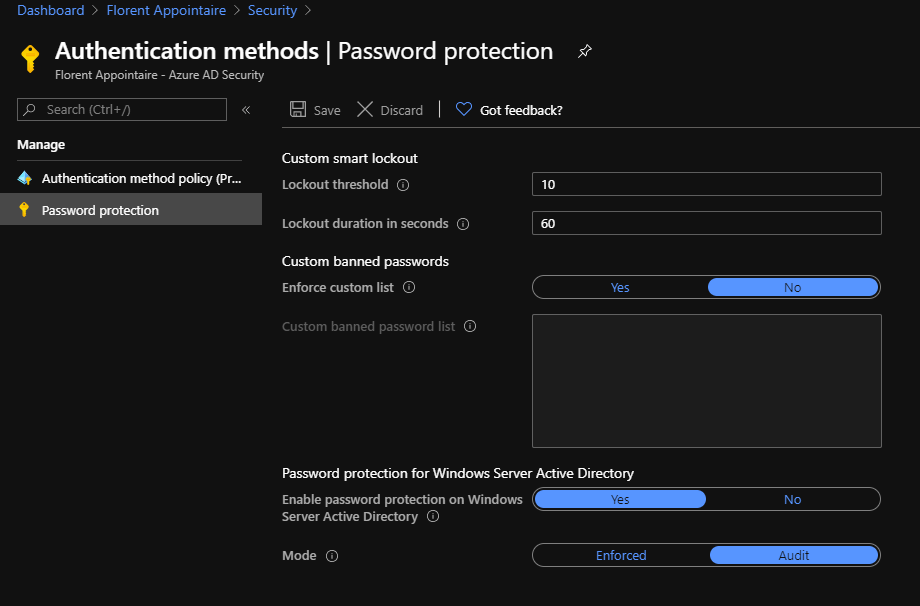
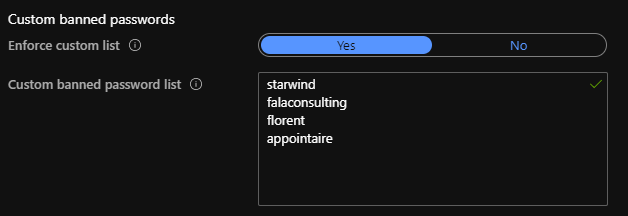
Here, activates the Password protection for Windows Server Active Directory. Currently, I’ll stay on Audit mode, to do not impact my users. You can also provide a list of banned passwords, for example to do not allow company name in the password:
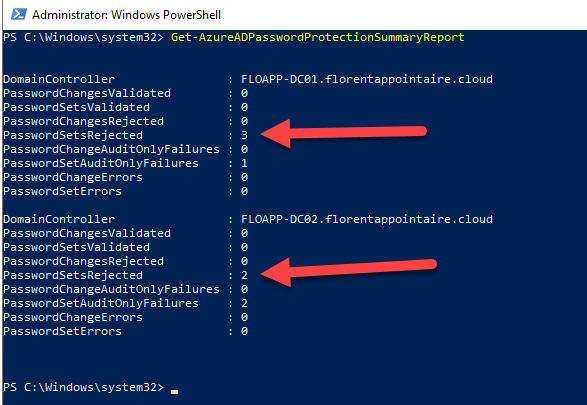
You can check, with the following command, a report of Azure AD Password Protect:
|
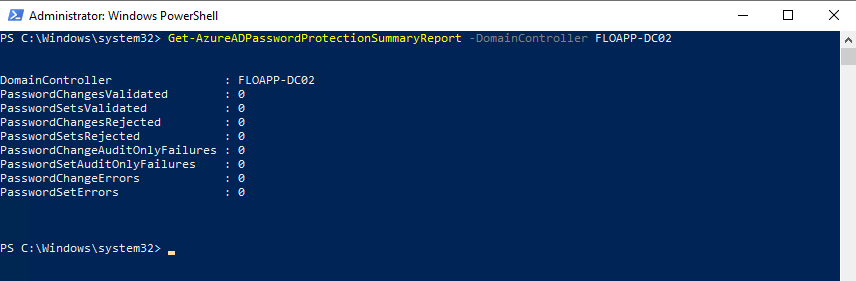
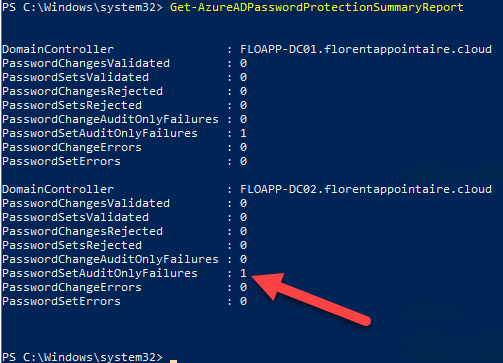
I changed the password for the Starwind account on my Active Directory, with a weak password. I checked again, and now, I’ve the PasswordSetAuditOnlyFailures parameter to 1:
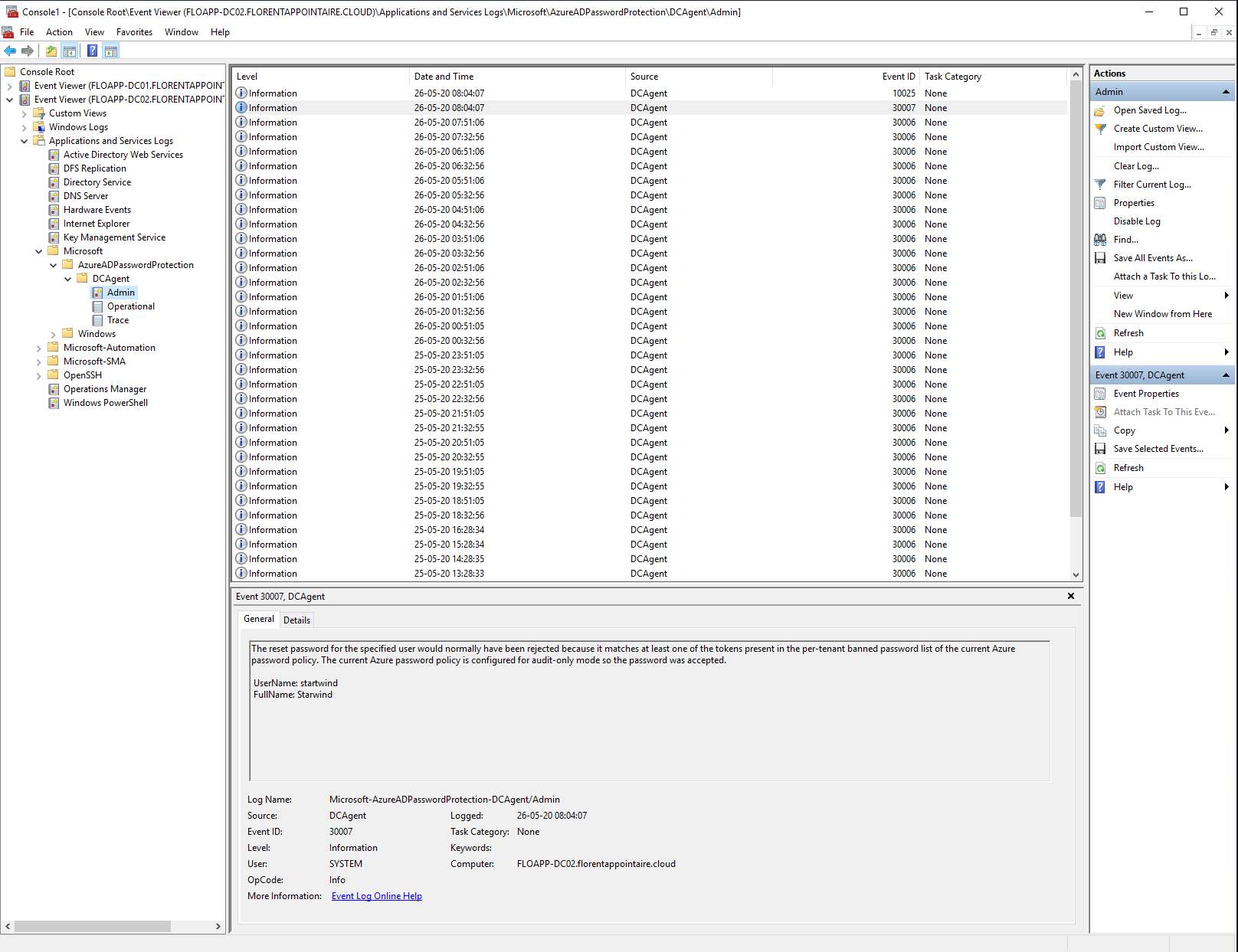
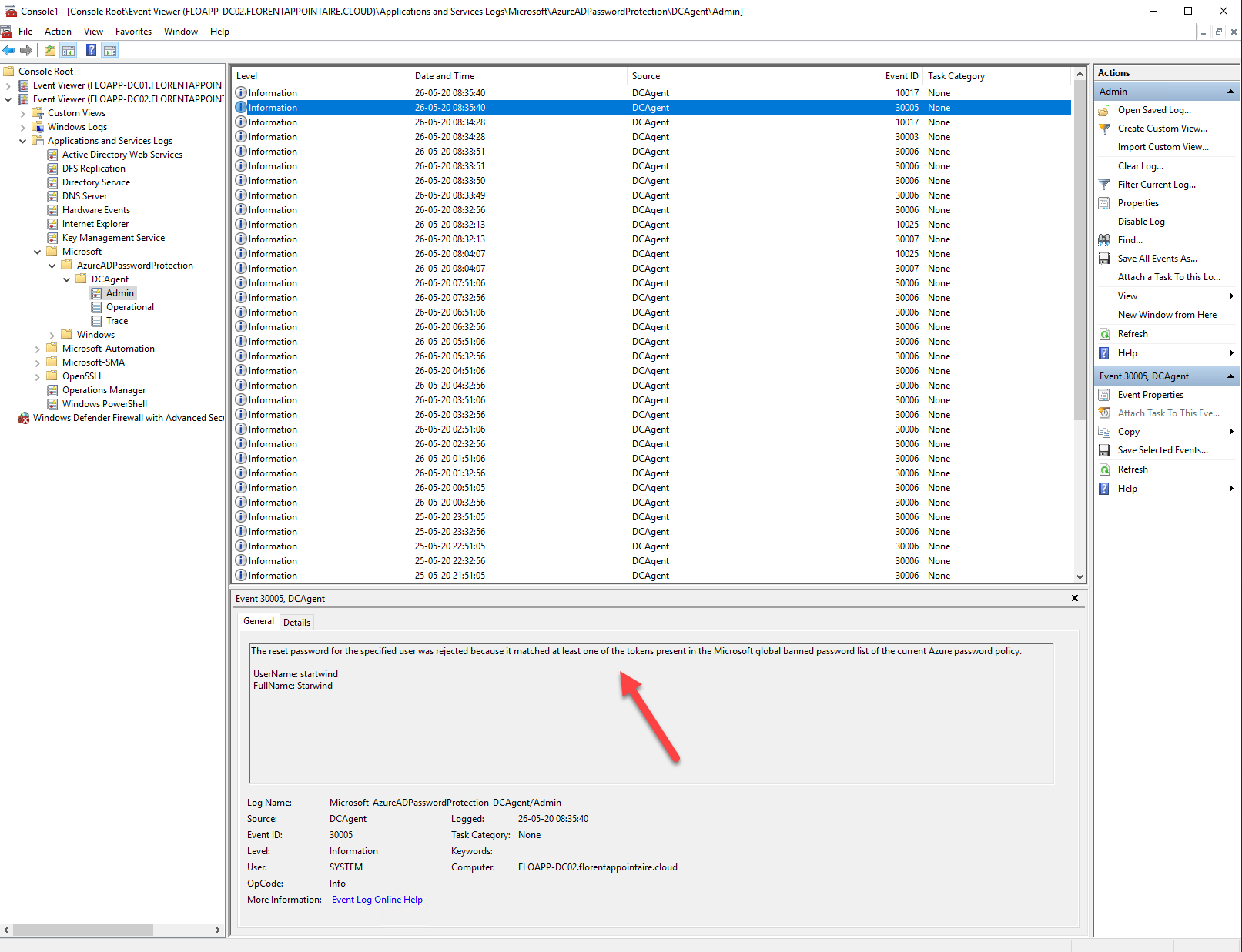
If I check in logs, I have the information that a weak password has been used. But, because I am in audit mode, it has not been blocked. These logs can be found under \Applications and Services Logs\Microsoft\AzureADPasswordProtection\DCAgent\Admin, in the Event viewer of one DC:
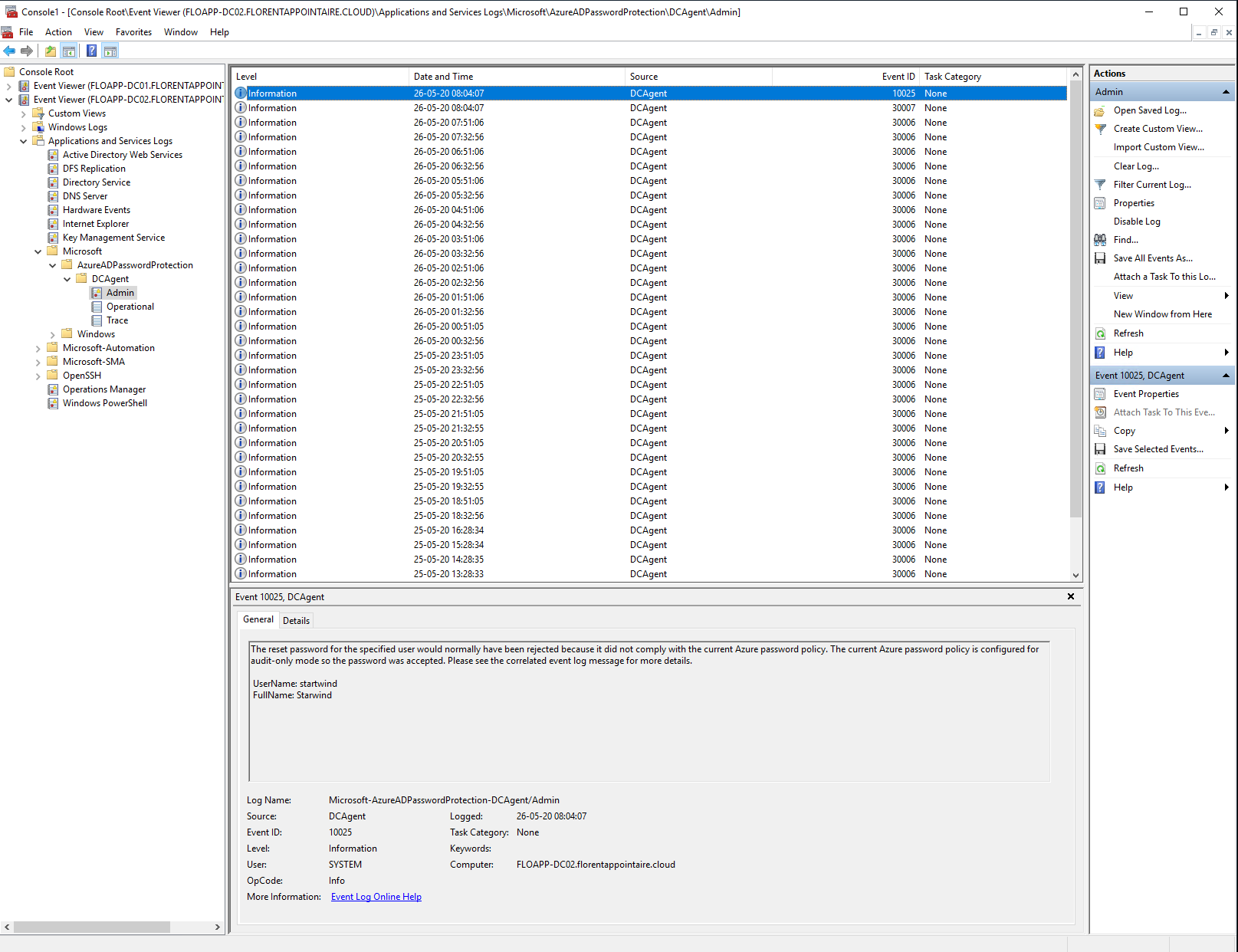
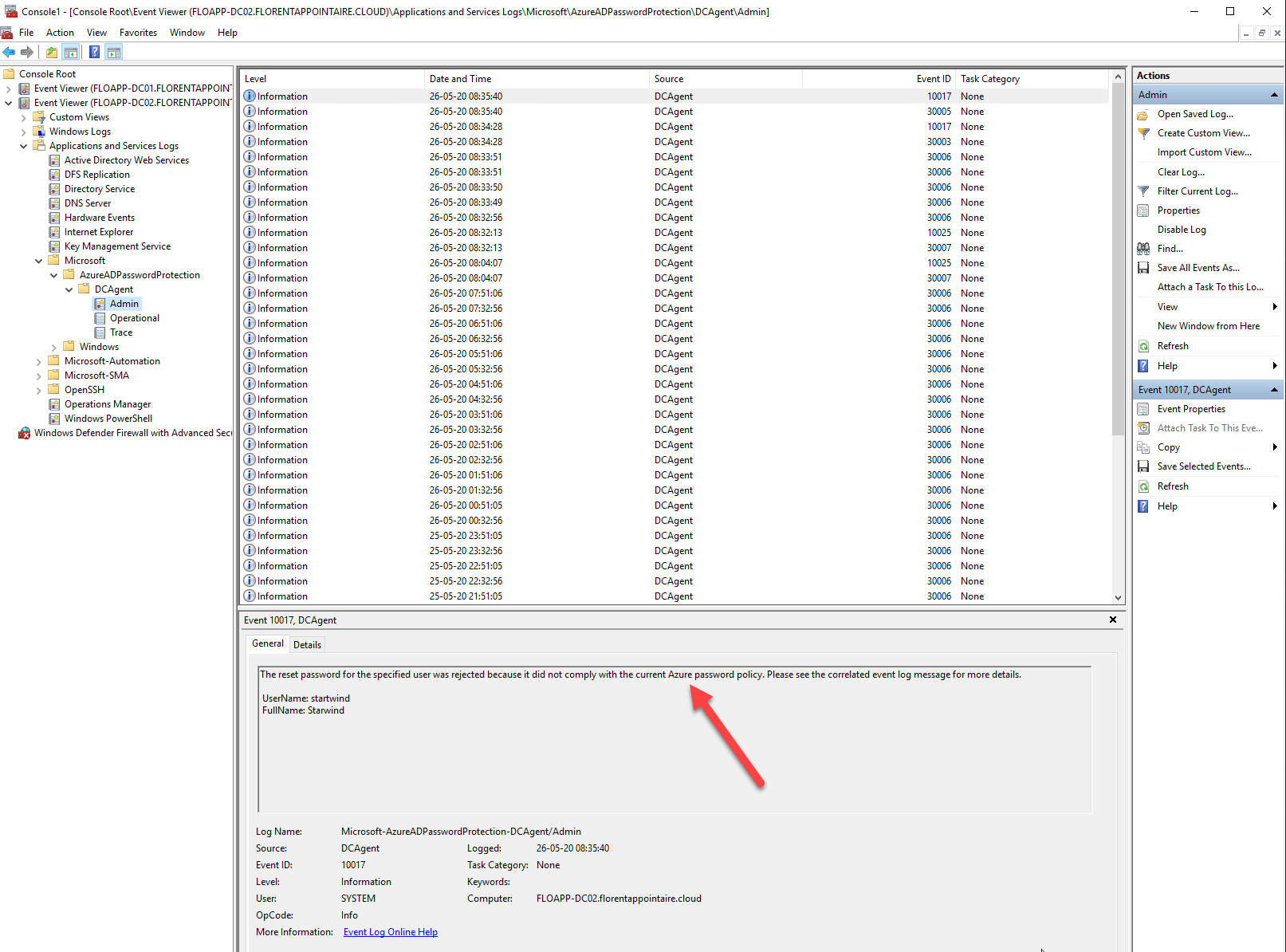
If I change the mode to Enforced, I have the following error:
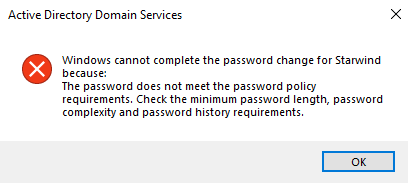
And it has been logged:
The only problem with this feature is that we can’t check which password has been defined by the user.
Weak password in the cloud
The documentation is available here: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad
If you only have cloud users, without On-Premises directory, you need to configure with the following. On the Azure Portal, go to Azure Active Directory > Security > Authentication methods > Password protection:
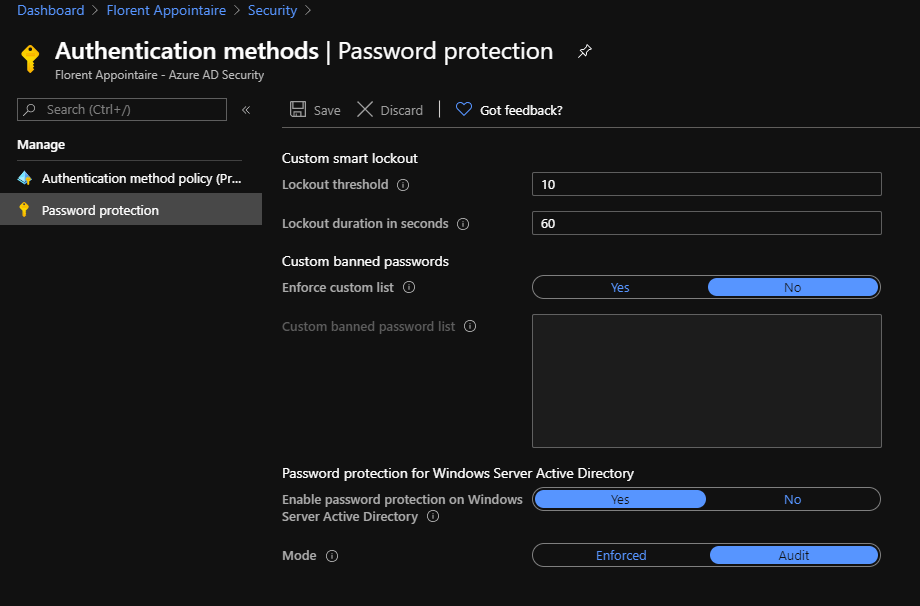
Choose the mode that you want to use and you can also provide a list of banned passwords, for example to do not allow company name in the password:
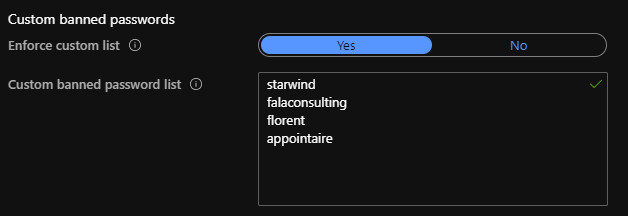
If you don’t use the custom list, the Azure AD Free will protect you. If you want to use a custom list, you will need an Azure AD P1/P2 license.
I created a new user, with a default password. During the first login, I had to change it. I tried a password in the password list, and had the following error:
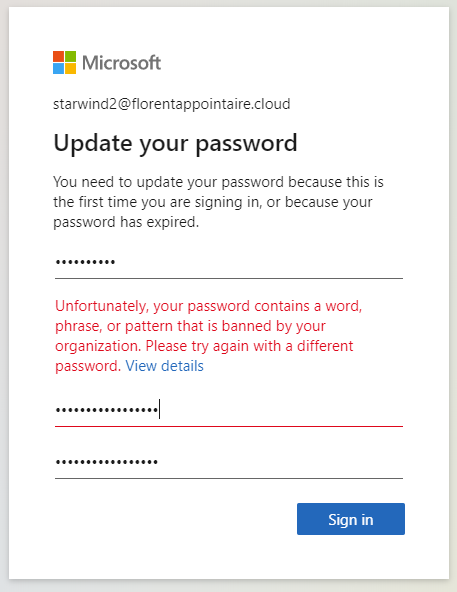
This feature, is very helpful to manage weak password in your company, with less efforts.




